IDPA: Security Vulnerability Scanning Detected TLS SSL Weak MACs Cipher Suites on Search
Summary: The article provides a workaround for "TLS/SSL Weak Message Authentication Code Cipher Suites for Ports 442, 443, and 445" detected on Search.
Instructions
When the following vulnerability is detected on the Integration Data Protection Appliance (IDPA) on the Search component, ports 442, 443, and 445 (see table).
| Vulnerability Title | Components | Service Port | Service Protocol | Vulnerability Severity Level |
Vulnerability Description | Vulnerability Proof |
|---|---|---|---|---|---|---|
| TLS SSL Weak Message Authentication Code Cipher Suites | Search | 442 | TCP | 4 | Transport Layer Security version 1.2 and earlier include support for cipher suites which use cryptographically weak Hash-based message authentication codes (HMACs), such as MD5 or SHA1. | Negotiated with the following insecure cipher suites: TLS 1.2 ciphers:
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
|
| TLS SSL Weak Message Authentication Code Cipher Suites | Search | 443 | TCP | 4 | Transport Layer Security version 1.2 and earlier include support for cipher suites which use cryptographically weak Hash-based message authentication codes (HMACs), such as MD5 or SHA1. |
Negotiated with the following insecure cipher suites: TLS 1.2 ciphers:
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
|
| TLS SSL Weak Message Authentication Code Cipher Suites | Search | 445 | TCP | 4 | Transport Layer Security version 1.2 and earlier include support for cipher suites which use cryptographically weak Hash-based message authentication codes (HMACs), such as MD5 or SHA1. |
Negotiated with the following insecure cipher suites: TLS 1.2 ciphers: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
|
Follow these steps to mitigate the issue:
- Open a PuTTY session to the Search index control node and log in as the 'root' user.
- Change the working directory to "/etc/nginx" using the following command:
cd /etc/nginx
- Confirm that the "nginx.cis.conf" and "nginx.search.conf" files exist in the directory:
Search:/etc/nginx #ls -la total 96 drwxr-xr-x 2 root root 4096 Jun 5 11:42 . drwxr-xr-x 92 root root 4096 Jul 18 11:51 .. -rw-r--r-- 1 root root 1077 Apr 19 14:48 fastcgi.conf -rw-r--r-- 1 root root 1077 Apr 19 14:48 fastcgi.conf.default -rw-r--r-- 1 root root 1007 Apr 19 14:48 fastcgi_params -rw-r--r-- 1 root root 1007 Apr 19 14:48 fastcgi_params.default -rw-r--r-- 1 root root 2837 Apr 19 14:48 koi-utf -rw-r--r-- 1 root root 2223 Apr 19 14:48 koi-win -rw-r--r-- 1 root root 5349 Apr 19 14:48 mime.types -rw-r--r-- 1 root root 5349 Apr 19 14:48 mime.types.default -rw-r--r-- 1 root root 1021 Jun 5 11:42 nginx.avamar-action.conf -rw-r--r-- 1 root root 3086 Jun 5 11:39 nginx.cis.conf -rw-r--r-- 1 root root 548 Jun 5 11:42 nginx.conf -rw-r--r-- 1 root root 2656 Apr 19 14:48 nginx.conf.default -rw-r--r-- 1 root root 548 Jun 5 11:42 nginx.conf.tmp -rw-r--r-- 1 root root 1027 Jun 5 11:42 nginx.networker-action.conf -rw-r--r-- 1 root root 2513 Jun 5 11:42 nginx.search.conf -rw-r--r-- 1 root root 636 Apr 19 14:48 scgi_params -rw-r--r-- 1 root root 636 Apr 19 14:48 scgi_params.default -rw-r--r-- 1 root root 664 Apr 19 14:48 uwsgi_params -rw-r--r-- 1 root root 664 Apr 19 14:48 uwsgi_params.default -rw-r--r-- 1 root root 3610 Apr 19 14:48 win-utf Search:/etc/nginx #
- Make a copy of the current "nginx.cis.conf" and "nginx.search.conf" files:
cp nginx.cis.conf nginx.cis.conf.default cp nginx.search.conf nginx.search.conf.default
- Update the ssl_ciphers on "nginx.cis.conf" and "nginx.search.conf" files:
From: ssl_ciphers 'kEECDH+ECDSA+AES128 kEECDH+ECDSA+AES256 kEECDH+AES128 kEECDH+AES256 kEDH+AES128 kEDH+AES256 +SHA !aNULL !eNULL !LOW !kECDH !DSS !MD5 !EXP !PSK !SRP !CAMELLIA !SEED !DES'; To: ssl_ciphers 'kEECDH+ECDSA+AES128 kEECDH+ECDSA+AES256 kEECDH+AES128 kEECDH+AES256 kEDH+AES128 kEDH+AES256 !SHA1 !aNULL !eNULL !LOW !kECDH !DSS !MD5 !EXP !PSK !SRP !CAMELLIA !SEED !DES';
There are two entries in "nginx.cis.conf" as shown below:
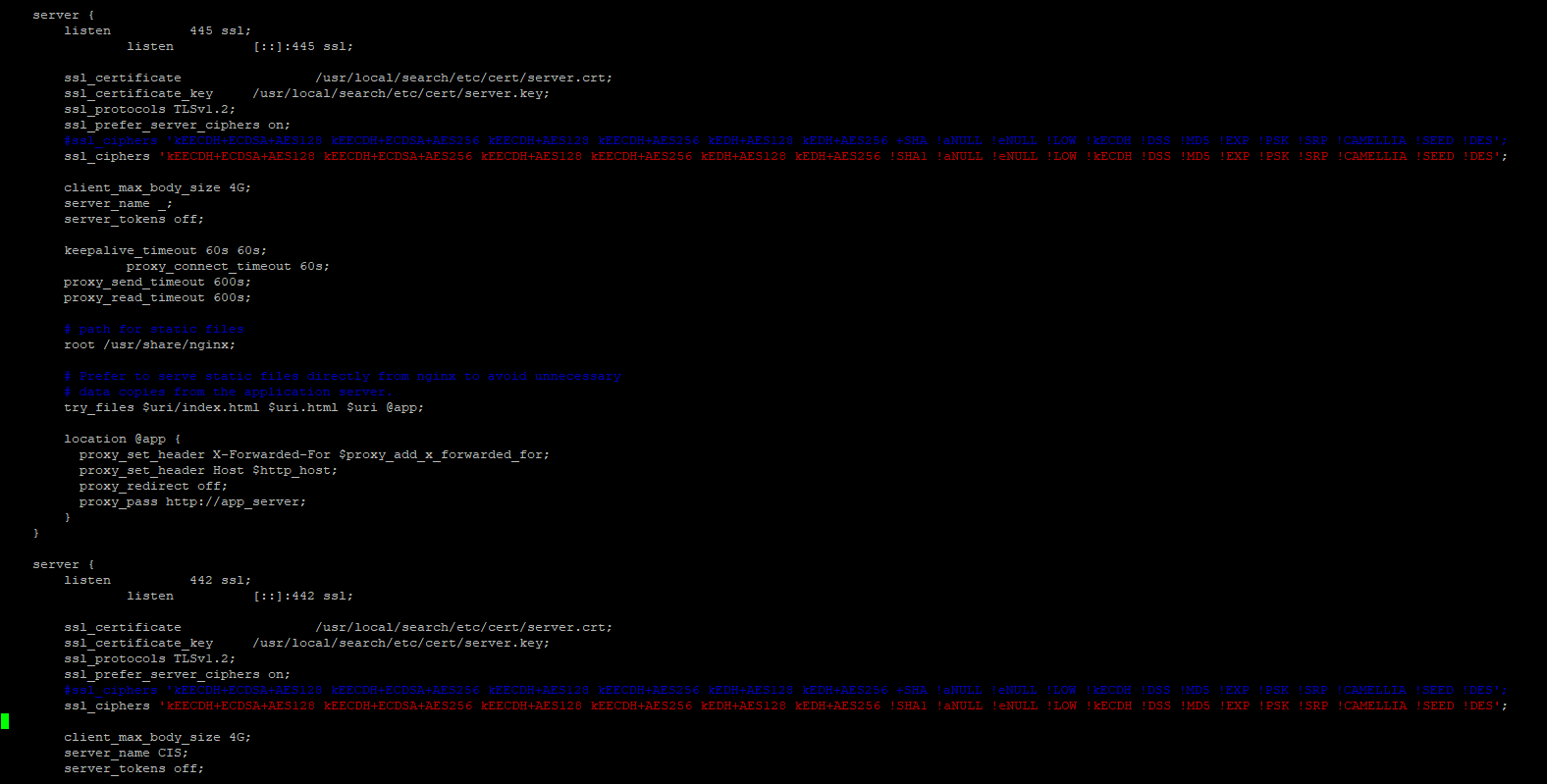
Figure 1: Screenshot of nginx.cis.conf file
There is one entry in "nginx.search.conf" as shown below:
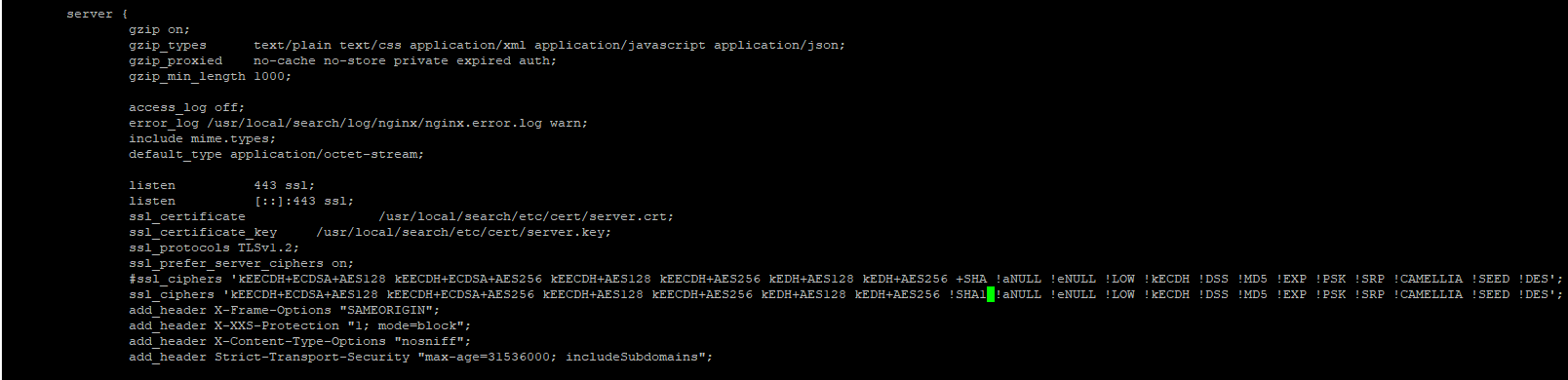
Figure 2: Screenshot of nginx.search.conf file
- Reboot the Search server.
systemctl reboot
- The "TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA and TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA" should be removed from the cipher list.
PORT STATE SERVICE VERSION 442/tcp open ssl/http nginx | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | compressors: | NULL | cipher preference: server |_ least strength: A 443/tcp open ssl/http nginx | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | compressors: | NULL | cipher preference: server |_ least strength: A 445/tcp open ssl/http nginx | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | compressors: | NULL | cipher preference: server |_ least strength: A
Additional Information
The Security Vulnerability scanning detects "TLS SSL Weak Message Authentication Code Cipher Suites" for port 30002 on Search as well.
| Vulnerability Title | Components | Service Port | Service Protocol | Vulnerability Severity Level |
Vulnerability Description | Vulnerability Proof |
|---|---|---|---|---|---|---|
| TLS SSL Weak Message Authentication Code Cipher Suites | Search | 30002 | TCP | 4 | Transport Layer Security version 1.2 and earlier include support for cipher suites which use cryptographically weak Hash-based message authentication codes (HMACs), such as MD5 or SHA1. |
Negotiated with the following insecure cipher suites: TLS 1.2 ciphers: |
The cipher suites for Port 30002 are planned to be updated after Avamar is updated in the upcoming Integration Data Protection Appliance major release.
Before implementing the workaround, the ports 442, 443, 445, and 30002 scanning results would be similar to this:
Search:~ #nmap -sV --script ssl-enum-ciphers -p 442,443,445,30002 localhost -Pn Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-31 14:27 GMT-10 Nmap scan report for localhost (127.0.0.1) Host is up (0.000041s latency). Other addresses for localhost (not scanned): ::1 PORT STATE SERVICE VERSION 442/tcp open ssl/http nginx | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | compressors: | NULL | cipher preference: server |_ least strength: A 443/tcp open ssl/http nginx | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | compressors: | NULL | cipher preference: server |_ least strength: A 445/tcp open ssl/http nginx | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | compressors: | NULL | cipher preference: server |_ least strength: A 30002/tcp open ssl/pago-services2? | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp384r1) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 3072) - A | compressors: | NULL | cipher preference: client |_ least strength: A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.44 seconds Search:~ #