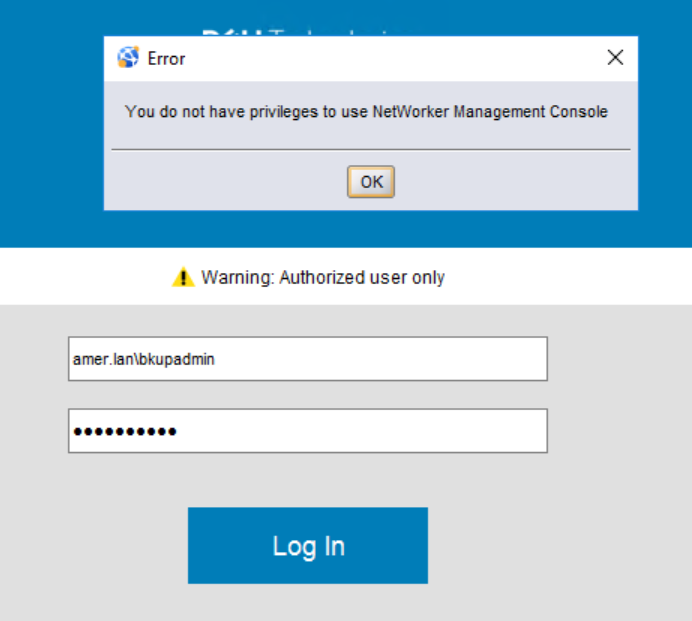
NMC: AD/LDAP login fails "You do not have privileges to use NetWorker Management Console"
Summary: External authentication (AD or LDAP) is integrated with NetWorker. Logging in to the NetWorker Management Console (NMC) as an external account returns the error "You do not have privileges to use NetWorker Management Console." ...
Symptoms
- External authentication (Microsoft Active Directory (AD) or LDAP (OpenLDAP) has been successfully added to the NetWorker server's authentication server service.
- When attempting to log In to the NetWorker Management Console (NMC) with an AD or LDAP account, an error box appears stating "You do not have privileges to use NetWorker Management Console"
Cause
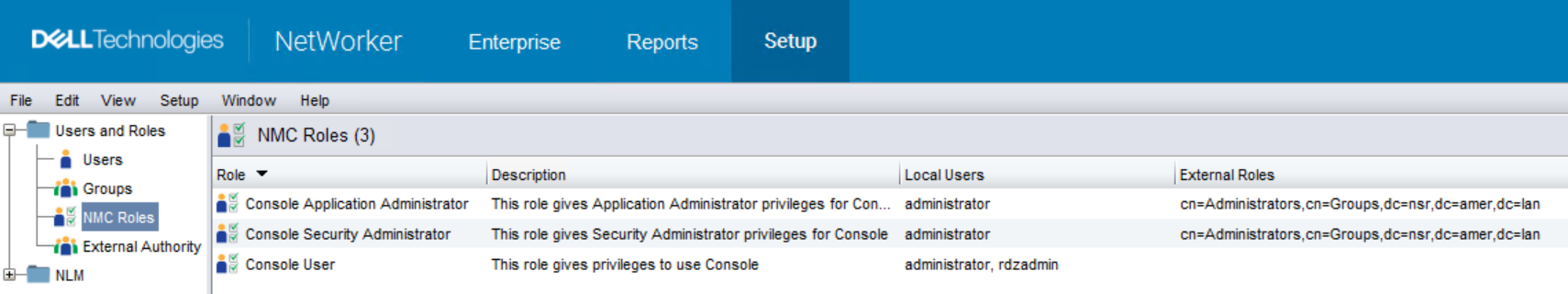
- Console Application Administrators: Gives the user/group access to log in to the NMC and run NMC Reports. Users or groups with Application Administrators privileges access can change the NMC Enterprise configuration.
- Console Security Administrators: Gives the user/group access to change user settings and groups in the NMC Enterprise configuration.
- Console Users: Gives the user/group access to log in to the NMC and run NMC Reports; however, the user cannot change the NMC Enterprise settings or access security information.
The symptom in this KB appears when:
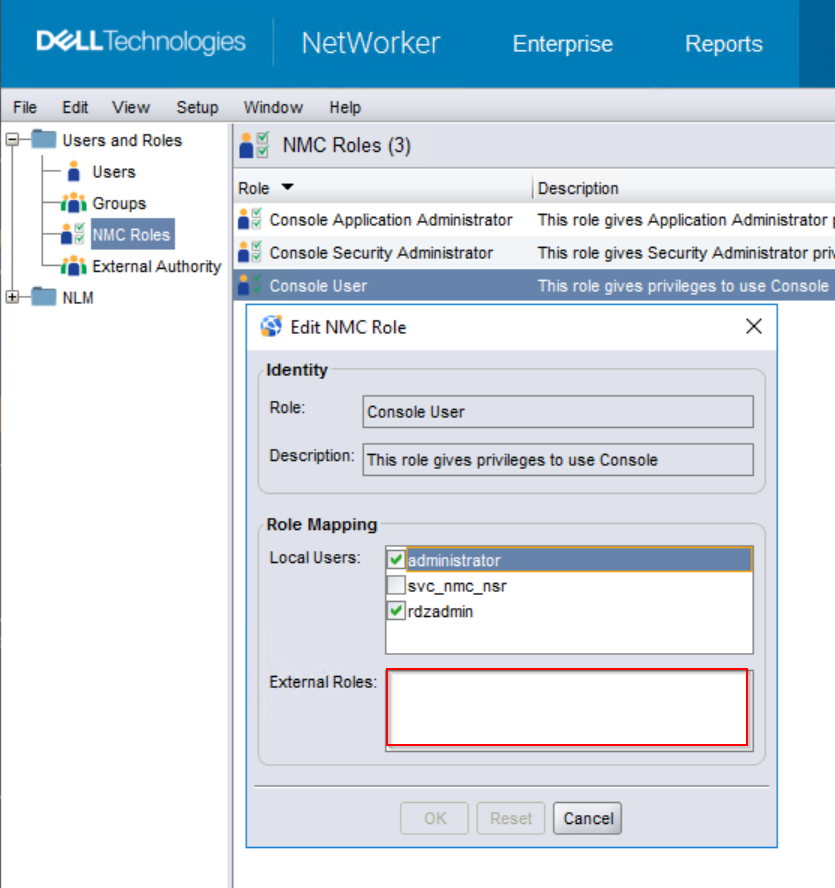
- The AD/LDAP user or group Distinguished-Name (DN) was not specified in the external roles field of either Console Application Administrators or Console Users groups.
- The AD/LDAP user does not belong to an AD/LDAP group which is defined in the external roles field of either the Console Application Administrators or Console Users groups.
Resolution
1. Determine which host is the NetWorker Authentication (AUTHC) server.
- On the NetWorker Management Console (NMC) server, open the
gstd.conffile.
Linux: /opt/lgtonmc/etc/gstd.conf
Windows (Default): C:\Program Files\EMC NetWorker\Management\GST\etc\gstd.conf
- The gstd.conf file contains a authsvc_hostname string, which defines the hostname and port used for processing login requests in the NMC:
string authsvc_hostname = "lnx-nwserv.amer.lan";
int authsvc_port = 9090;
2. Open an elevated prompt on the AUTHC server, determine which AD group the user belongs to:
The following methods can be used:
NetWorker Method:
authc_mgmt command to query which AD groups a user belongs to:
authc_mgmt -u Administrator -p 'NMC_ADMIN_PASS' -e query-ldap-groups-for-user -D query-tenant=TENANT_NAME -D query-domain=DOMAIN_NAME -D user-name=AD_USERNAME
- You can get the tenant name with:
authc_config -u Administrator -p 'NMC_ADMIN_PASS' -e find-all-tenants
- You can get the domain name with:
authc_config -u Administrator -p 'NMC_ADMIN_PASS' -e find-all-configs
authc_config -u Administrator -p 'NMC_ADMIN_PASS' -e find-config -D config-id=CONFIG_ID
[root@lnx-nwserv]:~# authc_config -u Administrator -p '!Password1' -e find-all-tenants
The query returns 1 records.
Tenant Id Tenant Name
1 default
[root@lnx-nwserv]:~# authc_config -u Administrator -p '!Password1' -e find-all-configs
The query returns 1 records.
Config Id Config Name
1 amer_ad
[root@lnx-nwserv]:~# authc_config -u Administrator -p '!Password1' -e find-config -D config-id=1
Config Id : 1
Config Tenant Id : 1
Config Name : amer_ad
Config Domain : amer.lan
Config Server Address : ldaps://dc.amer.lan:636/dc=amer,dc=lan
Config User DN : CN=Administrator,CN=Users,dc=amer,dc=lan
Config User Group Attribute :
Config User ID Attribute : sAMAccountName
Config User Object Class : person
Config User Search Filter :
Config User Search Path :
Config Group Member Attribute: member
Config Group Name Attribute : cn
Config Group Object Class : group
Config Group Search Filter :
Config Group Search Path :
Config Object Class : objectclass
Is Active Directory : true
Config Search Subtree : true
[root@lnx-nwserv]:~# authc_mgmt -u Administrator -p '!Password1' -e query-ldap-groups-for-user -D query-tenant=default -D query-domain=amer.lan -D user-name=bkupadmin
The query returns 1 records.
Group Name Full Dn Name
NetWorker_Admins CN=NetWorker_Admins,DC=amer,DC=lan
Get-ADPrincipalGroupMembership AD_USERNAME
PS C:\Users\Administrator> Get-ADPrincipalGroupMembership bkupadmin
distinguishedName : CN=NetWorker_Admins,DC=amer,DC=lan
GroupCategory : Security
GroupScope : Global
name : NetWorker_Admins
objectClass : group
objectGUID : c5c1bb45-88b4-4baa-afc3-9f1c28605d4a
SamAccountName : NetWorker_Admins
SID : S-1-5-21-3150365795-1515931945-3124253046-9611
distinguishedName : CN=Domain Users,CN=Users,DC=amer,DC=lan
GroupCategory : Security
GroupScope : Global
name : Domain Users
objectClass : group
objectGUID : 5c648708-a9ee-483c-b92d-bc37e93280f4
SamAccountName : Domain Users
SID : S-1-5-21-3150365795-1515931945-3124253046-513
3. Log in to the NMC as the default NetWorker Administrator account.
b. Open the NMC Users role and specify the AD groups distinguished name in the External Roles field:
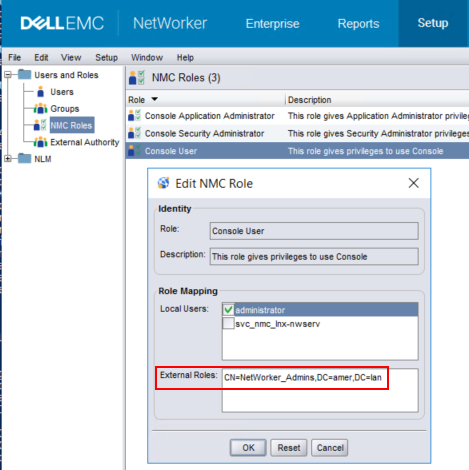
"cn=Administrators,cn=Groups,dc=NETWORKER_SERVER_HOSTNAME,dc=DOMAIN_COMPONENT1,dc=DOMAIN_COMPONENT2." Do not remove these.
4. Before disconnecting from the NMC, also confirm if the AD group has been defined in a NetWorker server User Group. If the user lacks NetWorker server permissions, they can log in to NMC but will not see jobs or resources after connecting to the server.
a. While still logged in to the NMC as the default NetWorker Administrator, connect to the NetWorker server.
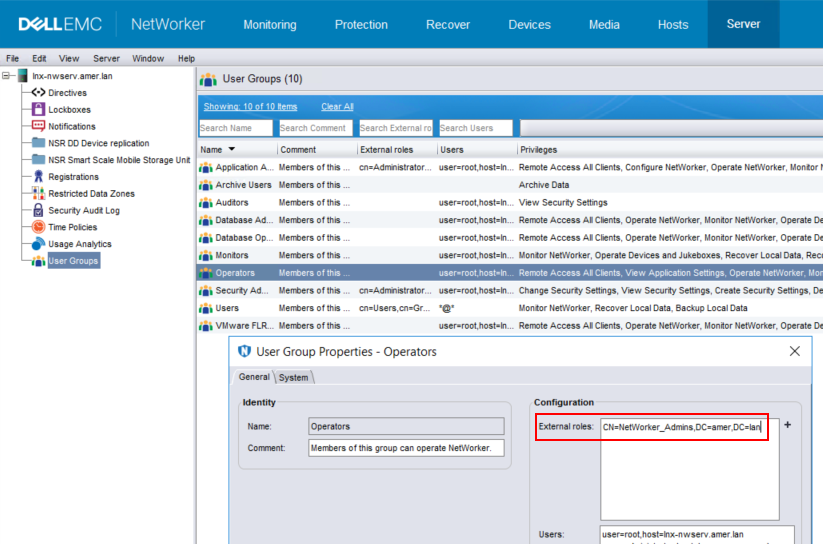
b. Got to Server->Users and Groups.
c. Open the User Group which has the permissions you want applied to the AD group.
d. In the External Roles field, append the AD group's distinguished name:
5. Attempt to log in to the NMC using the AD/LDAP user account:

b. Using the AD group DN you want to grant
FULL_CONTROL permission to run:
authc_config -u Administrator -p 'NMC_ADMIN_PASS' -e add-permission -D permission-name=FULL_CONTROL -D permission-group-dn="AD_GROUP_DN"
[root@lnx-nwserv]:~# authc_config -u Administrator -p '!Password1' -e add-permission -D permission-name=FULL_CONTROL -D permission-group-dn="CN=NetWorker_Admins,DC=amer,DC=lan"
Permission FULL_CONTROL is created successfully.
[root@lnx-nwserv]:~# authc_config -u Administrator -p '!Password1' -e find-all-permissions
The query returns 2 records.
Permission Id Permission Name Group DN Pattern Group DN
1 FULL_CONTROL ^cn=Administrators,cn=Groups.*$
2 FULL_CONTROL CN=NetWorker_Admins,dc=amer,dc=lan