PowerFlex: Error "Certificates Do Not Conform To Algorithm Constraint" When Trying To Register System With Secure Remote Services (SRS)
Summary: Unable to register PowerFlex system with Secure Remote Services using IM Gateway's "FOSGWTool.sh"
Symptoms
This issue can occur when the IM Gateway certificate is not self-signed, rather signed by a third-party CA authority. The CA certificates are already imported into the IM Gateway truststore, as per PowerFlex documentation.
Symptoms
Secure Remote Services registration attempt throws the following error:
# /opt/emc/scaleio/gateway/bin/FOSGWTool.sh --register_esrs_gateway --scaleio_gateway_ip $gw_ip --scaleio_gateway_user admin --scaleio_gateway_password $gw_pass --esrs_gateway_ip $esrs_hostname --connect_in_ip $gw_ip --esrs_gateway_user $esrs_user --esrs_gateway_password <PASSWORD>
Exception in thread "main" org.springframework.web.client.ResourceAccessException: I/O error on GET request for "https://10.10.10.11/api/gatewayLogin": java.security.cert.CertificateException: Certificates do not conform to algorithm constraints; nested exception is javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: Certificates do not conform to algorithm constraints
at org.springframework.web.client.RestTemplate.doExecute(RestTemplate.java:525)
at org.springframework.web.client.RestTemplate.execute(RestTemplate.java:473)
at org.springframework.web.client.RestTemplate.exchange(RestTemplate.java:421)
at com.emc.s3g.scaleio.installation.cli.SioGWTool.loginToRestGateway(SioGWTool.java:2563)
at com.emc.s3g.scaleio.installation.cli.SioGWTool.main(SioGWTool.java:1754)
Caused by: javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: Certificates do not conform to algorithm constraints
at sun.security.ssl.Alert.createSSLException(Alert.java:131)
at sun.security.ssl.TransportContext.fatal(TransportContext.java:370)
at sun.security.ssl.TransportContext.fatal(TransportContext.java:313)
at sun.security.ssl.TransportContext.fatal(TransportContext.java:308)
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.checkServerCerts(CertificateMessage.java:652)
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.onCertificate(CertificateMessage.java:471)
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.consume(CertificateMessage.java:367)
at sun.security.ssl.SSLHandshake.consume(SSLHandshake.java:376)
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:479)
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:457)
at sun.security.ssl.TransportContext.dispatch(TransportContext.java:200)
at sun.security.ssl.SSLTransport.decode(SSLTransport.java:154)
at sun.security.ssl.SSLSocketImpl.decode(SSLSocketImpl.java:1290)
at sun.security.ssl.SSLSocketImpl.readHandshakeRecord(SSLSocketImpl.java:1199)
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:401)
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:373)
at sun.net.www.protocol.https.HttpsClient.afterConnect(HttpsClient.java:587)
at sun.net.www.protocol.https.AbstractDelegateHttpsURLConnection.connect(AbstractDelegateHttpsURLConnection.java:197)
at sun.net.www.protocol.https.HttpsURLConnectionImpl.connect(HttpsURLConnectionImpl.java:167)
at org.springframework.http.client.SimpleBufferingClientHttpRequest.executeInternal(SimpleBufferingClientHttpRequest.java:76)
at org.springframework.http.client.AbstractBufferingClientHttpRequest.executeInternal(AbstractBufferingClientHttpRequest.java:48)
at org.springframework.http.client.AbstractClientHttpRequest.execute(AbstractClientHttpRequest.java:49)
at org.springframework.web.client.RestTemplate.doExecute(RestTemplate.java:510)
... 4 more
Caused by: java.security.cert.CertificateException: Certificates do not conform to algorithm constraints
at sun.security.ssl.AbstractTrustManagerWrapper.checkAlgorithmConstraints(SSLContextImpl.java:1387)
at sun.security.ssl.AbstractTrustManagerWrapper.checkAdditionalTrust(SSLContextImpl.java:1312)
at sun.security.ssl.AbstractTrustManagerWrapper.checkServerTrusted(SSLContextImpl.java:1256)
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.checkServerCerts(CertificateMessage.java:636)
... 22 more
Caused by: java.security.cert.CertPathValidatorException: Algorithm constraints check failed on signature algorithm: SHA1withRSA < =============================== this is an issue
at sun.security.provider.certpath.AlgorithmChecker.check(AlgorithmChecker.java:237)
at sun.security.ssl.AbstractTrustManagerWrapper.checkAlgorithmConstraints(SSLContextImpl.java:1383)
... 25 moreImpact
Unable to register PowerFlex system with Secure Remote Services.
Cause
The IM Gateway certificate was signed by an old CA certificate using SHA1 as the signature hash algorithm. By default, Java does not allow SHA1 and few other older algorithms to be used in the certificate path due to potential security issues.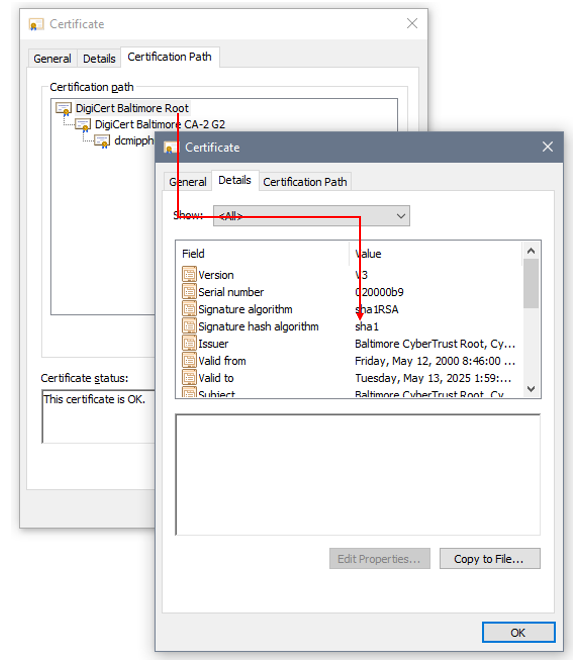
Resolution
As a workaround, Java can be configured to temporarily accept old types of hashing algorithms - edit the java.security file and comment out the lines corresponding with the "jdk.certpath.disabledAlgorithms" entry:
#
jdk.certpath.disabledAlgorithms=MD2, MD5, SHA1 jdkCA & usage TLSServer, \
RSA keySize < 1024, DSA keySize < 1024, EC keySize < 224For a permanent solution sign the IM Gateway certificate with CA using modern and secure hashing algorithms