PowerVault ME4:安裝與移除自訂憑證
Summary: 本文說明透過 FTP 為 Dell PowerVault ME 系列儲存產品安裝自訂憑證的步驟。
Instructions
在 ME4 上安裝或移除自訂憑證
安裝憑證。
請執行下列步驟以安裝第三方或自我簽署安全性憑證:
-
在 PowerVault Manager 中,準備使用 FTP 或安全檔案傳輸通訊協定 (SFTP):
-
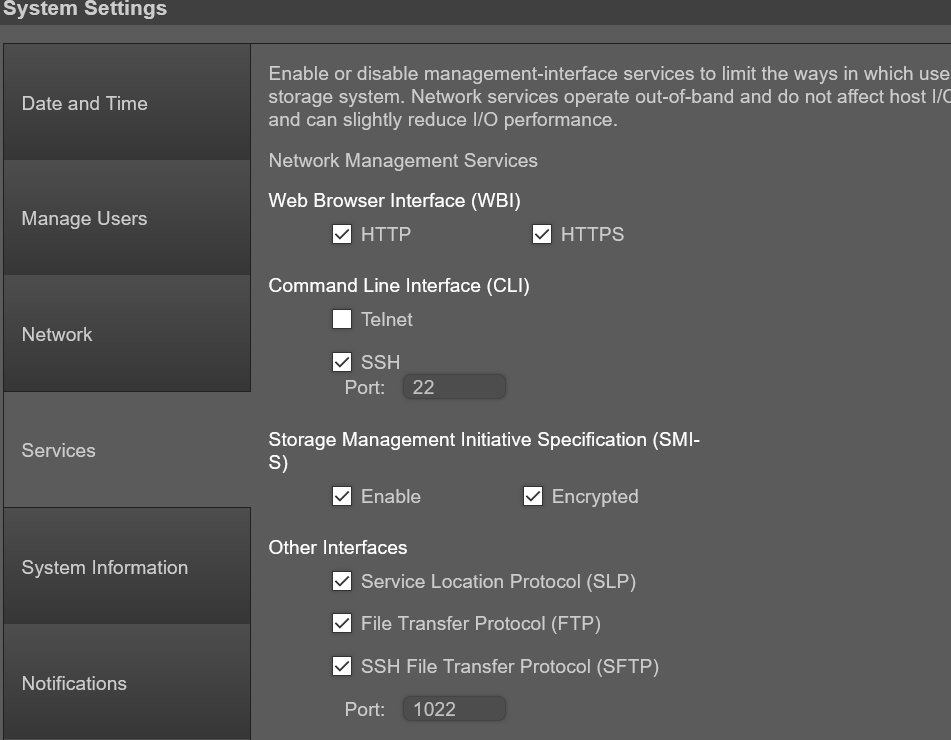
在 ME4 系統設定 > 網路下,判斷控制器的網路連接埠 IP 位址。
-
確認在 ME4 系統設定 > 服務下的儲存裝置上已啟用 FTP 或 SFTP 服務。如果使用 SFTP,請記錄設置為使用哪個埠 SFTP。
-
-
ME4:「系統設定 > :管理使用者」可用來驗證使用者帳戶是否具有「管理」和「FTP/SFTP」角色。
-
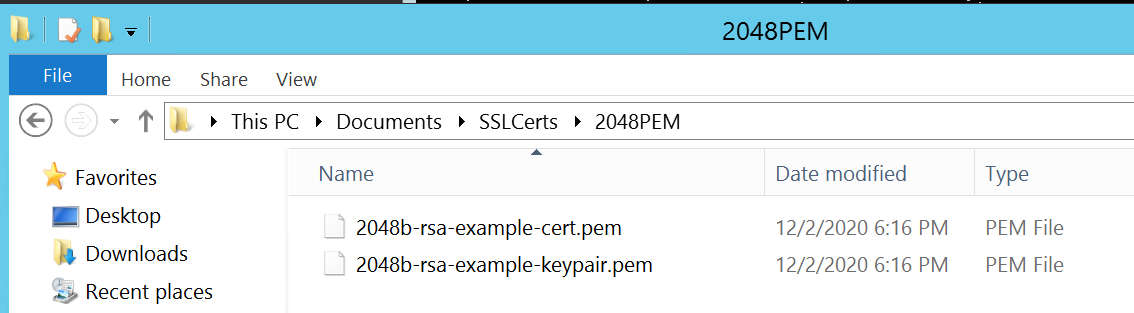
將證書檔和金鑰檔放在 FTP 用戶端可存取的目錄中。憑證和金鑰檔案的格式必須為隱私增強型郵件 (PEM) 格式。客戶可以上傳可分辨編碼規則 (DER) 檔案,但在控制器上重新啟動管理時無法使用這些規則。注意:ME4 支援萬用字元憑證。
-
開啟命令提示字元 (Windows) 或終端機視窗 (UNIX),然後前往包含認證檔案的目錄。UI 不能像 Filezilla 用戶端那樣使用,因為「put」行需要檔名後的命令參數。
如果啟用防火牆,Windows FTP 將無法執行被動 FTP。它也許能夠登入 ME4 陣列,但在嘗試傳送檔案時出現連接埠連線問題。如果嘗試使用 Windows 命令列 FTP,在開始前必須停用 Windows 防火牆。)
-
輸入:
sftp controller-network-address -P port or ftp controller-network-address。檔案必須上傳到兩個控制器,才能在兩個控制器上使用。
例如: sftp 10.235.XXX.XXX -P 1022 or ftp 10.X.0.X X。
以具有管理角色權限和 FTP 或 SFTP 介面權限的使用者身分登入。在這些範例中,會使用 WinSCP FTP 命令列用戶端,但如果停用 Windows 防火牆,則可使用 Windows FTP 用戶端。亦可使用 Linux 用戶端。
C:\Users\Administrator\Documents\SSLCerts\2048PEM>"c:\Program Files (x86)\WinSCP\WinSCP.com"
winscp> open ftp://100.85.XXX.X
Prompting for credentials...
Username: manage
Connecting to 100.85.XXX.X ...
Password:
Connected
Starting the session...
Session started.
Active session: [1] 100.85.XXX.X
winscp>
-
輸入:
put certificate-file-name cert-file其中,認證檔案名稱 是特定儲存裝置的認證檔案名稱。如果證書放入的目錄是 FTP 用戶無權修改的隱藏目錄,則可能會發生檔錯誤。
winscp> put 2048b-rsa-example-cert.pem cert-file
2048b-rsa-example-cert.pe | 1 KB | 0.0 KB/s | binary | 100%
winscp>
-
輸入:
put key-file-name cert-key-file其中,金鑰檔名 是特定儲存裝置的安全金鑰檔案名稱。
winscp> put 2048b-rsa-example-keypair.pem cert-key-file
2048b-rsa-example-keypair | 1 KB | 0.0 KB/s | binary | 100%
winscp>
-
請注意,如果在上傳這些檔案後在陣列 FTP 網站上完成目錄清單,則不會顯示這些目錄。它們存儲在FTP用戶無法查看的隱藏目錄中。
winscp> ls
D--------- 0 0 ..
Lrwxrwxrwx 0 0 0 12 Dec 2 13:19:33 2020 .banner ->
-rw-rw-rw- 0 0 10 0 Dec 2 14:46:49 2020 0
-rw-r--r-- 0 0 0 8436 Dec 2 13:19:33 2020 README
winscp>
-
對其他控制器重複步驟 4、5、6 和 7。
-
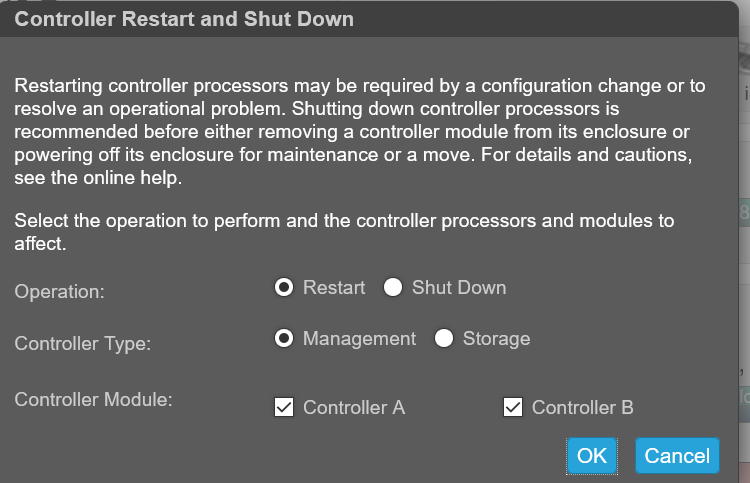
重新啟動兩個管理控制器,讓新的安全性憑證生效。管理控制器重新開機後,可透過如下所示的 UI 或透過 SSH 命令「show certificate」檢視憑證。
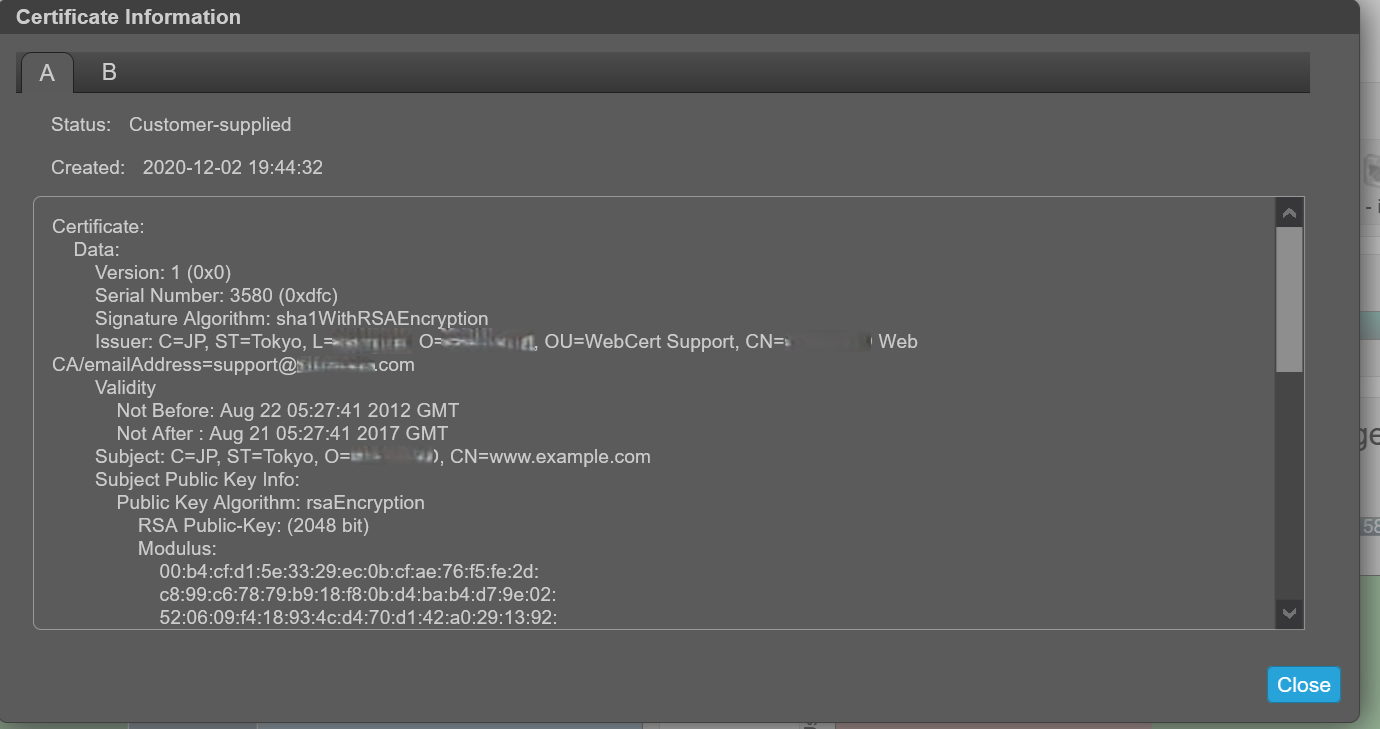
檢視憑證資訊。
默認情況下,存儲為每個控制器生成唯一的 SSL 證書。為了獲得最強的安全性,請將預設系統生成的證書替換為受信任的證書頒發機構頒發的證書。
憑證資訊面板顯示系統上每個控制器儲存的使用中 SSL 憑證資訊。選項卡 A 和 B 包含每個相應控制器的未格式化證書文本。該面板還顯示以下狀態值之一以及每個憑證的建立日期:
-
客戶提供 - 表示控制器使用客戶已上傳的憑證。
-
系統產生 - 表示控制器使用控制器產生的作用中憑證和金鑰。
-
未知狀態 - 表示無法讀取控制器的證書。當控制器正在重新啟動、證書替換過程仍在進行中或使用者已為單控制器系統中的合作控制器選擇了選項卡時,最常發生這種情況。
若要使用自訂憑證,請透過 FTP 或 SFTP 上傳,或使用建立憑證 CLI 命令的內容參數。這允許使用者使用自己的唯一證書內容創建證書。若要使新憑證生效,請為其重新啟動管理控制器。
確認憑證更換成功,且控制器使用的是提供的憑證:
- 確認憑證狀態為「客戶供應」
- 建立日期正確
- 憑證內容為預期文字
檢視憑證資訊:
-
在橫幅中,按一下系統面板,然後選取顯示憑證資訊。憑證資訊面板隨即開啟。
-
檢視憑證資訊完成後,按一下關閉。
在安裝憑證之前,資訊會顯示「系統已產生」。
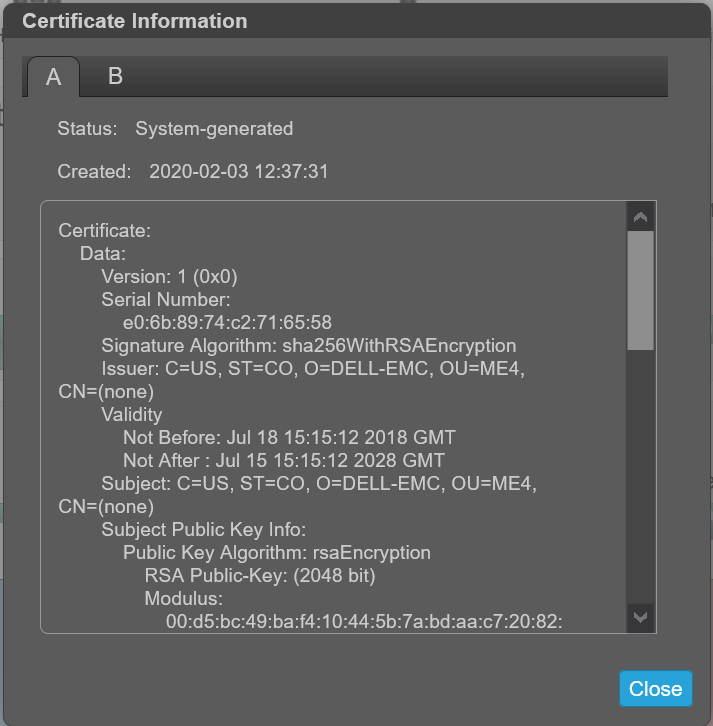
安裝您自己的憑證後,憑證會識別為「客戶供應」:
移除自訂憑證。
若要還原系統產生的憑證,並移除兩個控制器的自訂憑證,請登入每個控制器並執行命令:# create certificate restore
若要使憑證變更生效,請在所有使用該命令的控制器上重新啟動管理控制器。
僅 CLI 範例,使用 Linux 和 ME4 SSH 工作階段
-
建立憑證並將「PEM .cer」和「.key」放入 Linux 機器上
-
從 Linux 方塊上的 SSH 工作階段,使用 FTP 將檔案傳輸到陣列,然後開啟連接至陣列的 SSH 工作階段,以重新啟動 ME4 上的兩個控制器。重新啟動 ME4 管理控制器後,使用者大約需要兩分鐘才能重新登入 ME4 並顯示新憑證。注意:一個控制器可能需要比另一個更長的時間才能啟動。在兩個控制器都完全啟動之前,儲存裝置可能會在系統憑證上顯示一個控制器,在客戶憑證上顯示另一個控制器。
在以下範例中,ME4 控制器 IP 為:
A: 100.85.XXX.X
B: 100.85.XXX.XX8
若要讓兩個控制器都具有憑證:
- 使用 FTP 將憑證和金鑰檔案上傳至兩個控制器
- 在兩個控制器上重新開機管理控制器
[grpadmin@WWWWWWW certs]$ pwd
/home/grpadmin/Documents/certs
[grpadmin@WWWWWWW certs]$ ls
2048b-rsa-example-cert.pem 2048b-rsa-example-keypair.pem put
[grpadmin@WWWWWWW certs]$ ftp 100.85.QQQ.ZZZ
Connected to 100.85.QQQ.ZZZ (100.85.QQQ.ZZZ).
220-Welcome to Pure-FTPd.
220-You are user number 1 of 5 allowed.
220-Local time is now 23:29. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (100.85.QQQ.ZZZ:grpadmin): manage
331 User manage OK. Password required
Password:
230-OK. Current restricted directory is /.
.
.
230-Instructions for loading security certificate files:
230- 1. The security certificate files will consist of a pair of files.
230- You will have a certificate file and a key file.
230- 2. Log in with a user name and password.
230- 3. Type 'put <certificate-file-name> cert-file'
230- where <certificate-file-name> is the name of the certificate file
230- for your specific system.
230- 4. Type 'put <key-file-name> cert-key-file'
230- where <key-file-name> is the name of the security key file for
230- your specific system.
230- 5. Restart both Management Controllers to have the new security
230- certificate take effect.
230-
230
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put 2048b-rsa-example-cert.pem cert-file
local: 2048b-rsa-example-cert.pem remote: cert-file
227 Entering Passive Mode (100,85,QQQ,ZZZ,127,0)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-10 17:40:12)
STATUS: Loading security certificate file
226-
226 Operation Complete. (2020-12-10 17:40:18)
1050 bytes sent in 9.4e-05 secs (11170.21 Kbytes/sec)
ftp> put 2048b-rsa-example-keypair.pem cert-key-file
local: 2048b-rsa-example-keypair.pem remote: cert-key-file
227 Entering Passive Mode (100,85,QQQ,ZZZ,204,57)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-10 17:40:37)
STATUS: Loading security certificate file
Verifying uploaded certificate and key.
The uploaded SSL certificate and key have been installed. Reboot the controller to apply.
226-
226 Operation Complete. (2020-12-10 17:40:45)
1679 bytes sent in 8.5e-05 secs (19752.94 Kbytes/sec)
ftp> ls
227 Entering Passive Mode (100,85,QQQ,ZZZ,189,193)
150 Accepted data connection
-rw-rw-rw- 1 0 users 0 Dec 10 17:40 0
-rw-r--r-- 1 0 0 8436 Dec 2 20:39 README
226-Options: -l
226 2 matches total
ftp> bye
221-Goodbye. You uploaded 3 and downloaded 0 kbytes.
221 Logout.
[grpadmin@WWWWWWW certs]$ ftp 100.85.XXX.YYY
Connected to 100.85.XXX.YYY (100.85.XXX.YYY).
220-Welcome to Pure-FTPd.
220-You are user number 1 of 5 allowed.
220-Local time is now 23:30. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (100.85.XXX.YYY:grpadmin): manage
331 User manage OK. Password required
Password:
230-OK. Current restricted directory is /
.
.
.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put 2048b-rsa-example-cert.pem cert-file
local: 2048b-rsa-example-cert.pem remote: cert-file
227 Entering Passive Mode (100,85,XXX,YYY,126,144)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-11 23:30:22)
STATUS: Loading security certificate file
226-
226 Operation Complete. (2020-12-11 23:30:28)
1050 bytes sent in 4.7e-05 secs (22340.42 Kbytes/sec)
ftp> put 2048b-rsa-example-keypair.pem cert-key-file
local: 2048b-rsa-example-keypair.pem remote: cert-key-file
227 Entering Passive Mode (100,85,XXX,YYY,200,227)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-11 23:30:40)
STATUS: Loading security certificate file
Verifying uploaded certificate and key.
The uploaded SSL certificate and key have been installed. Reboot the controller to apply.
226-
226 Operation Complete. (2020-12-11 23:30:47)
1679 bytes sent in 5.2e-05 secs (32288.46 Kbytes/sec)
ftp> bye
221-Goodbye. You uploaded 3 and downloaded 0 kbytes.
221 Logout.
[grpadmin@WWWWWWW certs]$ ssh manage@100.85.QQQ.ZZZ
Password:
DELL EMC ME4024
System Name: NDC-ME4
System Location: NDC
Version: GT280R008-01
# restart mc both
During the restart process you will briefly lose communication with the specified Management Controller(s).
Do you want to continue? (y/n) y
Info: Restarting the local MC (A)...
Success: Command completed successfully. - Both MCs were restarted. (2020-12-11 23:31:26)
# Killed
Connection to 100.85.QQQ.ZZZ closed.
.
. Will take about 2 minutes for you to be able to log back into the array to
. see the certificates
.
[grpadmin@WWWWWWW certs]$ ssh manage@100.85.QQQ.ZZZ
Password:
DELL EMC ME4024
System Name: NDC-ME4
System Location: NDC
Version: GT280R008-01
# show certificates
Error: The command was not recognized. (2020-12-11 23:36:35)
# show certificate
Certificate Status
------------------
Controller: A
Certificate Status: Customer-supplied
Time Created: 2020-12-11 23:29:29
Certificate Text: Certificate:
Data:
Version: 1 (0x0)
Serial Number: 3580 (0xdfc)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=JP, ST=Tokyo, L=RRRRRRR, O=SSSSSSSSS, OU=WebCert Support, CN=SSSSSSSSS Web CA/emailAddress=support@SSSSSSSSS.com
Validity
Not Before: Aug 22 05:27:41 2012 GMT
Not After : Aug 21 05:27:41 2017 GMT
Subject: C=JP, ST=Tokyo, O=SSSSSSSSS, CN=www.example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b4:cf:d1:5e:33:29:ec:0b:cf:ae:76:f5:fe:2d:
c8:99:c6:78:79:b9:18:f8:0b:d4:ba:b4:d7:9e:02:
52:06:09:f4:18:93:4c:d4:70:d1:42:a0:29:13:92:
73:50:77:f6:04:89:ac:03:2c:d6:f1:06:ab:ad:6c:
c0:d9:d5:a6:ab:ca:cd:5a:d2:56:26:51:e5:4b:08:
8a:af:cc:19:0f:25:34:90:b0:2a:29:41:0f:55:f1:
---REDACTED---
9a:24:79:49:17:27:d7:89:4b:6a:2e:0d:87:51:d9:
23:3d:06:85:56:f8:58:31:0e:ee:81:99:78:68:cd:
6e:44:7e:c9:da:8c:5a:7b:1c:bf:24:40:29:48:d1:
03:9c:ef:dc:ae:2a:5d:f8:f7:6a:c7:e9:bc:c5:b0:
59:f6:95:fc:16:cb:d8:9c:ed:c3:fc:12:90:93:78:
5a:75:b4:56:83:fa:fc:41:84:f6:64:79:34:35:1c:
ac:7a:85:0e:73:78:72:01:e7:24:89:25:9e:da:7f:
65:bc:af:87:93:19:8c:db:75:15:b6:e0:30:c7:08:
f8:59
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
40:cb:fe:04:5b:c6:74:c5:73:91:06:90:df:ff:b6:9e:85:73:
fe:e0:0a:6f:3a:44:2f:cc:53:73:16:32:3f:79:64:39:e8:78:
---REDACTED---
1b:d7:eb:c0:31:6c:86:a0:f6:55:a8:f8:10:d0:42:06:1e:94:
a5:e0:68:a7:9f:b6:f3:9c:d0:e1:22:3b:ab:85:3d:a1:27:9b:
50:32:62:b8:ec:7a:fa:d6:7d:2b:29:e6:ad:b2:69:4d:28:b4:
f8:13
Certificate Status
------------------
Controller: B Certificate Status: Customer-supplied
Time Created: 2020-12-11 23:30:22
Certificate Text: Certificate:
Data:
Version: 1 (0x0)
Serial Number: 3580 (0xdfc)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=JP, ST=Tokyo, L=RRRRRRR, O=SSSSSSSSS, OU=WebCert Support, CN=SSSSSSSSS Web CA/emailAddress=support@SSSSSSSSS.com
Validity
Not Before: Aug 22 05:27:41 2012 GMT
Not After : Aug 21 05:27:41 2017 GMT
Subject: C=JP, ST=Tokyo, O=SSSSSSSSS, CN=www.example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b4:cf:d1:5e:33:29:ec:0b:cf:ae:76:f5:fe:2d:
c8:99:c6:78:79:b9:18:f8:0b:d4:ba:b4:d7:9e:02:
52:06:09:f4:18:93:4c:d4:70:d1:42:a0:29:13:92:
73:50:77:f6:04:89:ac:03:2c:d6:f1:06:ab:ad:6c:
c0:d9:d5:a6:ab:ca:cd:5a:d2:56:26:51:e5:4b:08:
8a:af:cc:19:0f:25:34:90:b0:2a:29:41:0f:55:f1:
---REDACTED---
9a:24:79:49:17:27:d7:89:4b:6a:2e:0d:87:51:d9:
23:3d:06:85:56:f8:58:31:0e:ee:81:99:78:68:cd:
6e:44:7e:c9:da:8c:5a:7b:1c:bf:24:40:29:48:d1:
03:9c:ef:dc:ae:2a:5d:f8:f7:6a:c7:e9:bc:c5:b0:
59:f6:95:fc:16:cb:d8:9c:ed:c3:fc:12:90:93:78:
5a:75:b4:56:83:fa:fc:41:84:f6:64:79:34:35:1c:
ac:7a:85:0e:73:78:72:01:e7:24:89:25:9e:da:7f:
65:bc:af:87:93:19:8c:db:75:15:b6:e0:30:c7:08:
f8:59
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
40:cb:fe:04:5b:c6:74:c5:73:91:06:90:df:ff:b6:9e:85:73:
fe:e0:0a:6f:3a:44:2f:cc:53:73:16:32:3f:79:64:39:e8:78:
---REDACTED---
1b:d7:eb:c0:31:6c:86:a0:f6:55:a8:f8:10:d0:42:06:1e:94:
a5:e0:68:a7:9f:b6:f3:9c:d0:e1:22:3b:ab:85:3d:a1:27:9b:
50:32:62:b8:ec:7a:fa:d6:7d:2b:29:e6:ad:b2:69:4d:28:b4:
f8:13
Success: Command completed successfully. (2020-12-11 23:36:41)
#