PowerVault ME4:安装和删除自定义证书
Summary: 本文介绍通过 FTP 为 Dell PowerVault ME 系列存储产品安装自定义证书的步骤。
Instructions
在 ME4 上安装或删除自定义证书
安装证书。
执行以下步骤以安装第三方或自签名安全证书:
-
在 PowerVault Manager中,准备使用 FTP 或安全文件传输协议 (SFTP):
-
在ME4系统设置 > 网络下确定控制器的网络端口 IP 地址。
-
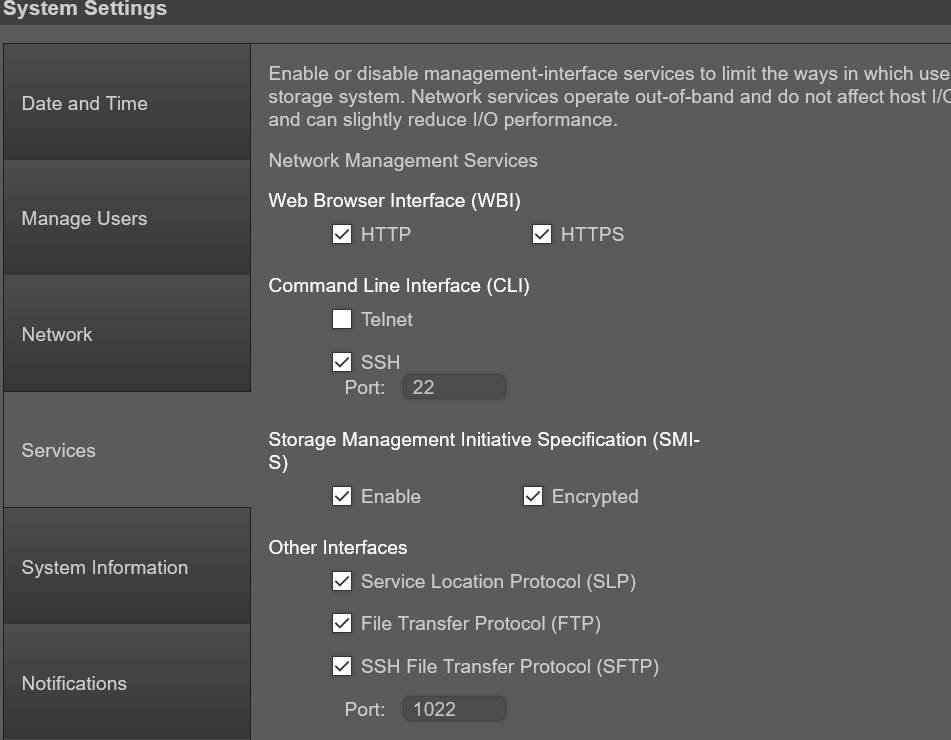
验证是否已在 ME4 System Settings > Services下的存储上启用 FTP 或 SFTP 服务。如果使用 SFTP,请记录设置为使用的 SFTP 端口。
-
-
ME4 系统设置 > Manage Users可用于验证用户帐户是否具有管理和 FTP/SFTP 角色。
-
将证书文件和密钥文件放在 FTP 客户端可访问的目录中。证书和密钥文件的格式必须是隐私增强邮件 (PEM) 格式。客户可以上传可分辨编码规则 (DER) 文件,但在控制器上重新启动管理时不能使用它们。提醒:ME4 支持通配符证书。

-
打开命令提示符 (Windows) 或终端窗口 (UNIX),然后转到包含证书文件的目录。UI 不能像 Filezilla 客户端那样使用,因为 “put” 行在文件名后需要命令参数。
如果启用了防火墙,Windows FTP 无法执行被动 FTP。它可能能够登录到 ME4 阵列,但在尝试发送文件时出现端口连接问题。如果尝试使用 Windows 命令行 FTP,则必须在启动之前禁用 Windows 防火墙。)
-
Type:
sftp controller-network-address -P port or ftp controller-network-address。必须将文件上传到两个控制器,才能在两个控制器上使用。
例如: sftp 10.235.XXX.XXX -P 1022 or ftp 10.X.0.X X。
以具有管理角色权限和 FTP 或 SFTP 接口权限的用户身份登录。在这些示例中,使用了 WinSCP FTP 命令行客户端,但如果禁用了 Windows 防火墙,则可以使用 Windows FTP 客户端。也可以使用 Linux 客户端。
C:\Users\Administrator\Documents\SSLCerts\2048PEM>"c:\Program Files (x86)\WinSCP\WinSCP.com"
winscp> open ftp://100.85.XXX.X
Prompting for credentials...
Username: manage
Connecting to 100.85.XXX.X ...
Password:
Connected
Starting the session...
Session started.
Active session: [1] 100.85.XXX.X
winscp>
-
Type:
put certificate-file-name cert-file其中,Certificate file name是特定存储单元的证书文件的名称。如果证书放入的目录是 FTP 用户无权修改的隐藏目录,则可能会发生文件错误。
winscp> put 2048b-rsa-example-cert.pem cert-file
2048b-rsa-example-cert.pe | 1 KB | 0.0 KB/s | binary | 100%
winscp>
-
Type:
put key-file-name cert-key-file其中 key-file-name是特定存储的安全密钥文件的名称。
winscp> put 2048b-rsa-example-keypair.pem cert-key-file
2048b-rsa-example-keypair | 1 KB | 0.0 KB/s | binary | 100%
winscp>
-
注意:如果在上传这些文件后在阵列 FTP 站点上列出目录,则不会看到这些文件。它们存储在 FTP 用户无法查看的隐藏目录中。
winscp> ls
D--------- 0 0 ..
Lrwxrwxrwx 0 0 0 12 Dec 2 13:19:33 2020 .banner ->
-rw-rw-rw- 0 0 10 0 Dec 2 14:46:49 2020 0
-rw-r--r-- 0 0 0 8436 Dec 2 13:19:33 2020 README
winscp>
-
对另一个控制器重复步骤 4、5、6 和 7。
-
重新启动两个管理控制器以使新的安全证书生效。在管理控制器重新启动后,可以通过如下所示的 UI 或 SSH 命令“show certificate”查看证书。
查看证书信息。
默认情况下,存储会为每个控制器生成唯一的 SSL 证书。为获得最强安全性,请将系统生成的默认证书替换为可信赖的证书颁发机构颁发的证书。
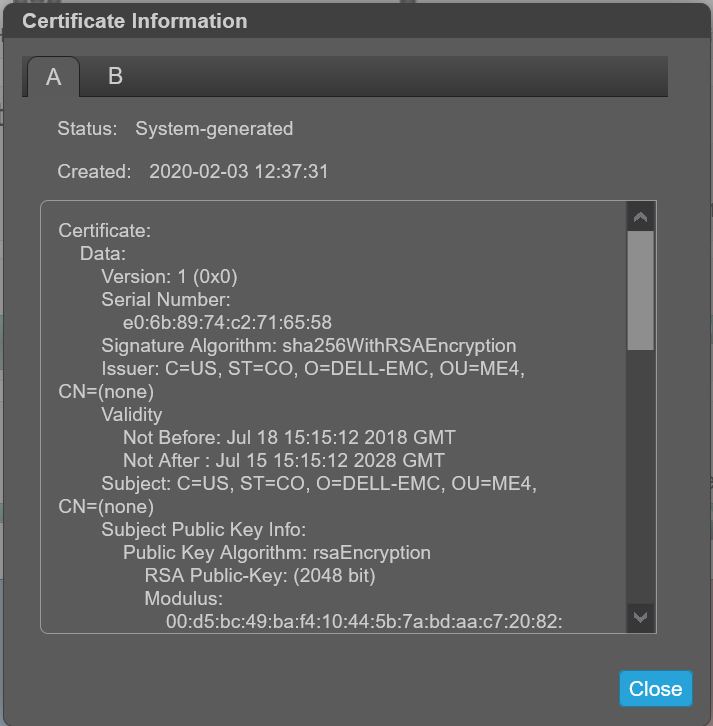
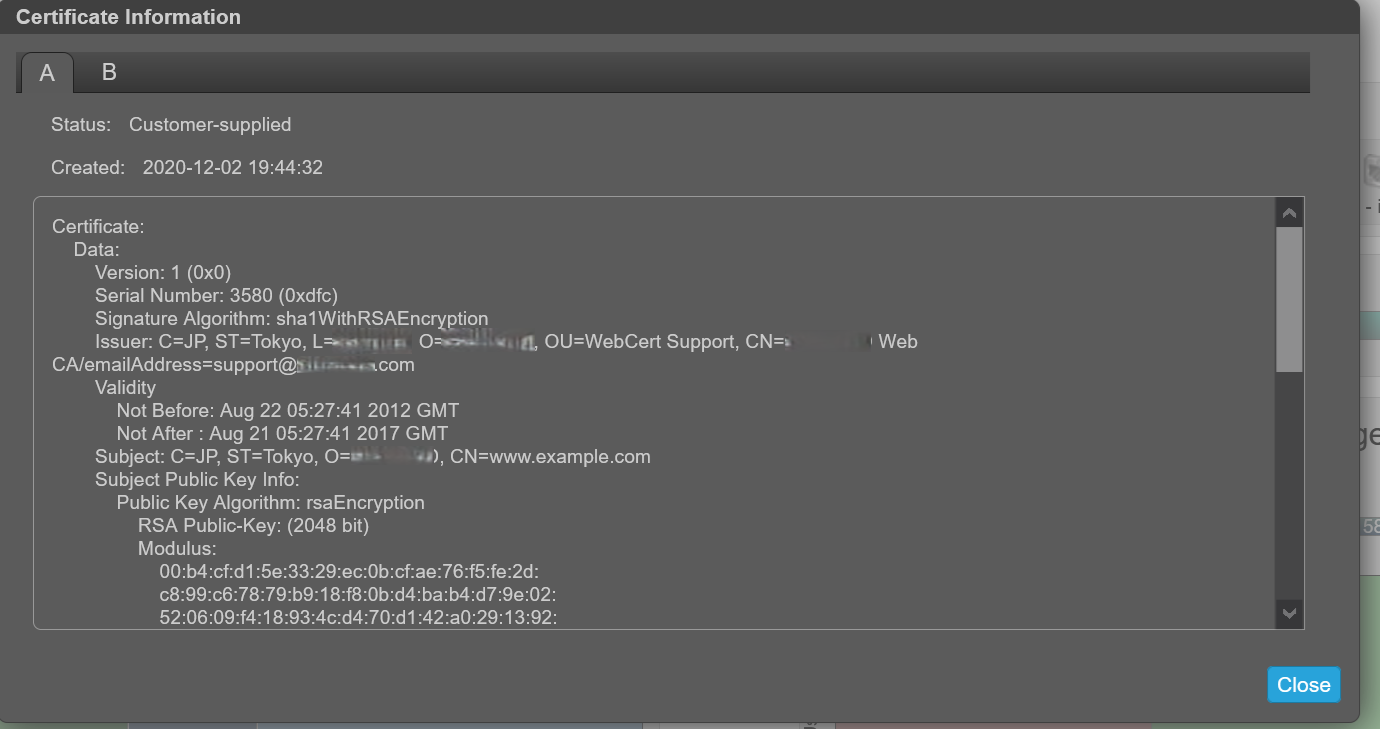
证书信息面板显示系统上为每个控制器存储的活动 SSL 证书的信息。选项卡 A 和 B 包含每个相应控制器的未格式化证书文本。该面板还显示以下状态值之一以及每个证书的创建日期:
-
客户提供 — 表示控制器正在使用客户上传的证书。
-
系统生成 — 表示控制器使用的是控制器生成的活动证书和密钥。
-
未知状态 — 表示无法读取控制器的证书。当控制器重新启动、证书更换过程仍在进行中或用户在单控制器系统中选择了合作伙伴控制器的选项卡时,通常会发生这种情况。
可以通过 FTP 或 SFTP 上传自定义证书或使用 create certificate CLI 命令的 contents 参数来使用自定义证书。这允许用户使用自己唯一的证书内容创建证书。要使新证书生效,请重新启动其管理控制器。
验证证书更换是否成功,以及控制器是否正在使用提供的证书:
- 确认证书状态为“客户提供”
- 创建日期正确无误
- 证书内容是预期的文本
查看证书信息:
-
在横幅中,单击系统面板,然后选择显示证书信息。此时将打开“证书信息”面板。
-
查看证书信息完成后,单击关闭。
在安装证书之前,信息显示“System Generated”。
安装您自己的证书后,它将标识为“客户提供”:
删除自定义证书。
要还原系统生成的证书并从两个控制器中删除自定义证书,请登录每个控制器并运行以下命令:# create certificate restore
要使证书更改生效,请在使用该命令的所有控制器上重新启动管理控制器。
使用 Linux 和 ME4 SSH 会话的仅限 CLI 的示例
-
创建证书并将“PEM .cer”和“.key”放在 Linux 计算机上。
-
从 Linux 机上的 SSH 会话中,使用 FTP 将文件传输到阵列,然后打开与阵列的 SSH 会话,以重新启动 ME4 上的两个控制器。重新启动 ME4 管理控制器后大约需要两分钟,然后用户才能重新登录 ME4 并显示新证书。提醒:一个控制器可能需要比另一个控制器更长的时间才能启动。在两个控制器都完全启动之前,存储可能会分别显示一个控制器和另一个控制器显示在客户证书上。
在下面的示例中,ME4 控制器 IP 为:
A: 100.85.XXX.X
B: 100.85.XXX.XX8
对于两个控制器,要获得证书:
- 使用 FTP 将证书和密钥文件上传到两个控制器
- 重新启动两个控制器上的管理控制器
[grpadmin@WWWWWWW certs]$ pwd
/home/grpadmin/Documents/certs
[grpadmin@WWWWWWW certs]$ ls
2048b-rsa-example-cert.pem 2048b-rsa-example-keypair.pem put
[grpadmin@WWWWWWW certs]$ ftp 100.85.QQQ.ZZZ
Connected to 100.85.QQQ.ZZZ (100.85.QQQ.ZZZ).
220-Welcome to Pure-FTPd.
220-You are user number 1 of 5 allowed.
220-Local time is now 23:29. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (100.85.QQQ.ZZZ:grpadmin): manage
331 User manage OK. Password required
Password:
230-OK. Current restricted directory is /.
.
.
230-Instructions for loading security certificate files:
230- 1. The security certificate files will consist of a pair of files.
230- You will have a certificate file and a key file.
230- 2. Log in with a user name and password.
230- 3. Type 'put <certificate-file-name> cert-file'
230- where <certificate-file-name> is the name of the certificate file
230- for your specific system.
230- 4. Type 'put <key-file-name> cert-key-file'
230- where <key-file-name> is the name of the security key file for
230- your specific system.
230- 5. Restart both Management Controllers to have the new security
230- certificate take effect.
230-
230
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put 2048b-rsa-example-cert.pem cert-file
local: 2048b-rsa-example-cert.pem remote: cert-file
227 Entering Passive Mode (100,85,QQQ,ZZZ,127,0)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-10 17:40:12)
STATUS: Loading security certificate file
226-
226 Operation Complete. (2020-12-10 17:40:18)
1050 bytes sent in 9.4e-05 secs (11170.21 Kbytes/sec)
ftp> put 2048b-rsa-example-keypair.pem cert-key-file
local: 2048b-rsa-example-keypair.pem remote: cert-key-file
227 Entering Passive Mode (100,85,QQQ,ZZZ,204,57)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-10 17:40:37)
STATUS: Loading security certificate file
Verifying uploaded certificate and key.
The uploaded SSL certificate and key have been installed. Reboot the controller to apply.
226-
226 Operation Complete. (2020-12-10 17:40:45)
1679 bytes sent in 8.5e-05 secs (19752.94 Kbytes/sec)
ftp> ls
227 Entering Passive Mode (100,85,QQQ,ZZZ,189,193)
150 Accepted data connection
-rw-rw-rw- 1 0 users 0 Dec 10 17:40 0
-rw-r--r-- 1 0 0 8436 Dec 2 20:39 README
226-Options: -l
226 2 matches total
ftp> bye
221-Goodbye. You uploaded 3 and downloaded 0 kbytes.
221 Logout.
[grpadmin@WWWWWWW certs]$ ftp 100.85.XXX.YYY
Connected to 100.85.XXX.YYY (100.85.XXX.YYY).
220-Welcome to Pure-FTPd.
220-You are user number 1 of 5 allowed.
220-Local time is now 23:30. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (100.85.XXX.YYY:grpadmin): manage
331 User manage OK. Password required
Password:
230-OK. Current restricted directory is /
.
.
.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put 2048b-rsa-example-cert.pem cert-file
local: 2048b-rsa-example-cert.pem remote: cert-file
227 Entering Passive Mode (100,85,XXX,YYY,126,144)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-11 23:30:22)
STATUS: Loading security certificate file
226-
226 Operation Complete. (2020-12-11 23:30:28)
1050 bytes sent in 4.7e-05 secs (22340.42 Kbytes/sec)
ftp> put 2048b-rsa-example-keypair.pem cert-key-file
local: 2048b-rsa-example-keypair.pem remote: cert-key-file
227 Entering Passive Mode (100,85,XXX,YYY,200,227)
150 Accepted data connection
226-File Transfer Complete. Starting Operation: (2020-12-11 23:30:40)
STATUS: Loading security certificate file
Verifying uploaded certificate and key.
The uploaded SSL certificate and key have been installed. Reboot the controller to apply.
226-
226 Operation Complete. (2020-12-11 23:30:47)
1679 bytes sent in 5.2e-05 secs (32288.46 Kbytes/sec)
ftp> bye
221-Goodbye. You uploaded 3 and downloaded 0 kbytes.
221 Logout.
[grpadmin@WWWWWWW certs]$ ssh manage@100.85.QQQ.ZZZ
Password:
DELL EMC ME4024
System Name: NDC-ME4
System Location: NDC
Version: GT280R008-01
# restart mc both
During the restart process you will briefly lose communication with the specified Management Controller(s).
Do you want to continue? (y/n) y
Info: Restarting the local MC (A)...
Success: Command completed successfully. - Both MCs were restarted. (2020-12-11 23:31:26)
# Killed
Connection to 100.85.QQQ.ZZZ closed.
.
. Will take about 2 minutes for you to be able to log back into the array to
. see the certificates
.
[grpadmin@WWWWWWW certs]$ ssh manage@100.85.QQQ.ZZZ
Password:
DELL EMC ME4024
System Name: NDC-ME4
System Location: NDC
Version: GT280R008-01
# show certificates
Error: The command was not recognized. (2020-12-11 23:36:35)
# show certificate
Certificate Status
------------------
Controller: A
Certificate Status: Customer-supplied
Time Created: 2020-12-11 23:29:29
Certificate Text: Certificate:
Data:
Version: 1 (0x0)
Serial Number: 3580 (0xdfc)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=JP, ST=Tokyo, L=RRRRRRR, O=SSSSSSSSS, OU=WebCert Support, CN=SSSSSSSSS Web CA/emailAddress=support@SSSSSSSSS.com
Validity
Not Before: Aug 22 05:27:41 2012 GMT
Not After : Aug 21 05:27:41 2017 GMT
Subject: C=JP, ST=Tokyo, O=SSSSSSSSS, CN=www.example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b4:cf:d1:5e:33:29:ec:0b:cf:ae:76:f5:fe:2d:
c8:99:c6:78:79:b9:18:f8:0b:d4:ba:b4:d7:9e:02:
52:06:09:f4:18:93:4c:d4:70:d1:42:a0:29:13:92:
73:50:77:f6:04:89:ac:03:2c:d6:f1:06:ab:ad:6c:
c0:d9:d5:a6:ab:ca:cd:5a:d2:56:26:51:e5:4b:08:
8a:af:cc:19:0f:25:34:90:b0:2a:29:41:0f:55:f1:
---REDACTED---
9a:24:79:49:17:27:d7:89:4b:6a:2e:0d:87:51:d9:
23:3d:06:85:56:f8:58:31:0e:ee:81:99:78:68:cd:
6e:44:7e:c9:da:8c:5a:7b:1c:bf:24:40:29:48:d1:
03:9c:ef:dc:ae:2a:5d:f8:f7:6a:c7:e9:bc:c5:b0:
59:f6:95:fc:16:cb:d8:9c:ed:c3:fc:12:90:93:78:
5a:75:b4:56:83:fa:fc:41:84:f6:64:79:34:35:1c:
ac:7a:85:0e:73:78:72:01:e7:24:89:25:9e:da:7f:
65:bc:af:87:93:19:8c:db:75:15:b6:e0:30:c7:08:
f8:59
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
40:cb:fe:04:5b:c6:74:c5:73:91:06:90:df:ff:b6:9e:85:73:
fe:e0:0a:6f:3a:44:2f:cc:53:73:16:32:3f:79:64:39:e8:78:
---REDACTED---
1b:d7:eb:c0:31:6c:86:a0:f6:55:a8:f8:10:d0:42:06:1e:94:
a5:e0:68:a7:9f:b6:f3:9c:d0:e1:22:3b:ab:85:3d:a1:27:9b:
50:32:62:b8:ec:7a:fa:d6:7d:2b:29:e6:ad:b2:69:4d:28:b4:
f8:13
Certificate Status
------------------
Controller: B Certificate Status: Customer-supplied
Time Created: 2020-12-11 23:30:22
Certificate Text: Certificate:
Data:
Version: 1 (0x0)
Serial Number: 3580 (0xdfc)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=JP, ST=Tokyo, L=RRRRRRR, O=SSSSSSSSS, OU=WebCert Support, CN=SSSSSSSSS Web CA/emailAddress=support@SSSSSSSSS.com
Validity
Not Before: Aug 22 05:27:41 2012 GMT
Not After : Aug 21 05:27:41 2017 GMT
Subject: C=JP, ST=Tokyo, O=SSSSSSSSS, CN=www.example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b4:cf:d1:5e:33:29:ec:0b:cf:ae:76:f5:fe:2d:
c8:99:c6:78:79:b9:18:f8:0b:d4:ba:b4:d7:9e:02:
52:06:09:f4:18:93:4c:d4:70:d1:42:a0:29:13:92:
73:50:77:f6:04:89:ac:03:2c:d6:f1:06:ab:ad:6c:
c0:d9:d5:a6:ab:ca:cd:5a:d2:56:26:51:e5:4b:08:
8a:af:cc:19:0f:25:34:90:b0:2a:29:41:0f:55:f1:
---REDACTED---
9a:24:79:49:17:27:d7:89:4b:6a:2e:0d:87:51:d9:
23:3d:06:85:56:f8:58:31:0e:ee:81:99:78:68:cd:
6e:44:7e:c9:da:8c:5a:7b:1c:bf:24:40:29:48:d1:
03:9c:ef:dc:ae:2a:5d:f8:f7:6a:c7:e9:bc:c5:b0:
59:f6:95:fc:16:cb:d8:9c:ed:c3:fc:12:90:93:78:
5a:75:b4:56:83:fa:fc:41:84:f6:64:79:34:35:1c:
ac:7a:85:0e:73:78:72:01:e7:24:89:25:9e:da:7f:
65:bc:af:87:93:19:8c:db:75:15:b6:e0:30:c7:08:
f8:59
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
40:cb:fe:04:5b:c6:74:c5:73:91:06:90:df:ff:b6:9e:85:73:
fe:e0:0a:6f:3a:44:2f:cc:53:73:16:32:3f:79:64:39:e8:78:
---REDACTED---
1b:d7:eb:c0:31:6c:86:a0:f6:55:a8:f8:10:d0:42:06:1e:94:
a5:e0:68:a7:9f:b6:f3:9c:d0:e1:22:3b:ab:85:3d:a1:27:9b:
50:32:62:b8:ec:7a:fa:d6:7d:2b:29:e6:ad:b2:69:4d:28:b4:
f8:13
Success: Command completed successfully. (2020-12-11 23:36:41)
#