APEX kullanıcısı, PowerScale Webui'den S3 anahtarları oluşturamaz
Summary: OneFS 9.3.0.4'te, müşteri APEX kullanıcı hesabı yeni BasicUser rolüyle ilişkilendirildi ve OneFS webui'den S3 anahtarları oluşturamıyor. Anahtar yönetimi sekmesi, müşteri APEX hesabı için görünür değildir. ...
This article applies to
This article does not apply to
This article is not tied to any specific product.
Not all product versions are identified in this article.
Symptoms
Müşteri APEX hesabı apex01 ile OneFS webui'de oturum açın.
Protocols -> Object storage (S3) öğesine tıklayın.
Key management (Anahtar yönetimi) sekmesinin görünür olmadığını gözlemleyin.
Örnek:
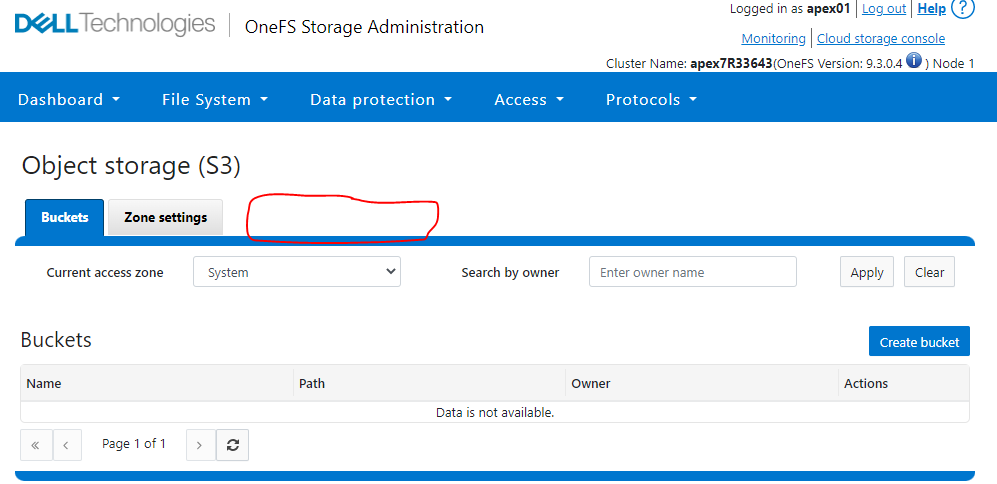
Protocols -> Object storage (S3) öğesine tıklayın.
Key management (Anahtar yönetimi) sekmesinin görünür olmadığını gözlemleyin.
Örnek:

Cause
APEX müşteri hesabı, OneFS webui'yi kullanarak S3 anahtarları oluşturma ayrıcalığına sahip değildir.
Resolution
Müşteri için rest API geçici çözümü:
1. Oturum oluşturma.
2. S3 anahtarı oluşturun.
curl -kv -H "Content-type:application/json" -H "X-CSRF-Token: " -H "Referer:https://" -X POST https://:8080/platform/12/protocols/s3/mykeys -b /tmp/cookie.txt
Not: Müşteri Apex01 hesabında PowerScale CLI erişimi yoktur, bu nedenle müşterinin geçici çözümü bir NFS istemciden veya PowerScale ile ağ bağlantısı olan bir Windows komut isteminden çalıştırması gerekir.
PowerScale Laboratuvar Örneği:
1. Oturum oluşturma:
Node_IP = X.X.X.X
Kullanıcı Adı = apex01
Parolası = apex01 kullanıcı hesabı parolası
2. S3 anahtarı oluşturun:
Node_IP = X.X.X.X.X
CSRF Belirteci değeri = 14762d26-e806-41c1-b310-4497afb28953 (oturum oluşturma komutundan kırmızı renkle vurgulanana bakın)
secret_key = oluşturulan S3 tuşu (aşağıda yeşil renkte)
1. Oturum oluşturma.
Windows CMD istemi:
curl --request POST --insecure 'https://:8080/session/1/session' --header 'Content-Type: application/json' --data-raw '{"username": "", "parola": "", "services": ["platform","ad alanı"]}' -v -c /tmp/cookie.txt
Linux istemci CLI'sı:
curl --request POST --insecure 'https://:8080/session/1/session' --header 'Content-Type: application/json' --data '{"username": "", "parola": "", "services": ["platform","ad alanı"]}' -v -c /tmp/cookie.txt
2. S3 anahtarı oluşturun.
curl -kv -H "Content-type:application/json" -H "X-CSRF-Token: " -H "Referer:https://" -X POST https://:8080/platform/12/protocols/s3/mykeys -b /tmp/cookie.txt
Not: Müşteri Apex01 hesabında PowerScale CLI erişimi yoktur, bu nedenle müşterinin geçici çözümü bir NFS istemciden veya PowerScale ile ağ bağlantısı olan bir Windows komut isteminden çalıştırması gerekir.
PowerScale Laboratuvar Örneği:
1. Oturum oluşturma:
Node_IP = X.X.X.X
Kullanıcı Adı = apex01
Parolası = apex01 kullanıcı hesabı parolası
apex7R33643-3% curl --request POST --insecure 'https://X.X.X.X:8080/session/1/session' --header 'Content-Type: application/json' --data-raw '{"username": "apex01","password": "","services": ["platform","namespace"]}' -v -c /tmp/cookie.txt
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying X.X.X.X:8080...
* Connected to X.X.X.X (X.X.X.X) port 8080 (#0)
* ALPN, offering http/1.1
* Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH
* successfully set certificate verify locations:
* CAfile: none
* CApath: /etc/ssl/certs/
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / DHE-RSA-AES256-SHA
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* start date: Apr 14 20:51:44 2022 GMT
* expire date: Jul 16 20:51:44 2024 GMT
* issuer: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* SSL certificate verify result: self signed certificate (18), continuing anyway.
> POST /session/1/session HTTP/1.1
> Host: X.X.X.X:8080
> User-Agent: curl/7.79.1
> Accept: */*
> Content-Type: application/json
> Content-Length: 83
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 201 Created
< Date: Tue, 21 Jun 2022 13:52:33 GMT
< Server: Apache
< X-Frame-Options: sameorigin
< X-Content-Type-Options: nosniff
< Strict-Transport-Security: max-age=31536000;
* Added cookie isisessid="eyJhbGciOiJQUzUxMiJ9.eyJhdWQiOlsicGxhdGZvcm0iLCJuYW1lc3BhY2UiXSwiZXhwIjoxNjU1ODMzOTUzLCJpYXQiOjE2NTU4MTk1NTMsIm9uZWZzL2NzcmYiOiIxNDc2MmQyNi1lODA2LTQxYzEtYjMxMC00NDk3YWZiMjg5NTMiLCJvbmVmcy9pcCI6IjEyOC4yMjEuMjI3LjMzIiwib25lZnMvbm9uY2UiOjExMTUzNzgyODM1MTU4MjE5ODk0LCJvbmVmcy9zZXNzaW9uIjoiYmZkMjVhMTMtMDNlOS00OTdhLTk2OWYtYmEwZjU1YmFhZTAzIiwib25lZnMvdWEiOiJjdXJsLzcuNzkuMSIsIm9uZWZzL3ppZCI6MSwic3ViIjoiYXBleDAxIn0K.ioRleO4O9kqDcQfzDUpjKDA9bgnpqqSYPQWJ9sDRSfkL0xI1F29YpTvnoa3uKPLZ7pE8sedkk6vpPcif1Tb7L7-9t4fG2kIXJKK7vm1VNNStUFRQMHMc1vaf8UzKwwJJKf0S_3GltOo8iRK2fdkw_bigw2xOwIHr-85YCHGJeYdFiJ2pK_CI_zYPbGAeg5hJFV7Ylci9FDRI8SDElIBe8FrvaZuiPsMloRU8oL4dxco1jAfPhjsv3YOUDXTEq7kI3xCNkKIj5PtQMjQInDz4qxHVNo9Ks7uEm2cjYotNcQ424i0tuGTe2piwdvlaiEC6WaqKo7HhuPEYqQ7vmgK_seCEb9GY6wAXw9xhpfRHb38f2qDohZj17J-6TzKU32PZ9NJutAidTFIVKH01JGOPRRdPM9oex4VH7FUFDhPAGSng1nmBEx6wk10D1LjTB36UbSQ9lkrh7y84DLZYSlJAfo3iX1_w4bZ0tZHa51K13KedLb4E3Jafjkp-MOUUwMMbjXDgxoC0IRWc2HgilDnvKaSe7R8t9vogW0E5m-0jophQD70BY7UioNu-U6CnaoFojQ-yKFS3t6ZV8i40mD3XaZKS5oeePUFWmlmPFEugziuS4dTdQY-_Myei1RhQPRydp_xFUVZyBb79yv71FLtouqB3UY0zy0qiWDip6VRCphc%3D" for domain X.X.X.X, path /, expire 0
< Set-Cookie: isisessid=eyJhbGciOiJQUzUxMiJ9.eyJhdWQiOlsicGxhdGZvcm0iLCJuYW1lc3BhY2UiXSwiZXhwIjoxNjU1ODMzOTUzLCJpYXQiOjE2NTU4MTk1NTMsIm9uZWZzL2NzcmYiOiIxNDc2MmQyNi1lODA2LTQxYzEtYjMxMC00NDk3YWZiMjg5NTMiLCJvbmVmcy9pcCI6IjEyOC4yMjEuMjI3LjMzIiwib25lZnMvbm9uY2UiOjExMTUzNzgyODM1MTU4MjE5ODk0LCJvbmVmcy9zZXNzaW9uIjoiYmZkMjVhMTMtMDNlOS00OTdhLTk2OWYtYmEwZjU1YmFhZTAzIiwib25lZnMvdWEiOiJjdXJsLzcuNzkuMSIsIm9uZWZzL3ppZCI6MSwic3ViIjoiYXBleDAxIn0K.ioRleO4O9kqDcQfzDUpjKDA9bgnpqqSYPQWJ9sDRSfkL0xI1F29YpTvnoa3uKPLZ7pE8sedkk6vpPcif1Tb7L7-9t4fG2kIXJKK7vm1VNNStUFRQMHMc1vaf8UzKwwJJKf0S_3GltOo8iRK2fdkw_bigw2xOwIHr-85YCHGJeYdFiJ2pK_CI_zYPbGAeg5hJFV7Ylci9FDRI8SDElIBe8FrvaZuiPsMloRU8oL4dxco1jAfPhjsv3YOUDXTEq7kI3xCNkKIj5PtQMjQInDz4qxHVNo9Ks7uEm2cjYotNcQ424i0tuGTe2piwdvlaiEC6WaqKo7HhuPEYqQ7vmgK_seCEb9GY6wAXw9xhpfRHb38f2qDohZj17J-6TzKU32PZ9NJutAidTFIVKH01JGOPRRdPM9oex4VH7FUFDhPAGSng1nmBEx6wk10D1LjTB36UbSQ9lkrh7y84DLZYSlJAfo3iX1_w4bZ0tZHa51K13KedLb4E3Jafjkp-MOUUwMMbjXDgxoC0IRWc2HgilDnvKaSe7R8t9vogW0E5m-0jophQD70BY7UioNu-U6CnaoFojQ-yKFS3t6ZV8i40mD3XaZKS5oeePUFWmlmPFEugziuS4dTdQY-_Myei1RhQPRydp_xFUVZyBb79yv71FLtouqB3UY0zy0qiWDip6VRCphc%3D; path=/; HttpOnly; Secure; SameSite=strict
* Added cookie isicsrf="14762d26-e806-41c1-b310-4497afb28953" for domain X.X.X.X, path /, expire 0
< Set-Cookie: isicsrf=14762d26-e806-41c1-b310-4497afb28953; path=/; Secure
< Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data:; script-src 'self' 'unsafe-eval'; style-src 'unsafe-inline' 'self';
< Content-Length: 106
< Content-Type: application/json
<
{"services":["platform","namespace"],"timeout_absolute":14400,"timeout_inactive":900,"username":"apex01"}
* Connection #0 to host X.X.X.X left intact
apex7R33643-3%
2. S3 anahtarı oluşturun:
Node_IP = X.X.X.X.X
CSRF Belirteci değeri = 14762d26-e806-41c1-b310-4497afb28953 (oturum oluşturma komutundan kırmızı renkle vurgulanana bakın)
secret_key = oluşturulan S3 tuşu (aşağıda yeşil renkte)
apex7R33643-3% curl -kv -H "Content-type:application/json" -H "X-CSRF-Token: 14762d26-e806-41c1-b310-4497afb28953" -H "Referer:https://X.X.X.X" -X POST https://X.X.X.X:8080/platform/12/protocols/s3/mykeys -b /tmp/cookie.txt
* Trying X.X.X.X:8080...
* Connected to X.X.X.X (X.X.X.X) port 8080 (#0)
* ALPN, offering http/1.1
* Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH
* successfully set certificate verify locations:
* CAfile: none
* CApath: /etc/ssl/certs/
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / DHE-RSA-AES256-SHA
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* start date: Apr 14 20:51:44 2022 GMT
* expire date: Jul 16 20:51:44 2024 GMT
* issuer: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* SSL certificate verify result: self signed certificate (18), continuing anyway.
> POST /platform/12/protocols/s3/mykeys HTTP/1.1
> Host: X.X.X.X:8080
> User-Agent: curl/7.79.1
> Accept: */*
> Cookie: isisessid=eyJhbGciOiJQUzUxMiJ9.eyJhdWQiOlsicGxhdGZvcm0iLCJuYW1lc3BhY2UiXSwiZXhwIjoxNjU1ODMzOTUzLCJpYXQiOjE2NTU4MTk1NTMsIm9uZWZzL2NzcmYiOiIxNDc2MmQyNi1lODA2LTQxYzEtYjMxMC00NDk3YWZiMjg5NTMiLCJvbmVmcy9pcCI6IjEyOC4yMjEuMjI3LjMzIiwib25lZnMvbm9uY2UiOjExMTUzNzgyODM1MTU4MjE5ODk0LCJvbmVmcy9zZXNzaW9uIjoiYmZkMjVhMTMtMDNlOS00OTdhLTk2OWYtYmEwZjU1YmFhZTAzIiwib25lZnMvdWEiOiJjdXJsLzcuNzkuMSIsIm9uZWZzL3ppZCI6MSwic3ViIjoiYXBleDAxIn0K.ioRleO4O9kqDcQfzDUpjKDA9bgnpqqSYPQWJ9sDRSfkL0xI1F29YpTvnoa3uKPLZ7pE8sedkk6vpPcif1Tb7L7-9t4fG2kIXJKK7vm1VNNStUFRQMHMc1vaf8UzKwwJJKf0S_3GltOo8iRK2fdkw_bigw2xOwIHr-85YCHGJeYdFiJ2pK_CI_zYPbGAeg5hJFV7Ylci9FDRI8SDElIBe8FrvaZuiPsMloRU8oL4dxco1jAfPhjsv3YOUDXTEq7kI3xCNkKIj5PtQMjQInDz4qxHVNo9Ks7uEm2cjYotNcQ424i0tuGTe2piwdvlaiEC6WaqKo7HhuPEYqQ7vmgK_seCEb9GY6wAXw9xhpfRHb38f2qDohZj17J-6TzKU32PZ9NJutAidTFIVKH01JGOPRRdPM9oex4VH7FUFDhPAGSng1nmBEx6wk10D1LjTB36UbSQ9lkrh7y84DLZYSlJAfo3iX1_w4bZ0tZHa51K13KedLb4E3Jafjkp-MOUUwMMbjXDgxoC0IRWc2HgilDnvKaSe7R8t9vogW0E5m-0jophQD70BY7UioNu-U6CnaoFojQ-yKFS3t6ZV8i40mD3XaZKS5oeePUFWmlmPFEugziuS4dTdQY-_Myei1RhQPRydp_xFUVZyBb79yv71FLtouqB3UY0zy0qiWDip6VRCphc%3D; isicsrf=14762d26-e806-41c1-b310-4497afb28953
> Content-type:application/json
> X-CSRF-Token: 14762d26-e806-41c1-b310-4497afb28953
> Referer:https://X.X.X.X
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 201 Created
< Date: Tue, 21 Jun 2022 13:54:51 GMT
< Server: Apache
< Allow: GET, POST, DELETE, HEAD
< X-Frame-Options: sameorigin
< X-Content-Type-Options: nosniff
< Strict-Transport-Security: max-age=31536000;
< Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data:; script-src 'self' 'unsafe-eval'; style-src 'unsafe-inline' 'self';
< Transfer-Encoding: chunked
< Content-Type: application/json
<
{
"keys" :
{
"access_id" : "1_apex01_accid",
"secret_key" : "<< SECRET KEY >>>",
"secret_key_timestamp" : 1655819691
}
}
* Connection #0 to host X.X.X.X left intact
apex7R33643-3%
Affected Products
APEX, APEX Data Storage ServicesArticle Properties
Article Number: 000200704
Article Type: Solution
Last Modified: 28 Jun 2023
Version: 7
Find answers to your questions from other Dell users
Support Services
Check if your device is covered by Support Services.