Avamar- og Data Domain-integration: Kan ikke synkronisere certifikater med sessionssikkerhed aktiveret
Resumen: Når Session Security er aktiveret på Avamar, skal certifikater synkronisere mellem Avamar og Data Domain. Dette kræver, at SCP-protokollen er aktiveret på Data Domain.
Este artículo se aplica a
Este artículo no se aplica a
Este artículo no está vinculado a ningún producto específico.
No se identifican todas las versiones del producto en este artículo.
Síntomas
Sikkerhedskopieringer kan mislykkes med følgende fejl:
Når du har kontrolleret MCS-logfilerne, er der en undtagelse relateret til SCP-protokollen.
DDR result code: 5049, desc: file not found DDR result code: 5341, desc: SSL library error "failed to import host or ca certificate automatically" DDR result code: 5008, desc: invalid argumentNår følgende Dell-artikel 197106, Avamar- og Data Domain-integration: DD, der viser Red i Avamar AUI og eller brugergrænsefladens løsningssti, genereres ikke certifikater.
Når du har kontrolleret MCS-logfilerne, er der en undtagelse relateret til SCP-protokollen.
09/29-16:29:13.00727 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.DdrCache.firsttimeToAddEx FINE: Importing host certificate and ca certificates... 09/29-16:29:13.00743 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.DdrSsh.executeDdrCommand FINE: Executing ddr command. host: idpa-lab.dell.com cmd: adminaccess certificate cert-signing-request show ... 09/29-16:29:14.00095 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.kc.PrefsCertRsa. FINE: RSA certificate: 09/29-16:29:14.00095 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.kc.PrefsCertRsa. FINE: Message digest algorithm: sha512 09/29-16:29:14.00095 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.PrefsDdrCert. INFO: DD RSA certificate: 09/29-16:29:14.00095 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.PrefsDdrCert. INFO: Number bits(key strength): 3072bit 09/29-16:29:14.00095 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.PrefsDdrCert. INFO: Message digest algorithm: sha512 09/29-16:29:14.00137 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.DdrSsh.executeDdrCommand FINE: Executing ddr command. host: idpa-lab.dell.com cmd: adminaccess certificate cert-signing-request generate key-strength 3072bit country 'US' state 'California' city 'Irvine' org-name 'EMC Corp' org-unit 'BRS Division'... 09/29-16:29:14.00721 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.DdrSsh.copyFile FINE: Copying file from host: idpa-lab.dell.com... 09/29-16:29:15.00619 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.datadomain.DdrSsh.copyFile WARNING: Failed to copy file from host: idpa-lab.dell.com. 09/29-16:29:15.00619 [RMI TCP Connection(27)-192.x.x.x#965] com.avamar.mc.util.MCException.logException WARNING: com.maverick.ssh.SshException: java.io.IOException at com.maverick.scp.ScpClientIO.get(ScpClientIO.java:151) at com.maverick.scp.ScpClientIO.get(ScpClientIO.java:124) at com.avamar.mc.datadomain.DdrSsh.copyFile(DdrSsh.java:940) at com.avamar.mc.datadomain.DdrSsh.copyFileEx(DdrSsh.java:961) at com.avamar.mc.datadomain.DdrSshCertificateCmd.getcertificateSigningRequest(DdrSshCertificateCmd.java:200) at com.avamar.mc.datadomain.DataDomainService.generateAndImportDdrHostCert(DataDomainService.java:5520) at com.avamar.mc.datadomain.DataDomainService.firsttimeToAdd(DataDomainService.java:5183) at com.avamar.mc.datadomain.DataDomainService.firsttimeToAdd(DataDomainService.java:6041) at com.avamar.mc.datadomain.DdrCache.firsttimeToAdd(DdrCache.java:1599) at com.avamar.mc.datadomain.DdrCache.firsttimeToAddEx(DdrCache.java:1645) at com.avamar.mc.datadomain.DdrCache.ConfigCerts(DdrCache.java:1454) at com.avamar.mc.datadomain.DdrCache.checkAndConfigCerts(DdrCache.java:1251) at com.avamar.mc.datadomain.DdrCache.update(DdrCache.java:402) at com.avamar.mc.datadomain.DdrCache.update(DdrCache.java:676) at com.avamar.mc.datadomain.DataDomainService.rewriteDdrCloudInfo(DataDomainService.java:6457) at com.avamar.mc.datadomain.DataDomainService.disableCloudTier(DataDomainService.java:6486) at com.avamar.mc.datadomain.DataDomainService._updateDdr(DataDomainService.java:1271) at com.avamar.mc.datadomain.DataDomainService.updateDdr(DataDomainService.java:1036) at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method) at sun.reflect.NativeMethodAccessorImpl.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source) at java.lang.reflect.Method.invoke(Unknown Source) at org.springframework.aop.support.AopUtils.invokeJoinpointUsingReflection(AopUtils.java:318) at org.springframework.aop.framework.ReflectiveMethodInvocation.invokeJoinpoint(ReflectiveMethodInvocation.java:183) at org.springframework.aop.support.AopUtils.invokeJoinpointUsingReflection(AopUtils.java:318) at org.springframework.aop.framework.ReflectiveMethodInvocation.invokeJoinpoint(ReflectiveMethodInvocation.java:183) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:150) at org.springframework.security.access.intercept.aopalliance.MethodSecurityInterceptor.invoke(MethodSecurityInterceptor.java:61) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172) at org.springframework.aop.framework.JdkDynamicAopProxy.invoke(JdkDynamicAopProxy.java:202) at com.sun.proxy.$Proxy37.updateDdr(Unknown Source) at com.avamar.mc.datadomain.DataDomainServiceContext.updateDdr(DataDomainServiceContext.java:223) at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method) at sun.reflect.NativeMethodAccessorImpl.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source) at java.lang.reflect.Method.invoke(Unknown Source) at sun.rmi.server.UnicastServerRef.dispatch(Unknown Source) at sun.rmi.transport.Transport$1.run(Unknown Source) at sun.rmi.transport.Transport$1.run(Unknown Source) at java.security.AccessController.doPrivileged(Native Method) at sun.rmi.transport.Transport.serviceCall(Unknown Source) at sun.rmi.transport.tcp.TCPTransport.handleMessages(Unknown Source) at sun.rmi.transport.tcp.TCPTransport$ConnectionHandler.run0(Unknown Source) at sun.rmi.transport.tcp.TCPTransport$ConnectionHandler.lambda$run$0(Unknown Source) at java.security.AccessController.doPrivileged(Native Method) at sun.rmi.transport.tcp.TCPTransport$ConnectionHandler.run(Unknown Source) at java.util.concurrent.ThreadPoolExecutor.runWorker(Unknown Source) at java.util.concurrent.ThreadPoolExecutor$Worker.run(Unknown Source) at java.lang.Thread.run(Unknown Source) Caused by: java.io.IOException: SCP unexpected cmd: Scp is disabled. Access denied. at com.maverick.scp.ScpClientIO$ScpEngineIO.readStreamFromRemote(ScpClientIO.java:305) at com.maverick.scp.ScpClientIO.get(ScpClientIO.java:148) at com.maverick.scp.ScpClientIO.get(ScpClientIO.java:124) at com.avamar.mc.datadomain.DdrSsh.copyFile(DdrSsh.java:940) at com.avamar.mc.datadomain.DdrSsh.copyFileEx(DdrSsh.java:961) at com.avamar.mc.datadomain.DdrSshCertificateCmd.getcertificateSigningRequest(DdrSshCertificateCmd.java:200) at com.avamar.mc.datadomain.DataDomainService.generateAndImportDdrHostCert(DataDomainService.java:5520) at com.avamar.mc.datadomain.DataDomainService.firsttimeToAdd(DataDomainService.java:5183) at com.avamar.mc.datadomain.DataDomainService.firsttimeToAdd(DataDomainService.java:6041) at com.avamar.mc.datadomain.DdrCache.firsttimeToAdd(DdrCache.java:1599) at com.avamar.mc.datadomain.DdrCache.firsttimeToAddEx(DdrCache.java:1645) at com.avamar.mc.datadomain.DdrCache.ConfigCerts(DdrCache.java:1454) at com.avamar.mc.datadomain.DdrCache.checkAndConfigCerts(DdrCache.java:1251) at com.avamar.mc.datadomain.DdrCache.update(DdrCache.java:402) at com.avamar.mc.datadomain.DdrCache.update(DdrCache.java:676) at com.avamar.mc.datadomain.DataDomainService.rewriteDdrCloudInfo(DataDomainService.java:6457) at com.avamar.mc.datadomain.DataDomainService.disableCloudTier(DataDomainService.java:6486) at com.avamar.mc.datadomain.DataDomainService._updateDdr(DataDomainService.java:1271) at com.avamar.mc.datadomain.DataDomainService.updateDdr(DataDomainService.java:1036) at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method) at sun.reflect.NativeMethodAccessorImpl.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source) at java.lang.reflect.Method.invoke(Unknown Source) at org.springframework.aop.support.AopUtils.invokeJoinpointUsingReflection(AopUtils.java:318) at org.springframework.aop.framework.ReflectiveMethodInvocation.invokeJoinpoint(ReflectiveMethodInvocation.java:183) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:150) at org.springframework.security.access.intercept.aopalliance.MethodSecurityInterceptor.invoke(MethodSecurityInterceptor.java:61) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172) at org.springframework.aop.framework.JdkDynamicAopProxy.invoke(JdkDynamicAopProxy.java:202) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172) at org.springframework.aop.framework.JdkDynamicAopProxy.invoke(JdkDynamicAopProxy.java:202) at com.sun.proxy.$Proxy37.updateDdr(Unknown Source) at com.avamar.mc.datadomain.DataDomainServiceContext.updateDdr(DataDomainServiceContext.java:223) at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method) at sun.reflect.NativeMethodAccessorImpl.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source) at java.lang.reflect.Method.invoke(Unknown Source) at sun.rmi.server.UnicastServerRef.dispatch(Unknown Source) at sun.rmi.transport.Transport$1.run(Unknown Source) at sun.rmi.transport.Transport$1.run(Unknown Source) at java.security.AccessController.doPrivileged(Native Method) at sun.rmi.transport.Transport.serviceCall(Unknown Source) at sun.rmi.transport.tcp.TCPTransport.handleMessages(Unknown Source) at sun.rmi.transport.tcp.TCPTransport$ConnectionHandler.run0(Unknown Source) at sun.rmi.transport.tcp.TCPTransport$ConnectionHandler.lambda$run$0(Unknown Source) at java.security.AccessController.doPrivileged(Native Method) at sun.rmi.transport.tcp.TCPTransport$ConnectionHandler.run(Unknown Source) at java.util.concurrent.ThreadPoolExecutor.runWorker(Unknown Source) at java.util.concurrent.ThreadPoolExecutor$Worker.run(Unknown Source) at java.lang.Thread.run(Unknown Source)
Causa
Gennemse mcserver-loggen:
Strømmen af synkroniseringscertifikater mellem Avamar og Data Domain kræver, at SCP aktiveres som vist nedenfor:
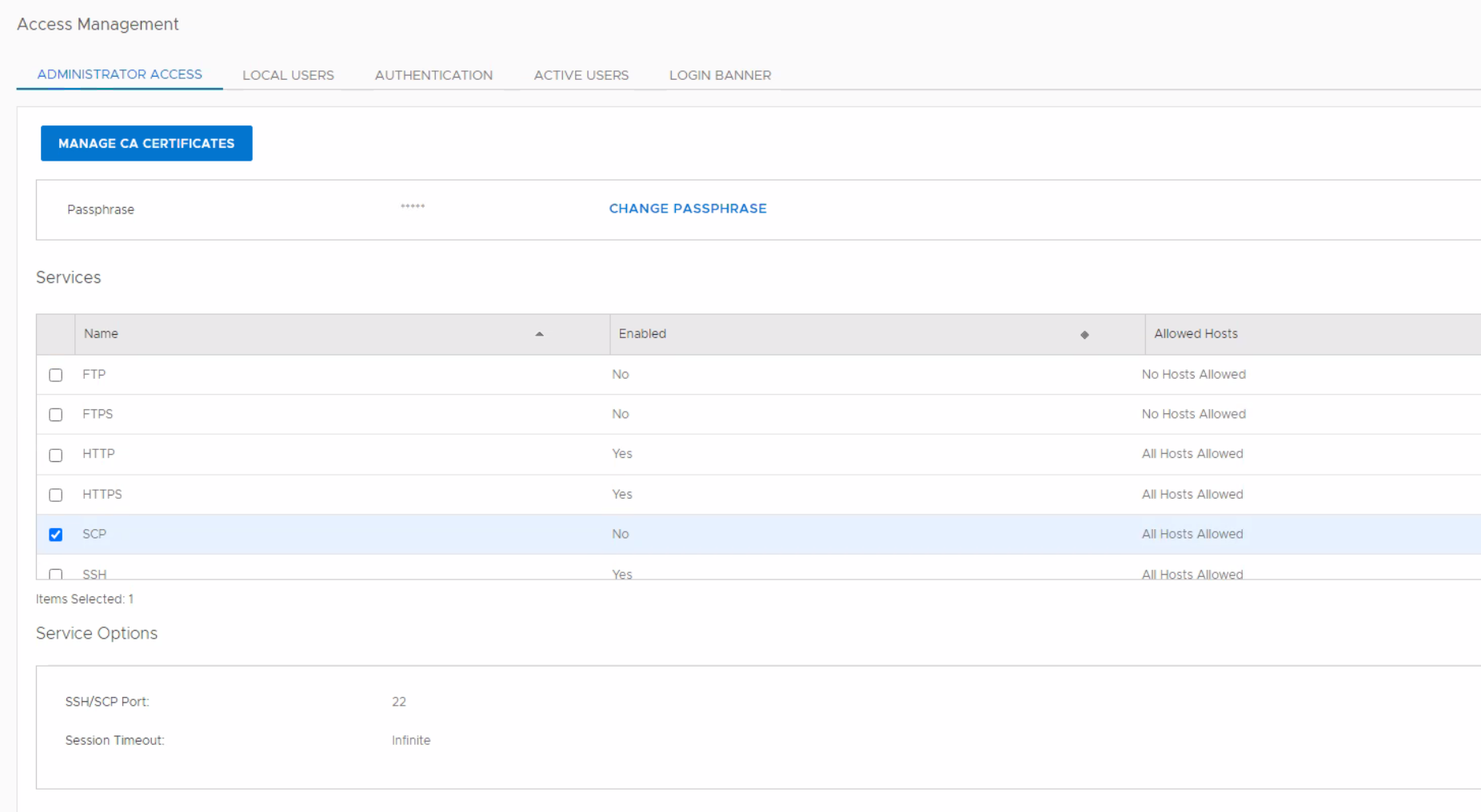
Figur 1: Data Domain-brugergrænsefladen viser, at SCP er deaktiveret
/usr/local/avamar/var/mc/server_log/mcserver.log.0 Caused by: java.io.IOException: SCP unexpected cmd: Scp is disabled. Access denied.Dette viser, at SCP-protokollen er deaktiveret på Data Domain.
Strømmen af synkroniseringscertifikater mellem Avamar og Data Domain kræver, at SCP aktiveres som vist nedenfor:
- Avamar kører en kommando på Data Domain ved hjælp af den offentlige Data Domain-nøgle til adgangskodefri godkendelse. Den første kommando er at generere en anmodning om certifikatsignering (CSR) på Data Domain.
- Avamar forsøger derefter at kopiere CSR fra Data Domain ved hjælp af SCP, men undlader at gøre det, når SCP er deaktiveret på Data Domain.
- Avamar vil bruge CSR til at underskrive et certifikat, der er udstedt til Data Domain af Avamar Root-nøglecentret. På Data Domain kaldes det "imported-host ddboost"-certifikatet.

Figur 1: Data Domain-brugergrænsefladen viser, at SCP er deaktiveret
Resolución
Aktivér SCP i Data Domain-webgrænsefladen
fra Administration > Adgang > tjenester > Kontrollér SCP > Konfigurer > Kontroller Tillad SCP.
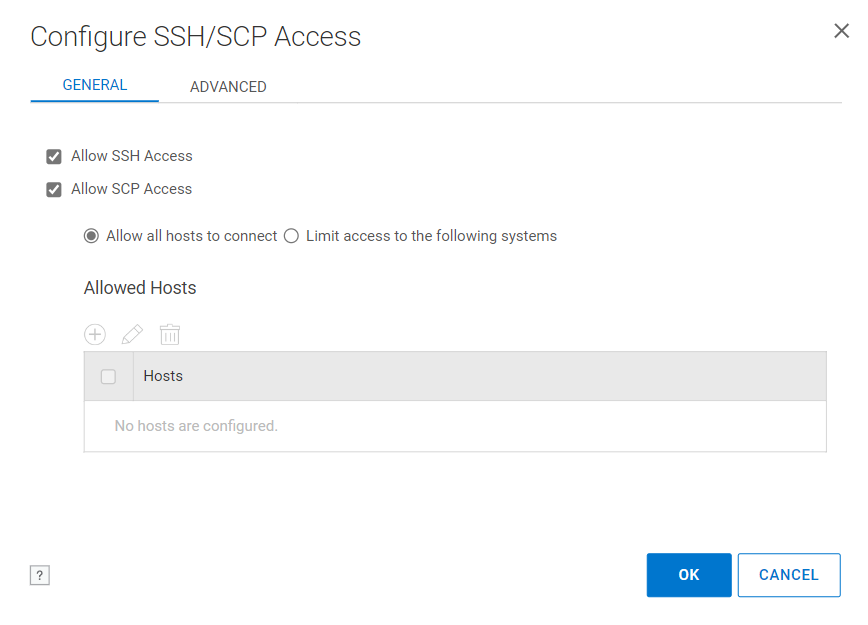
Figur 2: Aktiver SCP i Data Domain-webgrænsefladen
fra Administration > Adgang > tjenester > Kontrollér SCP > Konfigurer > Kontroller Tillad SCP.

Figur 2: Aktiver SCP i Data Domain-webgrænsefladen
Productos afectados
AvamarPropiedades del artículo
Número del artículo: 000218137
Tipo de artículo: Solution
Última modificación: 08 ene. 2026
Versión: 5
Encuentre respuestas a sus preguntas de otros usuarios de Dell
Servicios de soporte
Compruebe si el dispositivo está cubierto por los servicios de soporte.