NetWorker: AD Users Cannot Sign in Over LDAPS "Could not parse server-response from json string"
Summary: Microsoft Active Directory (AD) authentication was added to NetWorker using the NetWorker Management Console (NMC) External Authority configuration Wizard when using the "LDAP over SSL" option. The configuration was successfully added, but AD user authentication fails with HTTP-ERROR 500. ...
This article applies to
This article does not apply to
This article is not tied to any specific product.
Not all product versions are identified in this article.
Symptoms
- The user is accessing the NetWorker Management Console (NMC) or
nsrlogincommand line and receives an error:
An error occurred while validating user credentials. Verify that NetWorker Authentication Service is running. [POST failed with HTTP-ERROR: 500 Server Message: Could not parse server-response from json string]
- The External Authentication Authority was configured using LDAP over SSL option; however, the authentication server is Microsoft Active Directory:
- Setup > Users and Roles > External Authority > Right-Click External Authority > Properties:
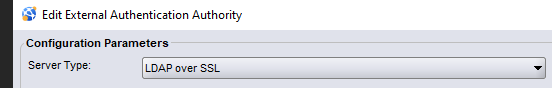
Cause
HTTP Error 500 "Internal Server Error."
When the LDAP over SSL option is selected, it sets an internal attribute Is Active Directory to false. This prevents successful logins for users who are configured in Microsoft Active Directory through NetWorker.
This can be verified from authc_config command line using root or Administrator command prompt:
authc_config -u Administrator -e find-all-configs authc_config -u Administrator -e find-config -D config-id=config_id#
NOTE: You are prompted to enter the NetWorker Administrator account password. The password can also be specified with the command using
-p password.
[root@networker-mc ~]# authc_config -u administrator -p 'Pa$$w0rd01' -e find-all-configs
The query returns 1 records.
Config Id Config Name
2 amer
[root@networker-mc ~]# authc_config -u administrator -p 'Pa$$w0rd01' -e find-config -D config-id=2 | grep -i "is active directory"
Is Active Directory : false
The LDAP over SSL option is not intended for AD over SSL.
Resolution
NOTE: The NetWorker Web User Interface (NWUI) external authority wizard has an AD over SSL option; however, the NMC does not. AD over SSL sets the Is Active Directory parameter to true, while maintaining other secure (LDAPS) settings. See Dell article NetWorker: How to configure "AD over SSL" (LDAPS) from The NetWorker Web User Interface (NWUI)
Workaround:
The authc_config command can be used to update the configuration Is Active Directory value to true.
Windows:
- On the NetWorker (
authc) server, open an Admin command prompt. - Get the configuration ID of the external authority configuration:
authc_config -u Administrator -p NetWorker_Administrator_Password -e find-all-configs
The current settings can be reviewed with:
authc_config -u Administrator -p NetWorker_Administrator_Password -e find-config -D config-id=config_id#
- Update the Is Active Directory value with the following command:
authc_config -u administrator -p NetWorker_Administrator_Password -e update-config -D config-id=config_id# -D "config-active-directory=y" -D "config-server-address=ldaps://domain_server_hostname:636/dc=domain,dc=com" -D config-user-dn=”cn=service_account,ou=some_group,dc=domain,dc=com" -D config-user-dn-password="Service_Account_Password"
NOTE: All required fields except the AD service account password can be collected from
authc_config -u Administrator -e find-config -D config-id=config_id#.
Example:
C:\Users\Administrator.AMER>authc_config -u administrator -p 'Pa$$w0rd01' -e update-config -D config-id=1 -D "config-active-directory=y" -D "config-server-address=ldaps://dc.amer.lan:636/dc=amer,dc=lan" -D "config-user-dn=cn=administrator,cn=users,dc=amer,dc=lan" -D config-user-dn-password="Pa$$w0rd01" Configuration ad is updated successfully. C:\Users\Administrator.AMER>
- AD logins through NetWorker should now complete successfully.
Linux:
- On the NetWorker (
authc) server, open a root command prompt. - Get the configuration ID of the external authority configuration:
authc_config -u Administrator -p 'NetWorker_Administrator_Password' -e find-all-configs
The current settings can be reviewed with:
authc_config -u Administrator -p 'NetWorker_Administrator_Password' -e find-config -D config-id=config_id#
- Create a hidden text file containing the AD service account password:
echo 'Service_Account_Password' > /root/.sapasswd.txt
- Make the file only accessible to root:
chmod 700 /root/.sapasswd.txt
- Create a script to run the call the password from the hidden file and run the
authc_configcommand to update the configuration:
vi authc_update.sh
Example:
PASSWD=`cat /root/.sapasswd.txt` authc_config -u administrator -p 'NetWorker_Administrator_Password' -e update-config -D config-id=config_id# -D "config-active-directory=y" -D "config-server-address=ldaps://domain_server_hostname:636/dc=domain,dc=com" -D config-user-dn=”cn=service_account,ou=some_group,dc=domain,dc=com" -D config-user-dn-password="$PASSWD"
NOTE: Most Linux operating systems do not process the
authc_config command correctly if the service account password is specified in clear text using the command. The failure that is returned is LDAP error code 49 - Data 52e, which appears for invalid username or password. The method that is outlined above can be used to hide the password from clear text input.
- Set permissions on the script so that it is executable:
chmod 755 authc_update.sh
- Run the script:
/authc_update.sh
Example:
[root@nsr ~]# cat authc_update.sh PASSWD=`cat /root/.sapasswd.txt` authc_config -u administrator -p 'Pa$$w0rd01' -e update-config -D config-id=2 -D "config-active-directory=y" -D "config-server-address=ldaps://dc.amer.lan:636/dc=amer,dc=lan" -D "config-user-dn=cn=administrator,cn=users,dc=amer,dc=lan" -D config-user-dn-password="$PASSWD" [root@nsr ~]# chmod 755 authc_update.sh [root@nsr ~]# ./authc_update.sh Configuration AD is updated successfully.
- AD logins through NetWorker should now complete successfully.
Additional Information
If the configuration is updated from the NMC, the Is Active Directory flag is set to false again. If the configuration must be updated, use one of the following methods instead:
- Command-line or script method: NetWorker: How To Set up LDAP/AD using authc_config scripts
- NetWorker Web User Interface: NetWorker: How to configure "AD over SSL" (LDAPS) from The NetWorker Web User Interface (NWUI)
Affected Products
NetWorkerProducts
NetWorker Family, NetWorker SeriesArticle Properties
Article Number: 000204166
Article Type: Solution
Last Modified: 26 Sep 2025
Version: 7
Find answers to your questions from other Dell users
Support Services
Check if your device is covered by Support Services.