L'utente APEX non può generare chiavi S3 da PowerScale Webui
摘要: In OneFS 9.3.0.4, l'account utente APEX del cliente è associato al nuovo ruolo BasicUser e non è in grado di generare chiavi S3 dall'interfaccia utente web di OneFS. La scheda gestione delle chiavi non è visibile per l'account APEX del cliente. ...
本文章適用於
本文章不適用於
本文無關於任何特定產品。
本文未識別所有產品版本。
症狀
Accedere a OneFS webui con l'account APEX del cliente apex01.
Cliccare su Protocols -> Object storage (S3).
Si nota che la scheda Gestione delle chiavi non è visibile.
Esempio:
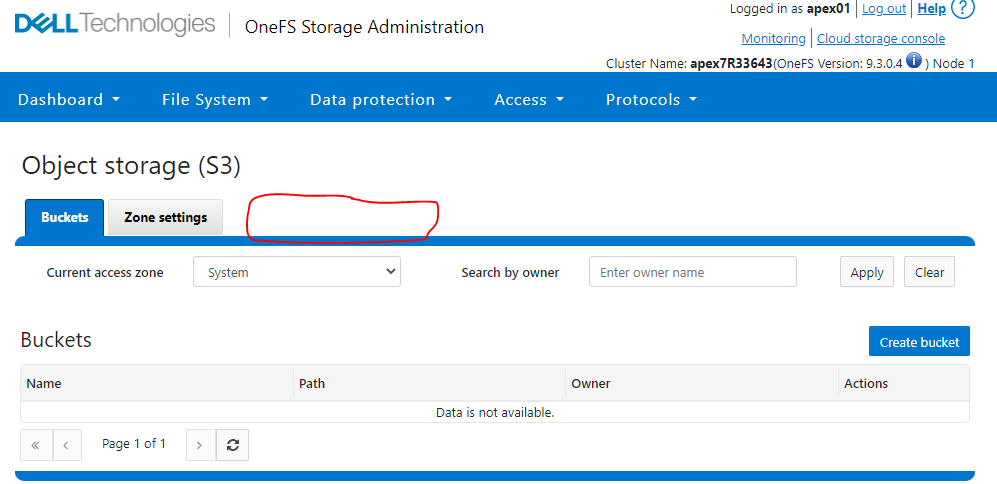
Cliccare su Protocols -> Object storage (S3).
Si nota che la scheda Gestione delle chiavi non è visibile.
Esempio:

原因
L'account del cliente APEX non ha il privilegio di generare chiavi S3 utilizzando l'interfaccia utente web di OneFS.
解析度
Soluzione alternativa api REST per il cliente:
1. Creare una sessione.
2. Generare la chiave S3.
curl -kv -H "Content-type:application/json" -H "X-CSRF-Token: " -H "Referer:https://" -X POST https://:8080/platform/12/protocols/s3/mykeys -b /tmp/cookie.txt
Nota: L'account Apex01 del cliente non dispone dell'accesso alla CLI di PowerScale, pertanto è necessario eseguire la soluzione alternativa da un client NFS o da un prompt dei comandi di Windows con connettività di rete a PowerScale.
Esempio di Laboratorio PowerScale:
1. Creare una sessione:
Node_IP = nome utente X.X.X.X
= password apex01
= la password dell'account utente apex01
2. Genera chiave S3:
Node_IP = X.X.X.X.X
VALORE del token CSRF = 14762d26-e806-41c1-b310-4497afb28953 (vedere sopra evidenziato in rosso dal comando create session)
secret_key = la chiave S3 generata (in verde di seguito)
1. Creare una sessione.
Prompt dei comandi di Windows:
curl --request POST --insecure 'https://:8080/session/1/session' --header 'Content-Type: application/json' --data-raw '{"username": "","password": "","servizi": ["piattaforma","namespace"]}' -v -c /tmp/cookie.txt
CLI client Linux:
curl --request POST --insecure 'https://:8080/session/1/session' --header 'Content-Type: application/json' --data '{"username": "","password": "","servizi": ["piattaforma","namespace"]}' -v -c /tmp/cookie.txt
2. Generare la chiave S3.
curl -kv -H "Content-type:application/json" -H "X-CSRF-Token: " -H "Referer:https://" -X POST https://:8080/platform/12/protocols/s3/mykeys -b /tmp/cookie.txt
Nota: L'account Apex01 del cliente non dispone dell'accesso alla CLI di PowerScale, pertanto è necessario eseguire la soluzione alternativa da un client NFS o da un prompt dei comandi di Windows con connettività di rete a PowerScale.
Esempio di Laboratorio PowerScale:
1. Creare una sessione:
Node_IP = nome utente X.X.X.X
= password apex01
= la password dell'account utente apex01
apex7R33643-3% curl --request POST --insecure 'https://X.X.X.X:8080/session/1/session' --header 'Content-Type: application/json' --data-raw '{"username": "apex01","password": "","services": ["platform","namespace"]}' -v -c /tmp/cookie.txt
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying X.X.X.X:8080...
* Connected to X.X.X.X (X.X.X.X) port 8080 (#0)
* ALPN, offering http/1.1
* Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH
* successfully set certificate verify locations:
* CAfile: none
* CApath: /etc/ssl/certs/
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / DHE-RSA-AES256-SHA
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* start date: Apr 14 20:51:44 2022 GMT
* expire date: Jul 16 20:51:44 2024 GMT
* issuer: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* SSL certificate verify result: self signed certificate (18), continuing anyway.
> POST /session/1/session HTTP/1.1
> Host: X.X.X.X:8080
> User-Agent: curl/7.79.1
> Accept: */*
> Content-Type: application/json
> Content-Length: 83
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 201 Created
< Date: Tue, 21 Jun 2022 13:52:33 GMT
< Server: Apache
< X-Frame-Options: sameorigin
< X-Content-Type-Options: nosniff
< Strict-Transport-Security: max-age=31536000;
* Added cookie isisessid="eyJhbGciOiJQUzUxMiJ9.eyJhdWQiOlsicGxhdGZvcm0iLCJuYW1lc3BhY2UiXSwiZXhwIjoxNjU1ODMzOTUzLCJpYXQiOjE2NTU4MTk1NTMsIm9uZWZzL2NzcmYiOiIxNDc2MmQyNi1lODA2LTQxYzEtYjMxMC00NDk3YWZiMjg5NTMiLCJvbmVmcy9pcCI6IjEyOC4yMjEuMjI3LjMzIiwib25lZnMvbm9uY2UiOjExMTUzNzgyODM1MTU4MjE5ODk0LCJvbmVmcy9zZXNzaW9uIjoiYmZkMjVhMTMtMDNlOS00OTdhLTk2OWYtYmEwZjU1YmFhZTAzIiwib25lZnMvdWEiOiJjdXJsLzcuNzkuMSIsIm9uZWZzL3ppZCI6MSwic3ViIjoiYXBleDAxIn0K.ioRleO4O9kqDcQfzDUpjKDA9bgnpqqSYPQWJ9sDRSfkL0xI1F29YpTvnoa3uKPLZ7pE8sedkk6vpPcif1Tb7L7-9t4fG2kIXJKK7vm1VNNStUFRQMHMc1vaf8UzKwwJJKf0S_3GltOo8iRK2fdkw_bigw2xOwIHr-85YCHGJeYdFiJ2pK_CI_zYPbGAeg5hJFV7Ylci9FDRI8SDElIBe8FrvaZuiPsMloRU8oL4dxco1jAfPhjsv3YOUDXTEq7kI3xCNkKIj5PtQMjQInDz4qxHVNo9Ks7uEm2cjYotNcQ424i0tuGTe2piwdvlaiEC6WaqKo7HhuPEYqQ7vmgK_seCEb9GY6wAXw9xhpfRHb38f2qDohZj17J-6TzKU32PZ9NJutAidTFIVKH01JGOPRRdPM9oex4VH7FUFDhPAGSng1nmBEx6wk10D1LjTB36UbSQ9lkrh7y84DLZYSlJAfo3iX1_w4bZ0tZHa51K13KedLb4E3Jafjkp-MOUUwMMbjXDgxoC0IRWc2HgilDnvKaSe7R8t9vogW0E5m-0jophQD70BY7UioNu-U6CnaoFojQ-yKFS3t6ZV8i40mD3XaZKS5oeePUFWmlmPFEugziuS4dTdQY-_Myei1RhQPRydp_xFUVZyBb79yv71FLtouqB3UY0zy0qiWDip6VRCphc%3D" for domain X.X.X.X, path /, expire 0
< Set-Cookie: isisessid=eyJhbGciOiJQUzUxMiJ9.eyJhdWQiOlsicGxhdGZvcm0iLCJuYW1lc3BhY2UiXSwiZXhwIjoxNjU1ODMzOTUzLCJpYXQiOjE2NTU4MTk1NTMsIm9uZWZzL2NzcmYiOiIxNDc2MmQyNi1lODA2LTQxYzEtYjMxMC00NDk3YWZiMjg5NTMiLCJvbmVmcy9pcCI6IjEyOC4yMjEuMjI3LjMzIiwib25lZnMvbm9uY2UiOjExMTUzNzgyODM1MTU4MjE5ODk0LCJvbmVmcy9zZXNzaW9uIjoiYmZkMjVhMTMtMDNlOS00OTdhLTk2OWYtYmEwZjU1YmFhZTAzIiwib25lZnMvdWEiOiJjdXJsLzcuNzkuMSIsIm9uZWZzL3ppZCI6MSwic3ViIjoiYXBleDAxIn0K.ioRleO4O9kqDcQfzDUpjKDA9bgnpqqSYPQWJ9sDRSfkL0xI1F29YpTvnoa3uKPLZ7pE8sedkk6vpPcif1Tb7L7-9t4fG2kIXJKK7vm1VNNStUFRQMHMc1vaf8UzKwwJJKf0S_3GltOo8iRK2fdkw_bigw2xOwIHr-85YCHGJeYdFiJ2pK_CI_zYPbGAeg5hJFV7Ylci9FDRI8SDElIBe8FrvaZuiPsMloRU8oL4dxco1jAfPhjsv3YOUDXTEq7kI3xCNkKIj5PtQMjQInDz4qxHVNo9Ks7uEm2cjYotNcQ424i0tuGTe2piwdvlaiEC6WaqKo7HhuPEYqQ7vmgK_seCEb9GY6wAXw9xhpfRHb38f2qDohZj17J-6TzKU32PZ9NJutAidTFIVKH01JGOPRRdPM9oex4VH7FUFDhPAGSng1nmBEx6wk10D1LjTB36UbSQ9lkrh7y84DLZYSlJAfo3iX1_w4bZ0tZHa51K13KedLb4E3Jafjkp-MOUUwMMbjXDgxoC0IRWc2HgilDnvKaSe7R8t9vogW0E5m-0jophQD70BY7UioNu-U6CnaoFojQ-yKFS3t6ZV8i40mD3XaZKS5oeePUFWmlmPFEugziuS4dTdQY-_Myei1RhQPRydp_xFUVZyBb79yv71FLtouqB3UY0zy0qiWDip6VRCphc%3D; path=/; HttpOnly; Secure; SameSite=strict
* Added cookie isicsrf="14762d26-e806-41c1-b310-4497afb28953" for domain X.X.X.X, path /, expire 0
< Set-Cookie: isicsrf=14762d26-e806-41c1-b310-4497afb28953; path=/; Secure
< Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data:; script-src 'self' 'unsafe-eval'; style-src 'unsafe-inline' 'self';
< Content-Length: 106
< Content-Type: application/json
<
{"services":["platform","namespace"],"timeout_absolute":14400,"timeout_inactive":900,"username":"apex01"}
* Connection #0 to host X.X.X.X left intact
apex7R33643-3%
2. Genera chiave S3:
Node_IP = X.X.X.X.X
VALORE del token CSRF = 14762d26-e806-41c1-b310-4497afb28953 (vedere sopra evidenziato in rosso dal comando create session)
secret_key = la chiave S3 generata (in verde di seguito)
apex7R33643-3% curl -kv -H "Content-type:application/json" -H "X-CSRF-Token: 14762d26-e806-41c1-b310-4497afb28953" -H "Referer:https://X.X.X.X" -X POST https://X.X.X.X:8080/platform/12/protocols/s3/mykeys -b /tmp/cookie.txt
* Trying X.X.X.X:8080...
* Connected to X.X.X.X (X.X.X.X) port 8080 (#0)
* ALPN, offering http/1.1
* Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH
* successfully set certificate verify locations:
* CAfile: none
* CApath: /etc/ssl/certs/
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / DHE-RSA-AES256-SHA
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* start date: Apr 14 20:51:44 2022 GMT
* expire date: Jul 16 20:51:44 2024 GMT
* issuer: C=US; ST=Washington; L=Seattle; O=Isilon Systems, Inc.; OU=Isilon Systems; CN=Isilon Systems; emailAddress=support@isilon.com
* SSL certificate verify result: self signed certificate (18), continuing anyway.
> POST /platform/12/protocols/s3/mykeys HTTP/1.1
> Host: X.X.X.X:8080
> User-Agent: curl/7.79.1
> Accept: */*
> Cookie: isisessid=eyJhbGciOiJQUzUxMiJ9.eyJhdWQiOlsicGxhdGZvcm0iLCJuYW1lc3BhY2UiXSwiZXhwIjoxNjU1ODMzOTUzLCJpYXQiOjE2NTU4MTk1NTMsIm9uZWZzL2NzcmYiOiIxNDc2MmQyNi1lODA2LTQxYzEtYjMxMC00NDk3YWZiMjg5NTMiLCJvbmVmcy9pcCI6IjEyOC4yMjEuMjI3LjMzIiwib25lZnMvbm9uY2UiOjExMTUzNzgyODM1MTU4MjE5ODk0LCJvbmVmcy9zZXNzaW9uIjoiYmZkMjVhMTMtMDNlOS00OTdhLTk2OWYtYmEwZjU1YmFhZTAzIiwib25lZnMvdWEiOiJjdXJsLzcuNzkuMSIsIm9uZWZzL3ppZCI6MSwic3ViIjoiYXBleDAxIn0K.ioRleO4O9kqDcQfzDUpjKDA9bgnpqqSYPQWJ9sDRSfkL0xI1F29YpTvnoa3uKPLZ7pE8sedkk6vpPcif1Tb7L7-9t4fG2kIXJKK7vm1VNNStUFRQMHMc1vaf8UzKwwJJKf0S_3GltOo8iRK2fdkw_bigw2xOwIHr-85YCHGJeYdFiJ2pK_CI_zYPbGAeg5hJFV7Ylci9FDRI8SDElIBe8FrvaZuiPsMloRU8oL4dxco1jAfPhjsv3YOUDXTEq7kI3xCNkKIj5PtQMjQInDz4qxHVNo9Ks7uEm2cjYotNcQ424i0tuGTe2piwdvlaiEC6WaqKo7HhuPEYqQ7vmgK_seCEb9GY6wAXw9xhpfRHb38f2qDohZj17J-6TzKU32PZ9NJutAidTFIVKH01JGOPRRdPM9oex4VH7FUFDhPAGSng1nmBEx6wk10D1LjTB36UbSQ9lkrh7y84DLZYSlJAfo3iX1_w4bZ0tZHa51K13KedLb4E3Jafjkp-MOUUwMMbjXDgxoC0IRWc2HgilDnvKaSe7R8t9vogW0E5m-0jophQD70BY7UioNu-U6CnaoFojQ-yKFS3t6ZV8i40mD3XaZKS5oeePUFWmlmPFEugziuS4dTdQY-_Myei1RhQPRydp_xFUVZyBb79yv71FLtouqB3UY0zy0qiWDip6VRCphc%3D; isicsrf=14762d26-e806-41c1-b310-4497afb28953
> Content-type:application/json
> X-CSRF-Token: 14762d26-e806-41c1-b310-4497afb28953
> Referer:https://X.X.X.X
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 201 Created
< Date: Tue, 21 Jun 2022 13:54:51 GMT
< Server: Apache
< Allow: GET, POST, DELETE, HEAD
< X-Frame-Options: sameorigin
< X-Content-Type-Options: nosniff
< Strict-Transport-Security: max-age=31536000;
< Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data:; script-src 'self' 'unsafe-eval'; style-src 'unsafe-inline' 'self';
< Transfer-Encoding: chunked
< Content-Type: application/json
<
{
"keys" :
{
"access_id" : "1_apex01_accid",
"secret_key" : "<< SECRET KEY >>>",
"secret_key_timestamp" : 1655819691
}
}
* Connection #0 to host X.X.X.X left intact
apex7R33643-3%
受影響的產品
APEX, APEX Data Storage Services文章屬性
文章編號: 000200704
文章類型: Solution
上次修改時間: 28 6月 2023
版本: 7
向其他 Dell 使用者尋求您問題的答案
支援服務
檢查您的裝置是否在支援服務的涵蓋範圍內。