Dell VxRail:如何在 PSC 上產生 CSR (憑證簽署要求) 和私密金鑰
摘要: 可能需要將 PSC 上的 Vmware SSL 憑證更換為由認證機構產生的客戶憑證。
本文章適用於
本文章不適用於
本文無關於任何特定產品。
本文未識別所有產品版本。
說明
-------------------------------------------------------------------------步驟 1--------------------------------------------------------------------------------------------
步驟 1 - 在 PSC 上產生 CSR (憑證簽署要求) 和私密金鑰:
- 登入 PSC
- SSH 根
- 建立要匯出的目錄並啟動 VMware 憑證工具
注意:VMware 建議僅變更 SSL 機器憑證。不建議變更 ESXi、解決方案使用者等的憑證。
root@ [ ~ ]# pwd /root root@ [ ~ ]# mkdir 憑證
root@ [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
*** Welcome to the vSphere 6.7 Certificate Manager *** |
| -- Select Operation -- |
| 1. Replace Machine SSL certificate with Custom Certificate |
| 2. Replace VMCA Root certificate with Custom Signing Certificate and replace all Certificates |
| 3. Replace Machine SSL certificate with VMCA Certificate |
| 4. Regenerate a new VMCA Root Certificate and replace all certificates |
| 5. Replace Solution user certificates with Custom Certificate |
| 6. Replace Solution user certificates with VMCA certificates |
| 7. Revert last performed operation by re-publishing old certificates
| 8. Reset all Certificates
Note : Use Ctrl-D to exit.
Option[1 to 8]:
- 選擇選項 1 並登入
Note : Use Ctrl-D to exit. Option[1 to 8]: 1 Please provide valid SSO and VC privileged user credential to perform certificate operations. Enter username [Administrator@vsphere.local]: Enter password: 1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate 2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate Option [1 or 2]:
- 完成必填資訊選項 [1 或 2]:1
Please provide a directory location to write the CSR(s) and PrivateKey(s) to: Output directory path: /root/certs Please configure certool.cfg with proper values before proceeding to next step. Press Enter key to skip optional parameters or use Default value. Enter proper value for 'Country' [Default value : US] : Country Enter proper value for 'Name' [Default value : CA] : Name for VC Enter proper value for 'Organization' [Default value : VMware] : DellEMC Enter proper value for 'OrgUnit' [Default value : VMware Engineering] : Services Enter proper value for 'State' [Default value : California] : Country Enter proper value for 'Locality' [Default value : Palo Alto] : DIC Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : IP of VCSA Enter proper value for 'Email' [Default value : email@acme.com] : Email address Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [ Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : VC FQDN Enter proper value for VMCA 'Name' :qpsc 2019-03-20T11:51:14.121Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--genkey', '--privkey', '/root/certs/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub'] 2019-03-20T11:51:14.334Z Done running command 2019-03-20T11:51:14.335Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--gencsr', '--privkey', '/root/certs/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub', '--config', '/var/tmp/vmware/certool.cfg', '--csrfile', '/root/certs/vmca_issued_csr.csr'] 2019-03-20T11:51:14.452Z Done running command CSR generated at: /root/certs/vmca_issued_csr.csr 1. Continue to importing Custom certificate(s) and key(s) for Machine SSL certificate 2. Exit certificate-manager Signing request file is at /root/certs/vmca_issued_csr.csr Option [1 or 2]: 2 root@qpsc [ ~ ]# ls -h /root/certs/ vmca_issued_csr.csr vmca_issued_key.key
- 將生成的 CSR 和 KEY 檔案複製到您的桌面系統,或者只是閱讀更多內容並複製文字。
root@qpsc [ ~ ]# cat /root/certs/vmca_issued_csr.csr-----BEGIN CERTIFICATE REQUEST----- MIIDBDCCAewCAQAwXzENMAsGA1UEAwwEcXBzYzELMAkGA1UEBhMCQUUxDjAMBgNV BAgMBUR1YmFpMQwwCgYDVQQHDANESUMxEDAOBgNVBAoMB0RlbGxFTUMxETAPBgNV BAsMCFNlcnZpY2VzMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAt0f2 EFXQYOTGJ99tJYCLrCPGelLoWQqVcEBtwA6VnOOzRyJr2TX8q9TYgnbXpYwkgH57 OO8Cs663CEUIRqDITbBjPaEUSm3hy68tsH9Y4X+7VKJhx92GSLAuioXUGOzjoIHO SgEI0URwaSRoVQ5TRvFYiIURY8wf5ofTl1pOisKA3VOy2XduKtXCwBh9uA9WOdw0 5MeCbO2P9qcK/MylxHg7WvqXk0KqEC4QQdKtcSCX5U/jaTTwk8YSZ9pjZVkIV9Gc dM7lo4QLJ9Jw2we5+u0doMqhdm/QI30n0fpCRtknIDZCItbZulSsgd8smBfoS5Uj ypTcBiBX4Xig3/oeQwIDAQABoGAwXgYJKoZIhvcNAQkOMVEwTzAuBgNVHREEJzAl gQ5hZG1pbkBkdWJhaS5hZIcECjvzVoINcXBzYy5kdWJhaS5hZDAdBgNVHQ4EFgQU YT9u3+1wEJ7jq9QE6LyrtUwlEsYwDQYJKoZIhvcNAQELBQADggEBAEiG/0v9yV7t EWXJ4yXfvgI44TAA62mJM75ymLf38yPTe4295y3OT5U/q1/sNuwHguyyFAdmpXsd TpocgKYiiSsMZNadXASq0GW1nzKD76geV6v9FgvnWRvHavVLDBwVPZw4+zNMuPaJ SCm8y+Ww/uDReK7PUnVc5ofZI+/DFWXPE3RnIzfL/tyIQf+FD6aemfAaK7ISa1XU kBfgTR2qFU+HKwPyrEufJpWxMWfDk6AQTbpm5P5+P11WQ0ramiF+iriNa3KzMOqG 5X7FAYvVOGTP4L5JpOJ8jP2xi8+diHd0D03IPQ1vYtVncVRxQTcf6axyqPq0F0sq b2vw6oeu7gk= -----END CERTIFICATE REQUEST-----
root@qpsc [ ~ ]# root@qpsc [ ~ ]# cat /root/certs/vmca_issued_key.key-----BEGIN PRIVATE KEY----- MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQC3R/YQVdBg5MYn 320lgIusI8Z6UuhZCpVwQG3ADpWc47NHImvZNfyr1NiCdteljCSAfns47wKzrrcI RQhGoMhNsGM9oRRKbeHLry2wf1jhf7tUomHH3YZIsC6KhdQY7OOggc5KAQjRRHBp JGhVDlNG8ViIhRFjzB/mh9OXWk6KwoDdU7LZd24q1cLAGH24D1Y53DTkx4Js7Y/2 pwr8zKXEeDta+peTQqoQLhBB0q1xIJflT+NpNPCTxhJn2mNlWQhX0Zx0zuWjhAsn 0nDbB7n67R2gyqF2b9AjfSfR+kJG2ScgNkIi1tm6VKyB3yyYF+hLlSPKlNwGIFfh eKDf+h5DAgMBAAECggEAGnBpEKYwbynRZAMZDaXjgCuRAChhmCastAq3SlNQRdeb DxHqGOVu06LasMdQCHOU+GxGfkoMS7tScAD1Vqru+jYNuuA3uxzqy6UzpBhay/zP G0BpdpmAO5AexqDTndzeYVMYXRiVGwsSZDh6THrKjJtYOClp/sl9eJXzcgv29JEn 4jaHa+7JPvtFsQ9oQWLq6gRu59Ytr1KqfiDknHQMGHSXjggaD8hiUkbpe766TemY E0vT8KwLvUlKFB52G/iegDhuX/GBCeqyzshkimt0refsQ+h0cik2VI/d4vlz5Jy+ AWu8IJ3zL5x7J1Ts5IXXjqL+E4PxlVEZm1NSn4jWMQKBgQDa4N/dgpClHdG/MP63 7Iu1gG8I9SFho4NcrBiPjbKOZCvHcmU9L3oRWTTfhapt8cOVmfPueT0wrvd/hJtB +4XT0V8YXzgM4q4S4iC7Qcf6XARgDIrb98IUNod5rsViCVRQkiRui+0vLU0w/iLd 3vPmooyKG0ipAPa6TYdLlv7kDwKBgQDWXYt0qCGfP3nXW58uBpFSR5suGFh63QKa YnTYjCqYJdg7TC/3/VxVfPAZNovXY/ZvnPn0DqzW39nNLTXdDjnR4fKG4+46vSkG 6J639aQSVfGCY94QDWQ60k8iqRm4RUzgkdBBMZU9pzIxDceQ6v/T1J11YsX39Ha1 xkiU15dejQKBgFovC65eTLDr329ShbFMsqffOmDLd6yeTdLSSfBkJu0KkwtDtDkI pdgeFG4Ayh8w3TB31Y0twSuc+/c7sSj3tMV44CDPou2UPLslFu1xBi++2EKnCFPn +ryPVzSo8UUaqPXlsUMnPlwQ41xLahxW79HYqeWBpmeUMRTEOvnHRlC7AoGBAIPP nXKr95CeTWM4+VYpv63iTe84FR/nSjR4GfUVqxNHIgDERjKs3dvLKS+3tKFK3Duh QKjrZSfzGU/qXtaAatk9oA2FlfUUX2faHc5sAukrY4eTtPYV5e2tZ++eHyyJoE3u GyobPPNeHaTAHlhjx88PS4rko2pmLaB0PikXsAH5AoGAFl++M9nQhSVC9vWQKwFb 4zX8SF06rrBwIgvozc8SRqltmDR21BbeQ0vKW+iHtu/FJpnkzLNxSQWYHURr1noF M52YT/4pLmPnIFggCd/MMBpzxg4uBiXaXQI0E6V1SAfJysyrq6mC88q7utm52RWc bMbWTeuNVR7T6bFnhlkzOR4= -----END PRIVATE KEY-----
-------------------------------------------------------------------------步驟 2--------------------------------------------------------------------------------------------
步驟 2 - 建立憑證:
- 就我而言,我正在使用Microsoft AD證書服務。
https://CA Manager/certsrv/ - 選擇要求憑證
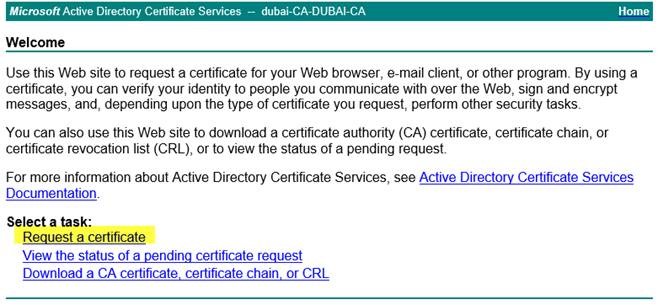
- 選擇進階憑證申請
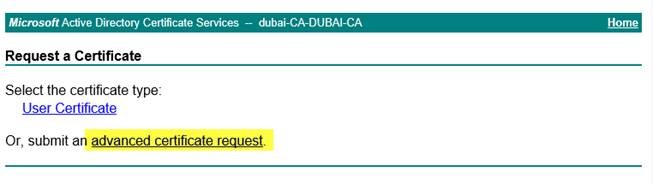
- 選項 2
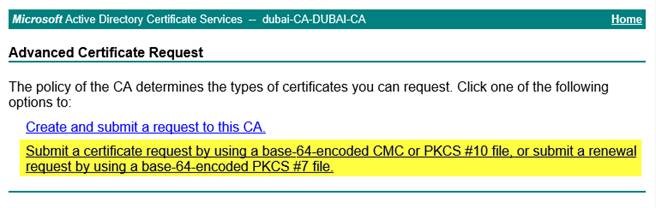
- 粘貼 CSR 中的文字,包括頁眉和頁腳。
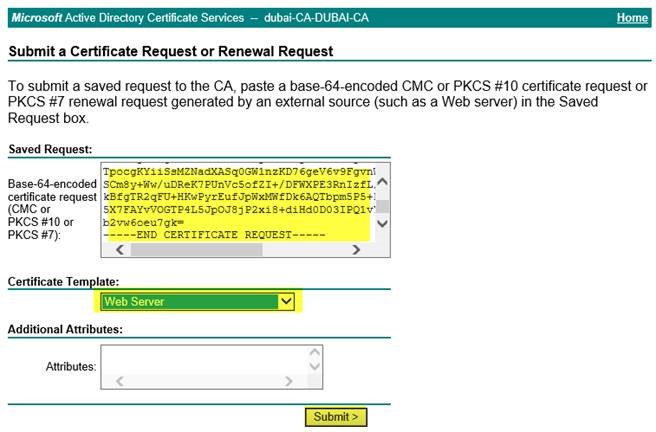
- 將產生的憑證和鏈以 base64 格式下載到您的電腦。

- 將它們下載到本地位置
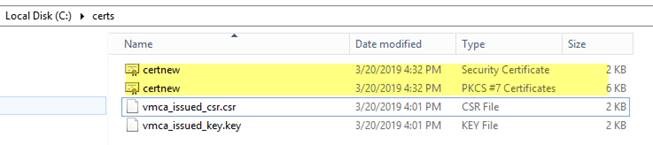
-------------------------------------------------------------------------步驟 3--------------------------------------------------------------------------------------------
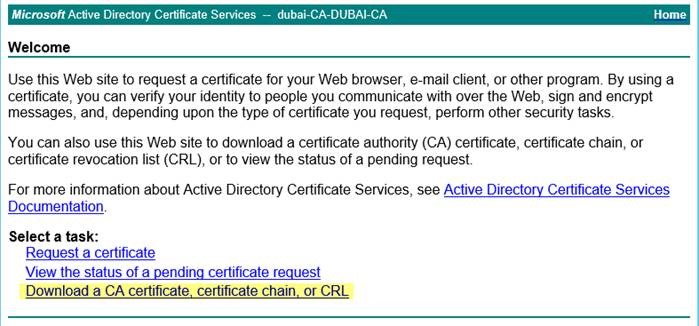
步驟 3 取得 CA 根憑證:
- 返回憑證伺服器頁面: https://CA/certsrv/
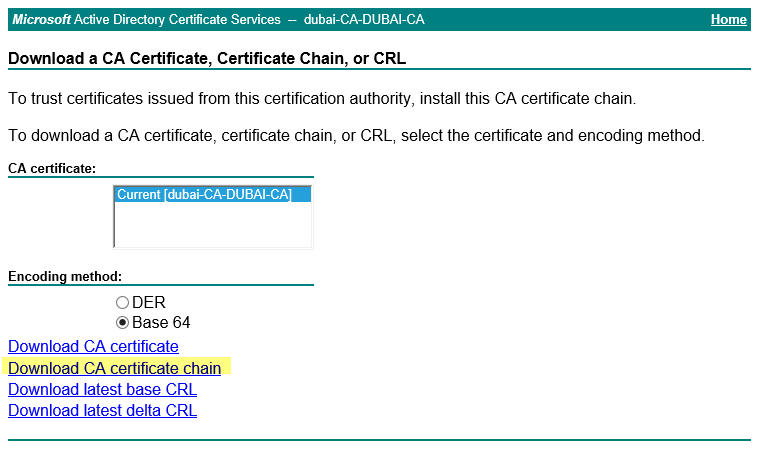
- 下載 CA 憑證,憑證鏈:
- 將鏈儲存為 cachain.p7b。
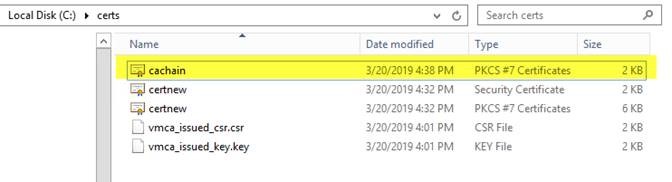
- 使用 certmgr 開啟此檔案並將其匯出至 base64 檔案:
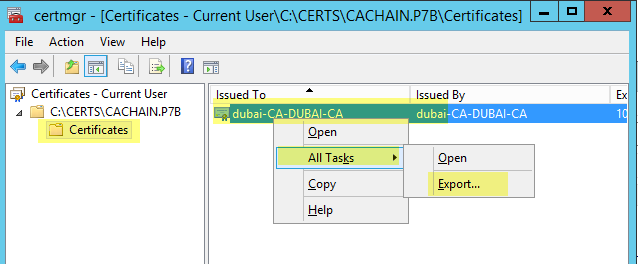
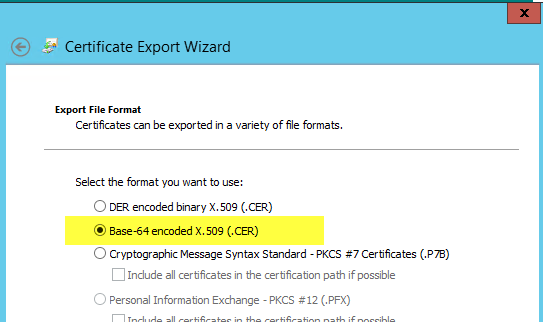
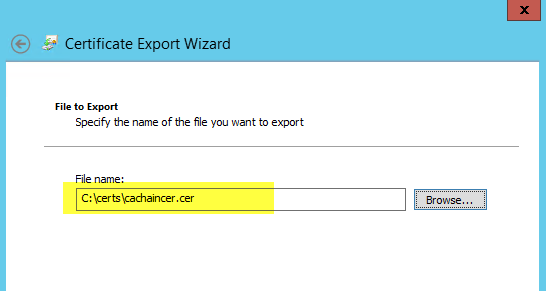
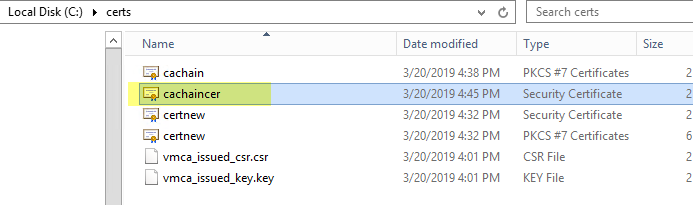
-------------------------------------------------------------------步驟 4--------------------------------------------------------------------------------------------
步驟 4 替換 PSC 上的憑證:
- 使用 WINSCP 將修改的憑證檔案複製到 PSC:
scp /cygdrive/c/certs/* root@:/root/certs/ VMware vCenter Server Appliance 6.7.0.21000 Type: VMware Platform Services Controller cachain.p7b 100% 1328 1.3KB/s 00:00 cachaincer.cer 100% 1266 1.2KB/s 00:00 certnew.cer 100% 2004 2.0KB/s 00:00 certnew.p7b 100% 5238 5.1KB/s 00:00 vmca_issued_csr.csr 100% 1122 1.1KB/s 00:00 vmca_issued_key.key 100% 1703 1.7KB/s 00:00
- 登入回 PSC
SSH root VMware vCenter Server Appliance 6.7.0.21000 輸入:VMware Platform Services Controller
root@qpsc [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
*** Welcome to the vSphere 6.7 Certificate Manager *** |
| -- Select Operation -- |
| 1. Replace Machine SSL certificate with Custom Certificate |
| 2. Replace VMCA Root certificate with Custom Signing Certificate and replace all Certificates |
| 3. Replace Machine SSL certificate with VMCA Certificate |
| 4. Regenerate a new VMCA Root Certificate and replace all certificates |
| 5. Replace Solution user certificates with Custom Certificate |
| 6. Replace Solution user certificates with VMCA certificates |
| 7. Revert last performed operation by re-publishing old certificates
| 8. Reset all Certificates
Note : Use Ctrl-D to exit.
Option[1 to 8]:
- 選擇選項 1 後登入
Option[1 to 8]: 1 Please provide valid SSO and VC privileged user credential to perform certificate operations. Enter username [Administrator@vsphere.local]: Enter password: 1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate 2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate Option [1 or 2]: Import custom: Option [1 or 2]: 2 Please provide valid custom certificate for Machine SSL. File : /root/certs/certnew.cer Please provide valid custom key for Machine SSL. File : /root/certs/vmca_issued_key.key Please provide the signing certificate of the Machine SSL certificate File : /root/certs/cachaincer.cer You are going to replace Machine SSL cert using custom cert Continue operation : Option[Y/N] ? : Y Command Output: /root/certs/certnew.cer: OK Get site nameCompleted [Replacing Machine SSL Cert...] default-first-site Lookup all services Get service default-first-site:c8b2c8ae-96a0-4104-aecd-b54df3676574 Update service default-first-site:c8b2c8ae-96a0-4104-aecd-b54df3676574; spec: /tmp/svcspec_t8ya_1yk Get service default-first-site:0b3330ad-5ad9-4754-8756-4cb1ebd8d11a Update service default-first-site:0b3330ad-5ad9-4754-8756-4cb1ebd8d11a; spec: /tmp/svcspec_wgnl6ln8 ...................................... ..................................... Get service 684e18e9-bbb5-4054-95aa-53a1d75449dc Update service 684e18e9-bbb5-4054-95aa-53a1d75449dc; spec: /tmp/svcspec_nudv5jgy Get service a5516943-a60c-463e-915c-19c7a55b771e_com.vmware.vxrail Don't update service a5516943-a60c-463e-915c-19c7a55b771e_com.vmware.vxrail Get service b79e1e3f-42c7-4e96-80df-ea6459560d91 Don't update service b79e1e3f-42c7-4e96-80df-ea6459560d91 Get service c4f48c92-184a-4cd9-85c6-b4ed89273fa5 ...................................... ..................................... Get service 76f0982a-ec9a-48e2-9180-0730bce9d05e_kv Don't update service 76f0982a-ec9a-48e2-9180-0730bce9d05e_kv Get service 3474fde1-bbdc-48a3-923b-5be4970b00b8 Don't update service 3474fde1-bbdc-48a3-923b-5be4970b00b8 Updated 11 service(s) Status : 100% Completed [All tasks completed successfully] Please restart all services in associated vCenter Server/s for changes made in Platform Service Controller machine to reflect Perform restart operation on the vCenter Server/s by using 'service-control --stop --all' and 'service-control --start --all'
- 等待幾分鐘,確認 PSC 使用憑證,然後檢查 VCSA Web 用戶端 (仍應提供憑證警告)
其他資訊
若要更換憑證,請遵循知識庫文章:000528684
受影響的產品
VxRail Appliance Family, VxRail E460, VxRail V470產品
VxRail Appliance Family文章屬性
文章編號: 000023142
文章類型: How To
上次修改時間: 09 1月 2025
版本: 7
向其他 Dell 使用者尋求您問題的答案
支援服務
檢查您的裝置是否在支援服務的涵蓋範圍內。