PowerScale: Netlogon RPC Elevation of Privilege Vulnerability (CVE-2022-38023)
Summary: CVE-2022-38023 has no functional impact on PowerScale clients. OneFS should be upgraded to 9.5 or later to use AES cryptography for Netlogon.
Symptoms
PowerScale OneFS uses Netlogon as a secure channel to communicate with Active Directory. This article provides some information about the impact of CVE-2022-38023 on PowerScale OneFS.
Here is the Microsoft Security Vulnerability announcement for CVE-2022-38023, Netlogon RPC Elevation of Privilege Vulnerability
Microsoft released an update on November 8, 2022 that introduced the following system registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\RequireSeal
That has three values:
0 – Disabled 1 – Compatibility mode. Windows domain controllers will require that Netlogon clients use RPC Seal if they are running Windows, or if they are acting as either domain controllers or Trust accounts. 2 - Enforcement mode. All clients are required to use RPC Seal, unless they are added to the "Domain Controller: Allow vulnerable Netlogon secure channel connections” group policy object (GPO).
PowerScale OneFS, by default, signs, and seals the Netlogon secure channel connection Requiring Netlogon sealing due to CVE-2022-38023 does not impact PowerScale OneFS.
You may see the following events logged in the Windows Event Viewer of the domain controllers:
| Event ID | 5840 |
| Event Text | The Netlogon service created a secure channel with a client with RC4. |
A New Event ID 5840 is created with PowerScale clients running OneFS releases 9.4.x and earlier which use RC4 by default for NTLM Netlogon Secure Channel.
A New Event ID 5840 is not created with PowerScale OneFS clients running releases 9.5.0 and later. PowerScale OneFS 9.5.0 uses AES cryptography for NTLM Netlogon.
Cause
Resolution
These updates to Windows by Microsoft to address CVE-2022-38023 have no functional impact to PowerScale OneFS clients running any supported release since 7.x.
To take advantage of AES cryptography for NTLM Netlogon Secure Channel in OneFS, upgrade to PowerScale OneFS release 9.5.0 or later.
The support of AES cryptography for NTLM Netlogon Secure Channel is not being backported to PowerScale OneFS releases 9.4.x and earlier.
Related Resources
Here are recommended resources related to this topic that may be of interest:
- Dell article 152189, PowerScale OneFS Info Hubs
- Dell article 184794, PowerScale OneFS Current Patches
- Dell article 63022, PowerScale: OneFS: Best practices for NFS client settings
Additional Information
The following registry value does not apply by default and does not cause any authentication failures unless deliberately enabled:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Netlogon\Parameters\RejectMd5Clients
If the value is deliberately set to TRUE (1), this does result in NTLM authentication failures on OneFS releases 9.4.x and earlier.
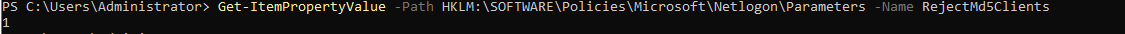
Verify the setting by running the following PowerShell command:
Get-ItemPropertyValue -Path HKLM:\SOFTWARE\Policies\Microsoft\Netlogon\Parameters -Name RejectMd5Clients
Example output of it being enabled:
For OneFS 9.4 and earlier and if the RejectMd5Clients value is enabled, you see similar errors in /var/log/lsassd.log for a failed NTLM authentication:
2023-05-03T10:55:18.847247-06:00 <30.4> vd9400-1(id1) lsass[24440]: [lsass] Failed to get Ntlm Target Info Type for 'TRUSTED.INT' Error code: 40134 (symbol: LW_ERROR_RPC_ERROR) 2023-05-03T10:55:18.855332-06:00 <30.3> vd9400-1(id1) lsass[24440]: [lsass] AD_NetrlogonOpenSchannel(WIN-871N98FR.trusted.int) failed with 3221226376 (0xc0000388) (symbol: 'STATUS_DOWNGRADE_DETECTED') 2023-05-03T10:55:18.855438-06:00 <30.3> vd9400-1(id1) lsass[24440]: [lsass] Failed to authenticate user (name = 'administrator') -> error = 40134, symbol = LW_ERROR_RPC_ERROR, client pid = 4294967295