IDPA: iDRAC UI fails to connect in browser using FQDN after 2.7.2 upgrade
Summary: (CVE-2021-21510) - Dell EMC iDRAC9 versions prior to IDPA 2.7.2 contain a host header injection vulnerability. A remote unauthenticated attacker may potentially exploit this vulnerability by injecting arbitrary 'Host' header values to poison a web-cache or trigger redirections. After IDPA v.2.7.2 upgrade, connection to iDRAC using only Fully Qualified Domain Name (FQDN) will fail to connect. Connecting using IP works as intended. ...
Symptoms
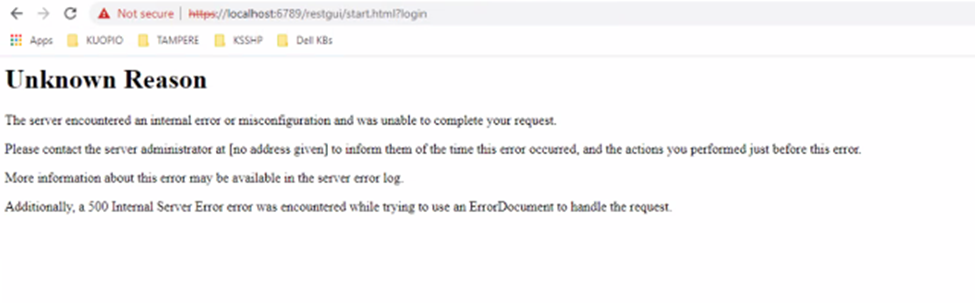
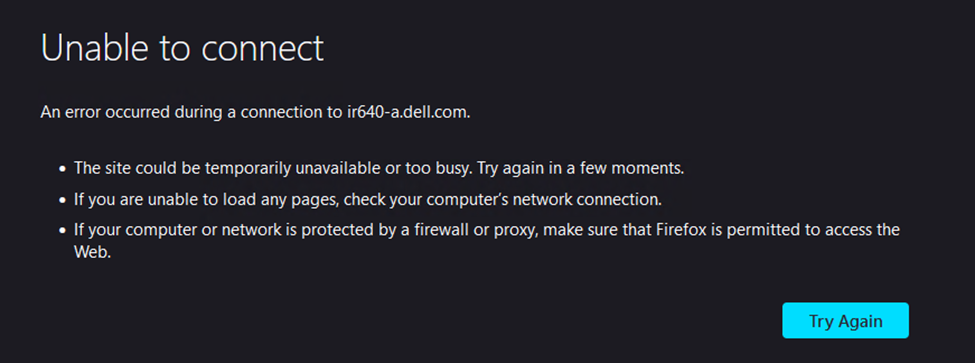
When accessing the iDRAC UI using FQDN after a v.2.7.2 upgrade, the browser fails with connectivity issues like redirection, '400 - Bad Request' errors or Unknown Reason.
Cause
IDPA 2.7.2 block contains iDRAC firmware version 5.10.00.00 which introduced HTTPS connection changes as part of the CVE-2021-21510 fix. The webserver in iDRAC firmware version 5.10.00.00 enforces an HTTPS Host Header check by default.
This also impacts Fully Qualified Domain Name (FQDN) addresses.
Resolution
DP4400 iDRAC can be accessed by using configured IP as expected. No other changes are required. iDRAC is no longer accessible by FQDN.
See the PowerProtect DP4400 Installation Guide for steps to configure networking, as was meant to be performed at initial deployment.
DP5x00 and DP8x00 are not deployed with external connection by default.