ECS:如何配置 ECS SNMP 陷阱
摘要: SNMP 陷阱由 ECS 上的任何一个生命周期节点生成。 以下知识库文章介绍了如何识别活动生命周期节点并生成测试警报以生成陷阱事件。
本文适用于
本文不适用于
本文并非针对某种特定的产品。
本文并非包含所有产品版本。
说明
SNMP 陷阱由 ECS 上的任何一个生命周期节点生成。 以下知识库文章介绍了如何识别活动生命周期节点并生成测试警报以生成陷阱事件。
要配置和重新创建 SNMP 陷阱发送,请执行以下操作:
提醒: 任何生命周期服务器节点都可以触发陷阱,因为它们作为整体同步,并且所有节点都具有结构代理程序来更新节点和资源的状态。
ECS 3.1 管理指南有关陷阱的其他信息:
ECS 3.7 管理指南(dell.com)(第 149-155 页)
在大多数监视解决方案中进行 OID 转换需要 MIB:
https://dl.dell.com/downloads/DL79351_ECS-MIB.mib
要配置和重新创建 SNMP 陷阱发送,请执行以下操作:
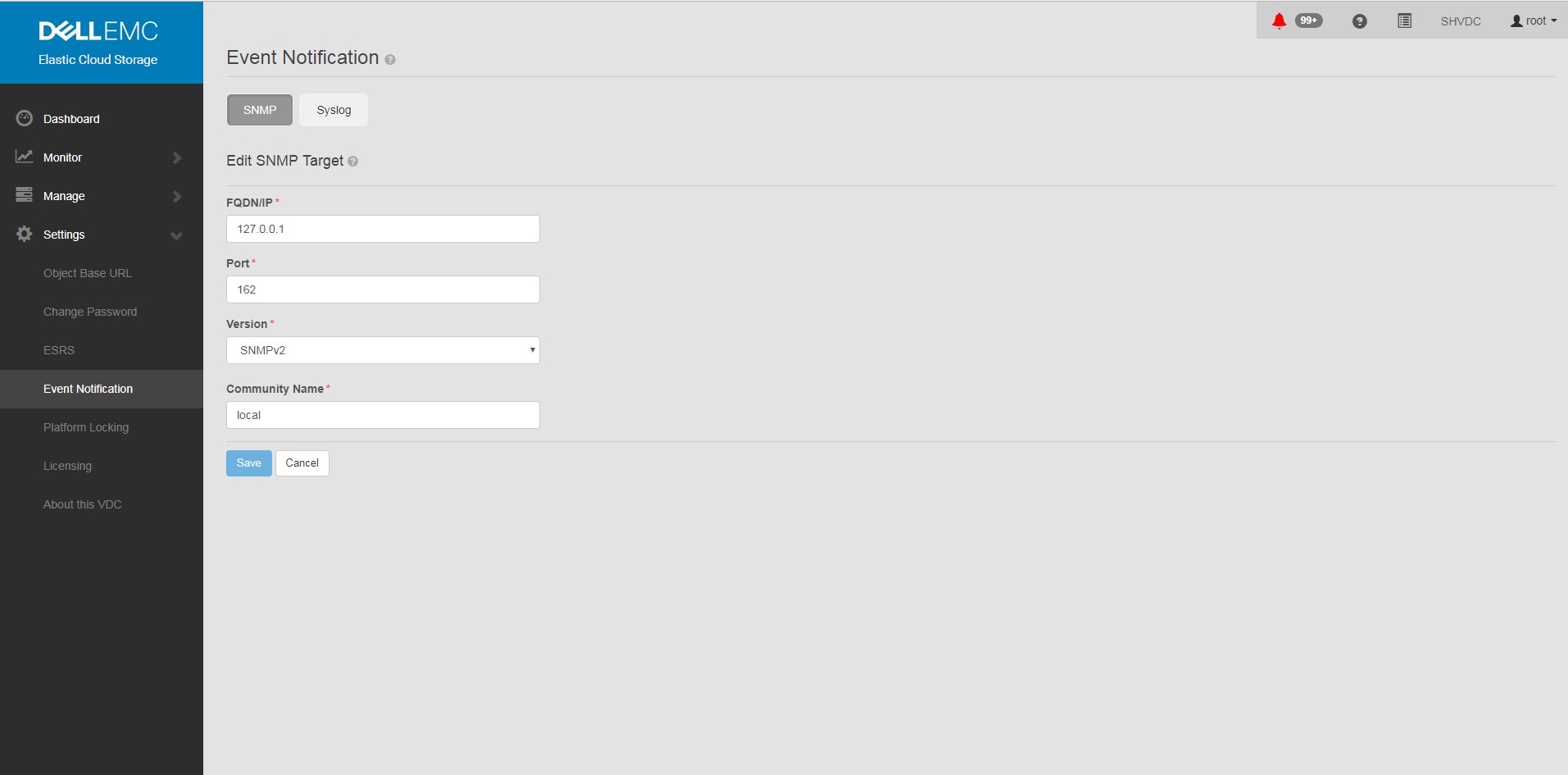
- 在 GUI 中将 SNMP 设置为<陷阱接收器地址>
一个。GUI
中的设置 b. 事件通知
c. 选择 SNMP
d.New Target
FQDN/IP = <trap receiver address>
Port= 162
Version= SNMPv2
Community Name= <community string>
Save
中的设置 b. 事件通知
c. 选择 SNMP
d.New Target
FQDN/IP = <trap receiver address>
Port= 162
Version= SNMPv2
Community Name= <community string>
Save
示例:

- 在UI中添加陷阱配置后,确认在ECS上设置了配置。
命令:
示例:
# sudo /opt/emc/caspian/fabric/cli/bin/fcli-internal lifecycle alert.snmpconfiguration
示例:
Node 1:~ # sudo /opt/emc/caspian/fabric/cli/bin/fcli-internal lifecycle alert.snmpconfiguration
{
"status": "OK",
"etag": 73523,
"snmp_configuration": {
"engine_id": "80001370010A20A9799527B54B",
"snmp_targets": [{
"version": "v2",
"port": 162,
"hostname": "127.0.0.1",
"community": "local",
"username": "",
"target_id": "816bd926-147e-4309-bf69-492eea94fc7a",
"authentication_protocol": "",
"privacy_protocol": ""
}]
}
}
- 运行 test alert 命令以生成警报和 SNMP 陷阱。
命令(请注意,您需要更改为正确的用户和密码):
示例:
# TOKEN=$(curl -iks https://localhost:4443/login -u '<User:Password>' | grep X-SDS-AUTH-TOKEN);echo $TOKEN;curl -ks -H "$TOKEN" -H "Content-Type: application/json" -d '{"user_str": "ECS Test Alert", "contact": "ecsadmin@company.com"}' https://localhost:4443/vdc/callhome/alert | xmllint --format -;curl -vk -H "$TOKEN" "https://localhost:4443/logout"
示例:
admin@provo:~> TOKEN=$(curl -iks https://localhost:4443/login -u 'root:ChangeMe' | grep X-SDS-AUTH-TOKEN);echo $TOKEN;curl -ks -H "$TOKEN" -H "Content-Type: application/json" -d '{"user_str": "ECS Test Alert", "contact": "ecsadmin@company.com"}' https://localhost:4443/vdc/callhome/alert | xmllint --format -;curl -vk -H "$TOKEN" "https://localhost:4443/logout"
X-SDS-AUTH-TOKEN: BAAcSWx4M3IvY0p6VFBCTUtTaE9zdmFVSVFZNFdNPQMAjAQASHVybjpzdG9yYWdlb3M6VmlydHVhbERhdGFDZW50ZXJEYXRhOmZkYzJhMDg2LTQzMGEtNGU3ZC04ZmNiLTU2MDA3ZDFmOWU4NgIADTE1NTM1NDgzNjk5ODEDAC51cm46VG9rZW46YzQ3ZmUwYzYtZjg3Ni00OTE5LWJkMWYtZDgyMjYwN2I2MmIwAgAC0A8=
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<alert>
<acknowledged>false</acknowledged>
<type>Notify</type>
<description>ECS Test Alert: ecsadmin@company.com</description>
<id>urn:storageos:Alert:bbb02b69-0169-1355-a40a-c1f3512e51cd</id>
<namespace/>
<severity>INFO</severity>
<symptomCode>999</symptomCode>
<timestamp>2019-03-26T20:27:58</timestamp>
</alert>
* SSL connection using TLSv1.2 / ECDHE-RSA-AES256-GCM-SHA384
* Server certificate:
* subject: CN=localhost
* start date: 2018-02-28 10:53:28 GMT
* expire date: 2028-02-26 10:53:28 GMT
* issuer: CN=localhost
* SSL certificate verify result: self signed certificate (18), continuing anyway.
* SSLv2, Unknown (23):
> GET /logout HTTP/1.1
> User-Agent: curl/7.37.0
> Host: localhost:4443
> Accept: */*
> X-SDS-AUTH-TOKEN: BAAcSWx4M3IvY0p6VFBCTUtTaE9zdmFVSVFZNFdNPQMAjAQASHVybjpzdG9yYWdlb3M6VmlydHVhbERhdGFDZW50ZXJEYXRhOmZkYzJhMDg2LTQzMGEtNGU3ZC04ZmNiLTU2MDA3ZDFmOWU4NgIADTE1NTM1NDgzNjk5ODEDAC51cm46VG9rZW46YzQ3ZmUwYzYtZjg3Ni00OTE5LWJkMWYtZDgyMjYwN2I2MmIwAgAC0A8=
>
* SSLv2, Unknown (23):
< HTTP/1.1 200 OK
< Date: Tue, 26 Mar 2019 20:27:58 GMT
< Content-Type: application/xml
< Content-Length: 95
< Connection: keep-alive
<
* Connection #0 to host localhost left intact
<?xml version="1.0" encoding="UTF-8" standalone="yes"?><LoggedOut><user>root</user></LoggedOut>
- 运行以下命令以查看陷阱是否已离开群集中的另一个生命周期节点,因为日志条目将具有最新的日期。
命令:
示例(请注意,节点 3 已记录陷阱发送):
# domulti 'grep -i snmp /opt/emc/caspian/fabric/agent/services/fabric/lifecycle/log/lifecycle.log'
示例(请注意,节点 3 已记录陷阱发送):
admin@provo:~> domulti 'grep -i snmp /opt/emc/caspian/fabric/agent/services/fabric/lifecycle/log/lifecycle.log | grep 2017-12-11'
192.168.219.1
========================================
192.168.219.2
========================================
192.168.219.3
========================================
2017-12-11 18:10:48,849 1419726792 [qtp1183213894-166677] DEBUG com.emc.caspian.fabric.lifecycle.alert.snmp.TrapSenderV2::<init> (line: 51) - 36827218-dcc3-4d44-b843-1fdcedc3899c Created trap sender SnmpV2CTarget[hostname=127.0.0.1, port=162, version=v2]
2017-12-11 18:10:48,856 1419726799 [qtp1183213894-166677] DEBUG com.emc.caspian.fabric.lifecycle.alert.snmp.TrapSenderV2::sendTrap (line: 85) - 36827218-dcc3-4d44-b843-1fdcedc3899c Sent trap: pdu TRAP[requestID=143015719, errorStatus=Success(0), errorIndex=0, VBS[1.3.6.1.2.1.1.3.0 = 113 days, 3:54:55.25; 1.3.6.1.6.3.1.1.4.1.0 = 1.3.6.1.4.1.1139.102.1.1; 1.3.6.1.4.1.1139.102.0.1.1 = Mon Dec 11 18:10:48 UTC 2017; 1.3.6.1.4.1.1139.102.0.1.2 = Info; 1.3.6.1.4.1.1139.102.0.1.3 = 999; 1.3.6.1.4.1.1139.102.0.1.4 = ECS Test Alert: ecsadmin@company.com]], target: CommunityTarget[address=127.0.0.1/162,version=1,timeout=5000,retries=2,securityLevel=1,securityModel=1,securityName=local,preferredTransports=null], snmp: org.snmp4j.Snmp@6e6f15f3, transport: org.snmp4j.transport.DefaultUdpTransportMapping@122299ef
2017-12-11 18:10:48,857 1419726800 [qtp1183213894-166677] INFO com.emc.caspian.fabric.lifecycle.alert.snmp.SnmpAgent::sendAlert (line: 400) - 36827218-dcc3-4d44-b843-1fdcedc3899c Sent alert Event[symptomCode=999, category=CONFIGURATION, severity=INFO, status=UNKNOWN, component=Object, componentId=, subComponent=Notify, subComponentId=, callHome=true, firstTime=1513015848814, lastTime=1513015848814, count=0, eventData=, description=ECS Test Alert: ecsadmin@company.com, channel=ALL] to SNMP target: SnmpV2CTarget[hostname=127.0.0.1, port=162, version=v2]
192.168.219.4
========================================
grep: /opt/emc/caspian/fabric/agent/services/fabric/lifecycle/log/lifecycle.log: No such file or directory
- 在第二个 putty 窗口中,通过 ssh 进入在最新日志中恢复的节点,并运行以下命令。
命令:
# tcpdump udp -i any port 162
- 在主窗口中,运行以下命令以生成测试陷阱:
命令(请注意,您需要更改为正确的用户和密码):
示例:
# TOKEN=$(curl -iks https://localhost:4443/login -u '<User:Password>' | grep X-SDS-AUTH-TOKEN);echo $TOKEN;curl -ks -H "$TOKEN" -H "Content-Type: application/json" -d '{"user_str": "ECS Test Alert", "contact": "ecsadmin@company.com"}' https://localhost:4443/vdc/callhome/alert | xmllint --format -;curl -vk -H "$TOKEN" "https://localhost:4443/logout"
示例:
admin@provo:~> TOKEN=$(curl -iks https://localhost:4443/login -u 'root:ChangeMe' | grep X-SDS-AUTH-TOKEN);echo $TOKEN;curl -ks -H "$TOKEN" -H "Content-Type: application/json" -d '{"user_str": "ECS Test Alert", "contact": "ecsadmin@company.com"}' https://localhost:4443/vdc/callhome/alert | xmllint --format -;curl -vk -H "$TOKEN" "https://localhost:4443/logout"
X-SDS-AUTH-TOKEN: BAAcUWtmaTU0OEo0M21EYW1oSHVLa2dacFUyVTFjPQMAjAQASHVybjpzdG9yYWdlb3M6VmlydHVhbERhdGFDZW50ZXJEYXRhOjI1ZTU1NDY3LWNiMTMtNGM5NC05NGZjLWMzNjBjYjRhNjExYgIADTE1MTI4OTA0NjExODQDAC51cm46VG9rZW46MTYzNzA2ZTgtNTI1Zi00NjgwLWJkYmItZjYyYWM0MjQ1YzViAgAC0A8=
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<alert>
<acknowledged>false</acknowledged>
<type>Notify</type>
<description>ECS Test Alert: ecsadmin@company.com</description>
<id>urn:storageos:Alert:46c9fdf1-0160-13fc-b8df-7c7be33092f3</id>
<namespace/>
<severity>INFO</severity>
<symptomCode>999</symptomCode>
<timestamp>2017-12-11T18:15:31</timestamp>
</alert>
- 在第二个窗口中,您应该会看到生命周期节点发出的陷阱。如果陷阱未显示,请重新检查步骤 4 中的日志,因为响应的 zookeeper 节点可能已更改。
示例(请注意,在本例中,我们在生成陷阱时将节点 3 标识为陷阱发送节点):
admin@murray:~> tcpdump udp -i any port 162
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
18:15:37.050102 IP localhost.33530 > localhost.snmptrap: C="local" V2Trap(198) system.sysUpTime.0=977758344 S:1.1.4.1.0=E:1139.102.1.1 E:1139.102.0.1.1="Mon Dec 11 18:15:37 UTC 2017" E:1139.102.0.1.2="Info" E:1139.102.0.1.3="999" E:1139.102.0.1.4="ECS Test Alert: ecsadmin@company.com"
提醒: 任何生命周期服务器节点都可以触发陷阱,因为它们作为整体同步,并且所有节点都具有结构代理程序来更新节点和资源的状态。
ECS 3.1 管理指南有关陷阱的其他信息:
ECS 3.7 管理指南(dell.com)(第 149-155 页)
在大多数监视解决方案中进行 OID 转换需要 MIB:
https://dl.dell.com/downloads/DL79351_ECS-MIB.mib
受影响的产品
ECS Appliance产品
ECS Appliance Hardware Gen1 U-Series, ECS Appliance Software with Encryption, ECS Appliance Software without Encryption文章属性
文章编号: 000019915
文章类型: How To
上次修改时间: 18 1月 2023
版本: 3
从其他戴尔用户那里查找问题的答案
支持服务
检查您的设备是否在支持服务涵盖的范围内。