Article Number: 000052262
Dell EMC Unity: GPO policies are not enforced correctly
Article Content
Symptoms
Change at domain controller
Customer reported that, GPO (Group Policy Object) policies are not behaving as expected.
Scenario with example:
Customer has 2 CIFS Servers (cifs100 and cifs200) in an OU, called "ou=EMC" and the OU has following 2 GPOs:
- all_servers_gpo
- cifs200_only_gpo
all_servers_gpo : Security filter is set to "Authenticated Users"
cifs200_only_gpo : Security filter set only to "cifs200$" computer account
Problem:
Customer noticed that, cifs200_only_gpo is also applied on cifs100 which is incorrect.
Customer reported that, GPO (Group Policy Object) policies are not behaving as expected.
Scenario with example:
Customer has 2 CIFS Servers (cifs100 and cifs200) in an OU, called "ou=EMC" and the OU has following 2 GPOs:
- all_servers_gpo
- cifs200_only_gpo
all_servers_gpo : Security filter is set to "Authenticated Users"
cifs200_only_gpo : Security filter set only to "cifs200$" computer account
Problem:
Customer noticed that, cifs200_only_gpo is also applied on cifs100 which is incorrect.
Cause
VNX/Unity follows standard ldap queries and apply the GPOs that it has access to.
1) Queries LDAP for CIFS Servers OU
2) Queries for all policies listed under that OU using "cifs server" account
3) Above should list only what is permitted and gets applied as per GPO link order
In customer case, cifs200_only_gpo is returned for other cifs server's query as well, which is why it got applied.
Customer recently patched the domain controller and that impacted how GPOs applied on (specifically Microsoft) Servers
This is documented in Microsoft KB 3159398 :
MS16-072 changes the security context with which user group policies are retrieved. This by-design behavior change protects customers computers from a security vulnerability. Before MS16-072 is installed, user group policies were retrieved by using the user s security context. After MS16-072 is installed, user group policies are retrieved by using the computer's security context
The KB suggested following workaround:
To resolve this issue, use the Group Policy Management Console (GPMC.MSC) and follow one of the following steps:
1) Queries LDAP for CIFS Servers OU
2) Queries for all policies listed under that OU using "cifs server" account
3) Above should list only what is permitted and gets applied as per GPO link order
In customer case, cifs200_only_gpo is returned for other cifs server's query as well, which is why it got applied.
Customer recently patched the domain controller and that impacted how GPOs applied on (specifically Microsoft) Servers
This is documented in Microsoft KB 3159398 :
MS16-072 changes the security context with which user group policies are retrieved. This by-design behavior change protects customers computers from a security vulnerability. Before MS16-072 is installed, user group policies were retrieved by using the user s security context. After MS16-072 is installed, user group policies are retrieved by using the computer's security context
The KB suggested following workaround:
To resolve this issue, use the Group Policy Management Console (GPMC.MSC) and follow one of the following steps:
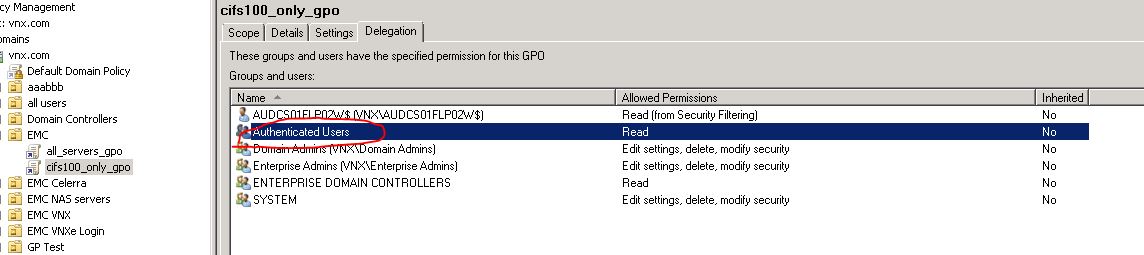
- Add the Authenticated Users group with Read Permissions on the Group Policy Object (GPO).
- If you are using security filtering, add the Domain Computers group with read permission.

Resolution
Request customer (domain admin) to remove the "Authenticated Users" (or anything else that should not exist) under GPO Link's Delegation tab. Only the Computer object (like cifsserver$) should be present
Following ldap search (available on all control stations) using any normal user account should not display the restricted policy:
$ ldapsearch -h <domain_controller_ip> -b "cn=policies,cn=system,dc=<domain>" -D 'domain\anyuser' -w <password> -x | egrep "displayName"
CIFS servers will automatically refresh this change in about 90 minutes, but can also refreshed immediate in VNX by "server_security server_2 -update -policy gpo"
Article Properties
Product
Unity All Flash
Last Published Date
20 Nov 2020
Version
2
Article Type
Solution