Article Number: 000137106
Security Scanner Malware Removal Guide
Summary: This article provides information about removing the Security Scanner Malware from your Dell computer. Most of the steps here are not covered under your warranty and are carried out at your own risk. ...
Article Content
Symptoms
Table of Contents:
- A description of what a Security Scanner is and the support possible under the warranty
- Removal Instructions
- Associated Security Scanner Files
- Associated Security Scanner Registry Information
- Prevent Re-Infection
A description of what a Security Scanner is and the support possible under the warranty
The Security Scanner software is malware and is similar to the Security Shield malware. It is a rogue anti-spyware program. It does a fake scan of your computer and displays false alerts. It stops you running any applications. This would get on your computer through either viruses or by visiting a website that is trying to exploit security holes on your computer. It installs without your knowledge or permission. It adds itself to your computer as a randomly named file. It locates itself in C:\Documents and Settings\Local Settings\Application Data\ if you are running XP or C:\Users\AppData\Local\, if you are running a more recent operating system.
The surest way to resolve this issue is to either perform a factory restore or a clean operating system install on your computer. Taking you through this reinstall is covered under your pro support warranty. You can also find articles taking you through this for your particular operating system and situation on the appropriate link page below:

The malware scans your computer and reports numerous infected files on your computer. Before it allows you to remove these infections, it advises that you have to buy the program first. Do not purchase the program. All the reports are false.
To stop you from removing it and to make you think your computer is about to stop responding. It stops any programs that you try to run. Every time it stops a program, it brings up alert messaging saying that the program was infected. They state that you should buy a Security Scanner to remove the infection.
"winword.exe" is infected with "Backdoor:Win32/Samsteal.A.dr". Do you want to register your copy and remove all threats now?
It reports infections like:
- Backdoor: Win 32
- Hackdef.O
- Virus.DOS.Lct.599
- Virus.DOS.Silver.2071
- Virus.DOS.Zerobug.1536.a
- TrojanWin32.KillWin.bl
- Backdoor.Win32.RA-based
- TrojanWin32.Killav.k
- Backdoor.WinCE.Brador.a
As with the scan results, ignore this messaging.
There are various alert messagings seen, such as:
Security Scanner Warning Spyware.IEMonster process is found. This is a virus that is trying to send your passwords from Internet browser (Explorer, Mozilla Firefox, Outlook & others) for the third-parties. Click here to protect your data with Security Scanner.
Security Scanner Warning Harmful software have been detected at your PC. Click here to deactivate it.
Security Scanner Warning Security Scanner has found viruses at your system. We highly recommend to get license for Security Scanner to remove harmful software now.
It takes over Internet Explorer to stop you browsing and prevent you from downloading any cleaning software. Usually with an on-screen warning saying that the site you are visiting is unsafe and has attempted to infect your computer.
This page under virus attack. This may crash your system. This may be caused by : Virus content founded at this site trying to install its components. Malicious & unknown network processes are determined. Your system is under virus attack Negative references from other citizens concerning this web page. Your system ports and backdoors have been checked by visited page for external access. Recommendations: Obtain a license of "Security Scanner" to protect your PC for the safest browsing Internet pages (desirable) Launch spyware, virus and malware scanning process. Keep browsing
As above, ignore this messaging. Security Scanner was created with the sole purpose of getting you to purchase the program. Do NOT purchase this program. If you have already paid them, contact your credit card company and cancel the charges. Inform them that the program is a computer infection and is trying to extort money and capture your card details.
Cause
Removal Instructions
We have to start by starting up in Safe Mode with Networking. Follow the appropriate guide for your version of Windows:
- How to boot into safe mode on Windows Vista and 7 on your Dell computer
- How to boot into Safe Mode on Windows 8 on your Dell Computer
- How to boot into Safe Mode on Windows 10
Eventually, you are brought to a menu similar to the example below.
Windows Advanced Options Menu Please select an option: Safe Mode Safe Mode with Networking Safe Mode with Command Prompt Enable Boot Logging Enable VGA Mode Last Known Good Configuration (your most recent settings that worked) Directory Services Restore Mode (Windows domain controllers only) Debugging Mode Disable automatic restart on system failure Start Windows Normally Reboot Use the up and down arrow keys to move the highlight to your choice.
Navigate using the cursor/arrow keys on your keyboard and select Safe Mode with Networking on-screen and press the Enter key on your keyboard.
Windows boots into safe mode with networking and prompts you to log in as a user. Log in as the user that is infected with the malware.
This Malware edits your Windows settings to use a proxy server. This stops you from browsing any pages on the Internet or updating your security software. Follow these instructions so that we can download the tools we must remove this infection.
You can either start Internet Explorer and select Internet Options from the Tools menu, or you can go to Control Panel and open it from there.
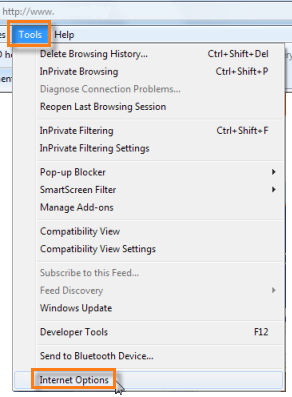
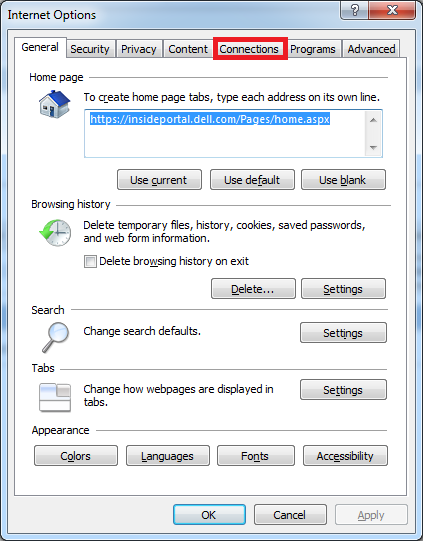
Click on the Connections tab.
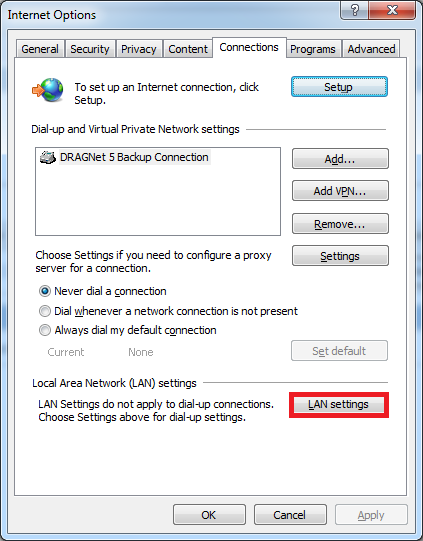
Click on the LAN Settings button.
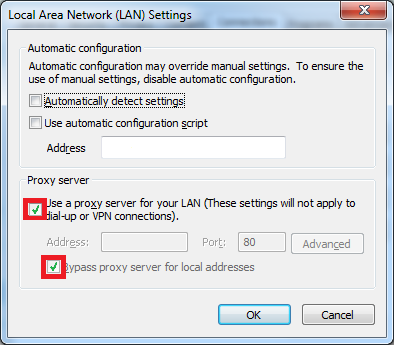
Clear the box labeled Use a proxy server for your LAN. Press the OK button to finalize your choice and close the window. Press OK again to close the Internet Options window. You should now be able to get online to download the removal tools.
The first step in actual removal is to end the processes that belong to the malware. In this case, I use RKill, as it is a program I am familiar with. You can use another program, but the steps below are for that program. You can download RKill to your desktop from the following link. (BleepingComputer developed RKill as Freeware and it is useful.)
You may want to download both the RKill and the iexplore.exe on another computer as some Malware recognizes RKill and tries to stop it running. Save them to your desktop using removable media.
Double-click on the RKill or iExplore.exe icon to automatically stop any processes associated with the Security Scanner and other Rogue programs. It may take a while for it to end them. When it is finished the black window closes. If you get any error messaging that RKill is an infection, ignore it. If any of these warnings close RKill, then it is best to leave the messaging on-screen and run RKill again. If you do not close the messaging, it cannot run again. Do not reboot your computer after running RKill as the malware is tied to your computer startup.
As before, Malwarebytes is another free program I am familiar with. You can use another program. The following steps are to download Malwarebytes Anti-Malware and save it to your desktop. It is a Freeware program.
Once downloaded, close all programs and Windows on your computer. (Including this browser.)
Double-click on the icon on your desktop to start the installation of Malwarebytes onto your computer.
Follow the setup prompts. Do not change any default settings. When the program has finished installation, ensure that you leave both the Update Malwarebytes Anti-Malware and Launch Malwarebytes Anti-Malware checked. Then click on the Finish button. If MalwareBytes asks you to reboot, ignore it.
Malwarebytes starts up, and you get an on-screen message saying that you should update the program before performing a scan. The program automatically updates itself after the installation completes, select the OK button to close that box and you are now at the main program window.
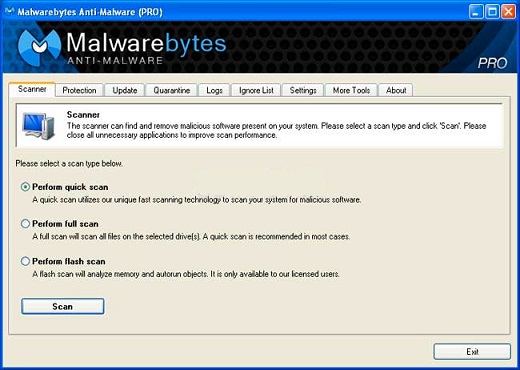
On the Scanner tab, ensure that the Perform quick scan option is selected and click on the Scan button to start scanning your computer.
The program starts scanning your computer for malware. This process should be quite a bit quicker than the full scan.

When the scan is complete, a finished message box appears.
Click on the OK button to close the message box and go to the removal process.
You go back at the main Scanner screen. Click on the Show Results button.
A window showing all the malware that the program found appears.
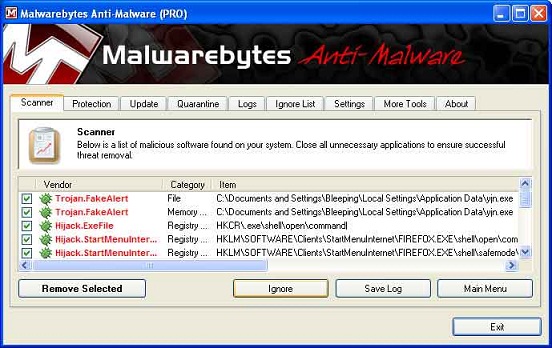
Click on the Remove Selected button to remove all the listed malware. All the files and registry keys are deleted and it adds them to the programs quarantine. While removing the files, Malwarebytes may require a reboot to remove some of them. If it displays a message stating that it must reboot, allow it to do so. After your computer has rebooted and you are logged in, go to the rest of the steps.
When Malwarebytes has finished removing the malware, it opens the scan log and displays it in Notepad. Review the log and then close the Notepad window. You can now exit the Malwarebytes program.
If the quick scan does not find anything, go back and select full scan. This can take a while to complete.
This particular malware also changes your Windows HOSTS file, we must put the default version for your operating system back onto the computer.
To protect itself, System Protection Tools changes the permissions of the HOSTS file so you cannot edit or delete it. I have added a link to a batch file that should resolve this. (The file like RKill is from BleepingComputer.)
Double-click on the hosts-perm.bat file to run it. (This is easier if you have downloaded it to your Desktop.) If you are asked if you are sure you want to run it, click allow. A small command prompt window opens and closes, this is supposed to happen. You could access your HOSTS file once this has run.
We must delete the C:\Windows\System32\Drivers\etc\HOSTS file. Once it has gone, follow the Microsoft Knowledge Base article below on resetting it to the default. The article covers Windows XP to Windows 8:
This takes your Windows HOSTS file back to default. Reboot your computer.
Resolution
Associated Security Scanner Files
Associated Security Scanner Files
- %LocalAppData%\<random characters>.exe
File Location Notes
- %LocalAppData%:
- Shows to the current users Local Settings Application Data folder, by default this is C:\Documents and Settings\<Current User>\Local Settings\Application Data for Windows 2000/XP and C:\Users\<Current User>\AppData\Local in Windows Vista, Windows 7, and Windows 8
Associated Security Scanner Registry Information
Associated Security Scanner Windows Registry Information
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "<random characters>
Prevent Re-Infection
To minimize the risk of a repeat infection, ensure that you have a real-time anti-virus program running on your computer and see that it stays updated. If you do not want to spend money on a paid service, then you can install one of the available free programs.
In addition to installing traditional anti-virus software, you might consider reading the guide below for some basic rules for safe surfing online:
Always double check any online accounts such as:
- Online banking
- Webmail
- Social networking sites
Virus scans must be run on the backup to confirm that it did not back up the infection if your files are automatically backed up. If virus scans are not possible such as online backups. You should delete your old backups and save new versions.
Keep your software current. Ensure that you update then frequently. If you receive any messages about this and are not sure of their validity, then always contact the company in question to clarify it.
 Get general information and guidance to secure your system/data on our Security and anti-virus page.
Get general information and guidance to secure your system/data on our Security and anti-virus page.Article Properties
Affected Product
Desktops & All-in-Ones, Laptops, Inspiron, Legacy Laptop Models, Fixed Workstations
Last Published Date
03 Oct 2023
Version
5
Article Type
Solution
