NetWorker: How To Set up AD/LDAP Authentication
Summary: This KB provides an overview for how to add external authority to NetWorker using the NetWorker Management Console's (NMC) external authority wizard. Active Directory (AD) or Linux LDAP authentication can be used alongside the default NetWorker Administrator account or other local NMC accounts. ...
Instructions
External Authority Resources can be created and managed from the NetWorker Management Console (NMC), NetWorker Web User Interface (NWUI), or AUTHC scripts:
- NetWorker Management Console (NMC): Log in to the NMC using the NetWorker Administrator account. Go to Setup->Users and Roles->External Authorities.
- NetWorker Web User interface (NMC): Log in to the NWUI using the NetWorker Administrator account. Go to Authentication Server->External Authorities.
Prerequisite:
External authentication (AD or LDAP) is integrated into the NetWorker authentication (AUTHC) server's database. It is not directly a part of the NMC or NWUI databases. In environments with a single NetWorker server, the NetWorker server is the AUTHC host. In environments with multiple NetWorker servers, managed through a single NMC, only one of the NetWorker servers is the AUTHC server. Determining the AUTHC host is required for the authc_mgmt commands used in later steps in this article. The AUTHC server is identified in the NetWorker Management Console (NMC) server's gstd.conf file:
- Linux:
/opt/lgtonmc/etc/gstd.conf - Windows (Default):
C:\Program Files\EMC NetWorker\Management\GST\etc\gstd.conf
NOTE: Thegstd.conffile contains a stringauthsvc_hostnamewhich defines the authentication server used to process login requests for the NetWorker Management Console (NMC).
Process:
Log in to the NetWorker Management Console (NMC) with the default NetWorker Administrator account. Under the Setup tab-->User and Roles, there is a new option for External Authority.

- To add a new authority, right click in the External Authority window and select New.
- In the External Authentication Authority box, you must populate the required fields with your AD/LDAP information.
- Check the "Show Advanced Options" box to see all the fields.
| Server Type | Select LDAP if the authentication server is a Linux/UNIX LDAP server, Active Directory if you are using a Microsoft Active Directory server. |
| Authority Name | Provide a name for this external authentication authority. This name can be whatever you want it to be, it is only to differentiate between other authorities when multiple are configured. |
| Provider Server Name | This field should contain the Fully Qualified Domain Name (FQDN) of your AD or LDAP server. |
| Tenant | Tenants can be used in environments where more than one authentication method may be used, or when multiple authorities must be configured. By default, the "default" tenant is selected. The use of tenants alters your log-in method. Log in to the NMC with "domain\user" for the default tenant, or "tenant\domain\user" for other tenants. |
| Domain | Specify your full domain name (excluding a hostname). Typically this is your base-Distinguished Name (DN) which is consisted of your Domain Component (DC) values of your domain. |
| Port Number | For LDAP and AD integration, use port 389. For LDAP over SSL, use port 636. These ports are non-NetWorker default ports on the AD/LDAP server.
NOTE: Changing the port to 636 is not sufficient for configuring SSL. The CA certificate (and chain, if a chain is used) must be imported from the domain server to the AUTHC server. See NetWorker: How to configure "AD over SSL" (LDAPS) from The NetWorker Web User Interface (NWUI).
|
| User DN | Specify the Distinguished Name  (DN) of a user account that has full read access to the LDAP or AD directory. (DN) of a user account that has full read access to the LDAP or AD directory.Specify the relative DN of the user account, or the full DN if overriding the value set in the Domain field. |
| User DN Password | Specify the password of the user account specified. |
| Group Object Class | The object class that identifies groups in the LDAP or AD hierarchy.
|
| Group Search Path | This field can be left blank in which case AUTHC is capable of querying the full domain. Permissions must be granted for NMC/ NetWorker server access before these users/groups can log in the NMC and manage the NetWorker server. Specify the relative path to the domain instead of full DN. |
| Group Name Attribute | The attribute that identifies the group name; for example, cn. |
| Group Member Attribute | Specifies the group membership of the user within a group.
|
| User Object Class | The object class that identifies the users in the LDAP or AD hierarchy. For example, inetOrgPerson or user |
| User Search Path | Like Group Search Path this field can be left blank in which case AUTHC is capable of querying the full domain. Specify the relative path to the domain instead of full DN. |
| User ID Attribute | The user ID that is associated with the user object in the LDAP or AD hierarchy.
|

- Once all the fields are populated, click OK to add the new authority.
- You can use the
authc_mgmtcommand on your NetWorker AUTHC server to confirm that the AD/LDAP groups/users are visible:
authc_mgmt -u Administrator -p 'NetWorker_Admin_Pass' -e query-ldap-users -D query-tenant=tenant_name -D query-domain=domain_name authc_mgmt -u Administrator -p 'NetWorker_Admin_Pass' -e query-ldap-groups -D query-tenant=tenant_name -D query-domain=domain_name authc_mgmt -u Administrator -p 'NetWorker_Admin_Pass' -e query-ldap-groups-for-user -D query-tenant=tenant_name -D query-domain=domain_name -D user-name=external_username
[root@nsr ~]# authc_mgmt -u Administrator -p '!Password1' -e query-ldap-users -D query-tenant=default -D query-domain=amer.lan The query returns 47 records. User Name Full Dn Name Administrator CN=Administrator,CN=Users,dc=amer,dc=lan ... bkupadmin CN=Backup Administrator,CN=Users,dc=amer,dc=lan [root@nsr ~]# authc_mgmt -u Administrator -p '!Password1' -e query-ldap-groups -D query-tenant=default -D query-domain=amer.lan The query returns 72 records. Group Name Full Dn Name Administrators CN=Administrators,CN=Builtin,dc=amer,dc=lan ... NetWorker_Admins CN=NetWorker_Admins,OU=Groups,dc=amer,dc=lan [root@nsr ~]# authc_mgmt -u Administrator -p '!Password1' -e query-ldap-groups-for-user -D query-tenant=default -D query-domain=amer.lan -D user-name=bkupadmin The query returns 1 records. Group Name Full Dn Name NetWorker_Admins CN=NetWorker_Admins,OU=Groups,dc=amer,dc=lan
-p" option. If you encounter this, remove "-p password" from the commands. You will be prompted to enter the password hidden after running the command.
- When logged into the NMC as the default NetWorker Administrator account, open Setup-->Users and Roles-->NMC Roles. Open the properties of the "Console Application Administrators" role and enter the Distinguished Name
(DN) of a AD/LDAP group (collected in step 5) in the external roles field. For users that require default NetWorker Administrator permissions, specify the AD/LDAP group DN in the "Console Security Administrators" role. For users /groups who do not need administrative rights to the NMC Console, add their full DN in the "Console User" - external roles.
- Access permissions must also be applied per NetWorker server configured in the NMC. This can be done one of two ways:
 (DN) of a AD/LDAP group (collected in step 5) in the external roles field. For users who require the same level permissions as the default NetWorker Administrator account, you must specify the AD/LDAP group DN in the "Security Administrators" role.
(DN) of a AD/LDAP group (collected in step 5) in the external roles field. For users who require the same level permissions as the default NetWorker Administrator account, you must specify the AD/LDAP group DN in the "Security Administrators" role.
NOTE: By default there is already the DN of the NetWorker server's LOCAL Administrators group, DO NOT delete this.
nsraddadmin command can be run from an administrator or root command prompt on the NetWorker server:
nsraddadmin -e "OU=group,CN=you,CN=want,CN=to,CN=add,DC=domain,DC=local"
nsraddadmin -e "CN=NetWorker_Admins,OU=Groups,dc=amer,dc=lan"
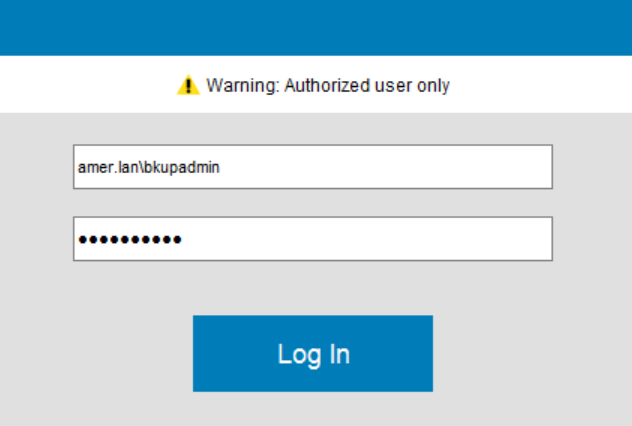
- Log in to the NMC using your AD/LDAP account (e.g: domain\user):
- (OPTIONAL) If you want an AD/LDAP group to be able to manage External Authorities, you must perform the following on the NetWorker server.
- Open an administrative/root command prompt.
- Using the AD group DN (collected in step 5) you want to grant
FULL_CONTROLpermission to run:
authc_config -u Administrator -p NetWorker_Admin_Pass -e add-permission -D permission-name=FULL_CONTROL -D permission-group-dn="AD/LDAP_group_dn"For Example
[root@nsr ~]# authc_config -u Administrator -p '!Password1' -e add-permission -D permission-name=FULL_CONTROL -D permission-group-dn="CN=NetWorker_Admins,OU=Groups,dc=amer,dc=lan" Permission FULL_CONTROL is created successfully. [root@nsr ~]# authc_config -u Administrator -p '!Password1' -e find-all-permissions The query returns 2 records. Permission Id Permission Name Group DN Pattern Group DN 1 FULL_CONTROL ^cn=Administrators,cn=Groups.*$ 2 FULL_CONTROL CN=NetWorker_Admins,OU=Groups,dc=amer... [root@nsr ~]#