Dell Automated Asset Discovery - Security and Compliance
Summary: An explanation of how Dell Automated Asset Discovery is maintaining the confidentiality of customer data.
Instructions
Overview
Dell Automated Asset Discovery* capability is committed to maintaining the availability, integrity and confidentiality of customer data. We’ve implemented robust processes and standards to secure customer data across all our platform operations, using:
-
Data Security
-
Product Security
-
Platform Security
Data Security
Dell Automated Asset Discovery follows strict practices for customer data that we manage and store in the platform. We encrypt all sensitive data, and each customer’s data is accessible only to authorized users of that tenant. Dell only captures and keeps data needed for IT operations management functions on devices/applications we manage.
Dell Automated Asset Discovery only collects data that helps us manage our customer’s IT environment, including:
-
Device Metadata. Like make, models, Serial Number
-
Events and SNMP Traps. We capture events and SNMP traps to understand device health.
Gateway Security
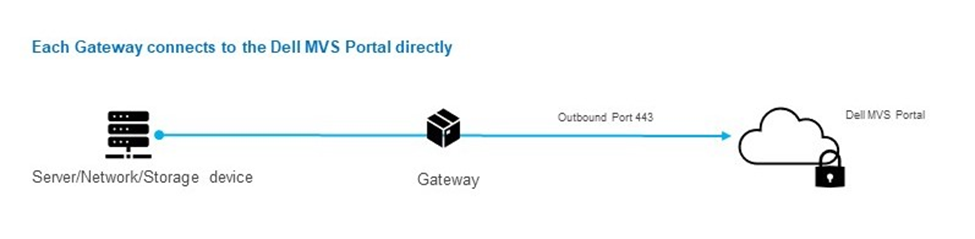
The Dell Automated Asset Discovery Gateway is a virtual appliance that monitors app services, network, and storage infrastructure.
Deployment Architectures
Telemetry data for computing (servers and applications) and non-compute infrastructure (network, storage, and virtual machines) is first sent to the Gateway. The Gateway then transmits this data to the Dell Automated Asset Discovery portal through secure channels
Product Security
Dell Automated Asset Discovery has broad security features for maintaining the privacy and security of customer data. We've designed the platform with security-first principles that integrate safety and reliability into day-to-day operations. We conduct quarterly due diligence audits to evaluate compliance with security policies through internal teams and third-party auditors.
Communication Security
Dell Automated Asset Discovery uses Gateways to collect relevant metrics on the health and performance of IT infrastructure. The data collected by Gateways is then sent to the Dell Automated Asset Discovery portal/cloud for processing and delivering the right operational insights.
All communication to the Dell Automated Asset Discovery cloud is encrypted by Transport Layer Security (TLS). We provide encryption for data in-flight and at rest. TLS encryption ensures that all network communications are secure without eavesdropping and tampering.
-
All data transmitted (in-flight mode) between the Dell Automated Asset Discovery Gateway and the Dell Automated Asset Discovery portal/cloud is encrypted using TLS 1.2.
Any data-at-rest mode in the Dell Automated Asset Discovery portal/cloud is similarly encrypted using AES-256 for enhanced data protection.
User Management
We grant user access to the Dell Automated Asset Discovery platform using fine-grained permissions built on role-based access controls (RBAC). RBAC lets you control how your users access, view, and manage data. Dell or Customers can assign roles to users based on their responsibilities. You can restrict the activities a user performs in Dell Automated Asset Discovery based on roles, and permissions and permissions.
Vulnerability Assessments
Our SaaS Operations teams conduct quarterly security audits to identify vulnerabilities and threats that can compromise platform security. As part of each audit, we assess existing processes, assess security infrastructure, and build the right controls. Critical issues identified during audits are immediately fixed. High and medium-severity issues which require code changes are prioritized for the next immediate platform release.
Platform Security
Dell Automated Asset Discovery leverages multiple layers of defense to provide a secure cloud platform to our customers. Our architecture, cloud operations, access, authentication, and deployment architecture guarantee the highest levels of security and protection.
Platform Availability
We've built the Dell Automated Asset Discovery platform for 99.90 % availability. The platform offers immediate and automatic failover when we lose connectivity to a primary data center. During an automatic failover, the platform routes traffic to the secondary data center using the BGP protocol for built-in disaster recovery, fault tolerance, and redundancy for seamless operations.
Platform Architecture
The Dell Automated Asset Discovery production environment is hosted in North America.
Platform Certifications
Dell Automated Asset Discovery* ensures continuous protection of customer data through compliance with leading industry standards and regulations:
-
SOC 2 Type II. Dell Automated Asset Discovery's data management and operational control practices are SOC 2 Type II certified. We have robust internal controls and rigorous processes in place to protect the confidentiality of customer data.
-
GDPR: Our platform instances hosted in Europe (London and Amsterdam) comply with GDPR regulations. Protecting personal privacy and security in line with applicable data protection laws is a commitment we take seriously at Dell Automated Asset Discovery.
The Dell Automated Asset Discovery* platform is hosted in Tier 1 data center providers (Equinix and Sungard), which hold the following certifications:
-
ISO 27001. Our platform operations have legal, physical, and technical controls from implementing, maintaining, and continually improving information security processes in accordance with ISO 27001 practices.
- SOC-1 Type I. Dell Automated Asset Discovery's information security practices, procedures, and operations meet the SOC 2 Type 1 standards for security, availability, and confidentiality.
* Powered by OpsRamp