Cyber Recovery: Henting av sertifikat mislyktes med TLS-protokollen
Summary: Når du har oppgradert til Cyber Recovery 19.17, finnes det et nytt alternativ for å kontrollere sertifikatet når du aktiverer TLS-protokollen (Transport Layer Security). Denne artikkelen dekker situasjoner der henting av sertifikatet mislyktes med TLS-protokollen. ...
Symptoms
Når du har oppgradert til Cyber Recovery 19.17, finnes det et nytt alternativ for å kontrollere sertifikatet når du aktiverer TLS-protokollen (Transport Layer Security). Når du kontrollerer sertifikatet, vises følgende feil i brukergrensesnittet for Cyber Recovery:
Mail server certificate is required when enabling TLS.
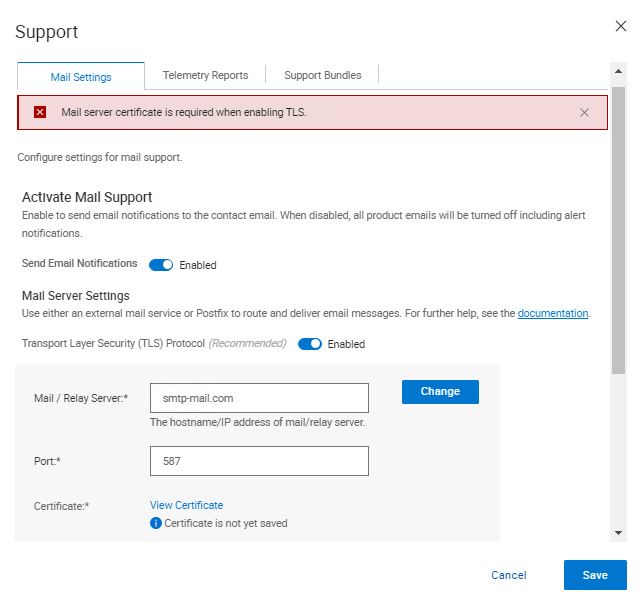
Cause
Følgende oppføringer skrives ut fra Cyber Recovery-loggene.
På crcli.log:
[2024-10-03 11:49:03.273] [DEBUG] [crcli] [restapi_client.go:384 HandleRESTAPIResponse()] : Entering
[2024-10-03 11:49:03.273] [DEBUG] [crcli] [restapi_client.go:392 HandleRESTAPIResponse()] : REST status code :500
[2024-10-03 11:49:03.273] [ERROR] [crcli] [restapi_client.go:401 HandleRESTAPIResponse()] : Failed to retrieve mail server certificate : Failed to connect to mail server: dial tcp: lookup smtp-mail.com: i/o timeout
[2024-10-03 11:49:03.273] [DEBUG] [crcli] [restapi_client.go:402 HandleRESTAPIResponse()] : Exiting
[2024-10-03 11:49:03.273] [ERROR] [crcli] [libcli.go:150 CliErrorExit()] : Failed to retrieve mail server certificate : Failed to connect to mail server: dial tcp: lookup smtp-mail.com: i/o timeoutPå edge.log:
[2024-10-03 11:48:53.268] [DEBUG] [edge] [restapi_client.go:200 callRestApi()] : Perform request.Post path=https://notifications:9096/irapi/v8/notifications/retrieveEmailCert
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:209 callRestApi()] : status = 500 Internal Server Error
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:410 GetCRResponse()] : Entering
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:417 GetCRResponse()] : Exiting
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:210 callRestApi()] : Exiting
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:116 CallCRRESTAPI()] : Exiting
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:57 CallRESTAPIHeader()] : Exiting
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:384 HandleRESTAPIResponse()] : Entering
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:392 HandleRESTAPIResponse()] : REST status code :500
[2024-10-03 11:49:03.272] [ERROR] [edge] [restapi_client.go:401 HandleRESTAPIResponse()] : Failed to connect to mail server: dial tcp: lookup smtp-mail.com: i/o timeout
[2024-10-03 11:49:03.272] [DEBUG] [edge] [restapi_client.go:402 HandleRESTAPIResponse()] : Exiting
[2024-10-03 11:49:03.272] [DEBUG] [edge] [jsonerr.go:27 JSONError()] : Entering
[2024-10-03 11:49:03.272] [ERROR] [edge] [jsonerr.go:40 JSONError()] : 500 : Failed to connect to mail server: dial tcp: lookup smtp-mail.com: i/o timeout
[2024-10-03 11:49:03.272] [DEBUG] [edge] [jsonerr.go:44 JSONError()] : Exiting
[2024-10-03 11:49:03.272] [DEBUG] [edge] [notifications.go:560 RetrieveEmailCert()] : Exiting
[2024-10-03 11:49:03.272] [INFO] [edge] [restauth.go:111 func1()] : POST /cr/v8/notifications/retrieveEmailCert End RetrieveEmailCert Elapsed=10.005125439sPå notifications.log:
[2024-10-03 11:48:53.270] [INFO] [notifications] [restauth.go:68 func1()] : POST /irapi/v8/notifications/retrieveEmailCert Start RetrieveEmailCert
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [restauth.go:210 validateToken()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [restauth.go:194 DecryptToken()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [encoding.go:48 DecodeString()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [encoding.go:56 DecodeString()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [crcrypto.go:558 DecryptCFB()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [crcrypto.go:579 DecryptCFB()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [encoding.go:48 DecodeString()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [encoding.go:56 DecodeString()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [crcrypto.go:112 GenHash()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [crcrypto.go:118 GenHash()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [restauth.go:206 DecryptToken()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [restauth.go:268 ValidateTokenTime()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [restauth.go:281 ValidateTokenTime()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [restauth.go:255 validateToken()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [notifications.go:283 RetrieveEmailCert()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [notifications.go:175 ValidateMailServer()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [notifications.go:201 ValidateMailServerURL()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [notifications.go:210 ValidateMailServerURL()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [notifications.go:215 ValidateMailServerPort()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [notifications.go:222 ValidateMailServerPort()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [notifications.go:196 ValidateMailServer()] : Exiting
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [email.go:227 RetrieveEmailCert()] : Entering
[2024-10-03 11:48:53.270] [DEBUG] [notifications] [email.go:272 GetTLSConn()] : Entering
[2024-10-03 11:49:03.271] [DEBUG] [notifications] [email.go:283 GetTLSConn()] : Exiting
[2024-10-03 11:49:03.272] [ERROR] [notifications] [email.go:235 RetrieveEmailCert()] : Failed to connect to mail server: dial tcp: lookup smtp-mail.com: i/o timeout
[2024-10-03 11:49:03.272] [DEBUG] [notifications] [email.go:236 RetrieveEmailCert()] : Exiting
[2024-10-03 11:49:03.272] [ERROR] [notifications] [notifications.go:321 RetrieveEmailCert()] : Failed to connect to mail server: dial tcp: lookup smtp-mail.com: i/o timeout
[2024-10-03 11:49:03.272] [DEBUG] [notifications] [jsonerr.go:27 JSONError()] : Entering
[2024-10-03 11:49:03.272] [ERROR] [notifications] [jsonerr.go:40 JSONError()] : 500 : Failed to connect to mail server: dial tcp: lookup smtp-mail.com: i/o timeout
[2024-10-03 11:49:03.272] [DEBUG] [notifications] [jsonerr.go:44 JSONError()] : Exiting
[2024-10-03 11:49:03.272] [DEBUG] [notifications] [notifications.go:323 RetrieveEmailCert()] : ExitingFra versjon 19.17 begynte Cyber Recovery å verifisere e-postserversertifikatet ved bruk av TLS.
I DNS-miljøer (Domain Name System) mislykkes inntasting av e-postserveren som et DNS-navn fordi Cyber Recovery ikke kan løse vertsnavnet til en IP-adresse på grunn av mangel på DNS i miljøet.
Når en IP-adresse brukes som felt for e-post-/videresendingsserver i CR og sertifikatet fra e-postserveren ikke har IP-adressen i sertifikatet, mislykkes bekreftelsen fordi sertifikatet verifiseres mot IP-en.
Det finnes et par løsninger for å få dette til å fungere:
- Legg til IP-adressen i sertifikatet du har fått av e-postserveren, slik at bekreftelsen kan fungere.
- Legge til oppføringen for e-postserver og IP i
/etc/hostsi varslingsbeholderen for å tillate at CR løser e-postserveren, og sertifikatverifisering kan forekomme.
Resolution
Det finnes to alternativer for å løse dette problemet:
- E-postserveren bruker et fullstendig kvalifisert domenenavn (FQDN), og Cyber Recovery får ikke sertifikatet.
- Kontroller at du bruker en DNS-server i hvelvmiljøet, og om den fungerer som den skal.
- Hvis det ikke er noen DNS-server i hvelvet, følger du trinnene nedenfor:
- Skriv inn SMTP-serverdetaljene (Simple Mail Transfer Protocol) i vertsfilene for varslingsdokkingstasjonen.
- Koble til Cyber Recovery ved hjelp av SSH.
- Kjør denne kommandoen:
docker exec -it cr_notifications_1 bash - Åpne filen med et tekstredigeringsprogram:
/etc/hosts - Legg til oppføringene for SMTP-serveren som IP, FQDN og kort navn.
- Lagre filen.
- Kjør denne kommandoen for å avslutte docker-beholderen:
exit
- Slik angir du oppføringen i
/etc/hostsGjør følgende vedvarende gjennom omstart:- Legge til en linje i
cr-install-path>/etc/docker-compose-prod-<current-version>.ymlfor IP-adressen du vil legge til/etc/hostsVarsler: - Den nye linjen uthevet i fet skrift, skal ha SMTP FQDN og deretter IP:
SMTP.server.com:xxx.xxx.xxx.xxx
build: .image: ${registryName}/cr_notifications:${notificationsVersion}container_name: cr_notifications_1security_opt:- no-new-privileges:truehostname: notificationsexpose:- "9096"depends_on:- postgresqlcap_drop:- ALLenvironment:- LD_LIBRARY_PATH=/cr/lockbox/lib- CRHOSTNAME=${dockerHostFQDN}- ENABLE_TLS=${enableTLS}- ENABLE_POSTFIX=${enablePostfix}- GODEBUG=tlskyber=0extra_hosts:- dockerbridge:${dockerBridge}- ${dockerHostFQDN}:${dockerHost}- SMTP.server.com:xxx.xxx.xxx.xxx - Kjør deretter
'crsetup.sh – forcerecreate'NÅR DET IKKE ER NOEN JOBBER SOM KJØRER.
- Legge til en linje i
- Skriv inn SMTP-serverdetaljene (Simple Mail Transfer Protocol) i vertsfilene for varslingsdokkingstasjonen.
- Hvis du bruker en IP-adresse for SMTP, henter ikke Cyber Recovery sertifikatet.
-
- I dette tilfellet må et nytt sertifikat genereres for å inneholde IP-adressen som brukes.
Eller
-
- Hvis sertifikatet ble opprettet ved hjelp av en FQDN, i stedet for å bruke IP-adressen til å koble til SMTP, bruker du FQDN i Cyber Recovery-grensesnittet.