Avamar: Unable to Add or Edit Data Domain Due to Cipher or Key-Exchange Missing
Summary: This article describes an issue when adding or editing Data Domain on an Avamar server and how to fix it.
Symptoms
Avamar User Interface (AUI) > Administration > System > Data Domain, the following error appears when adding or editing the Data Domain:
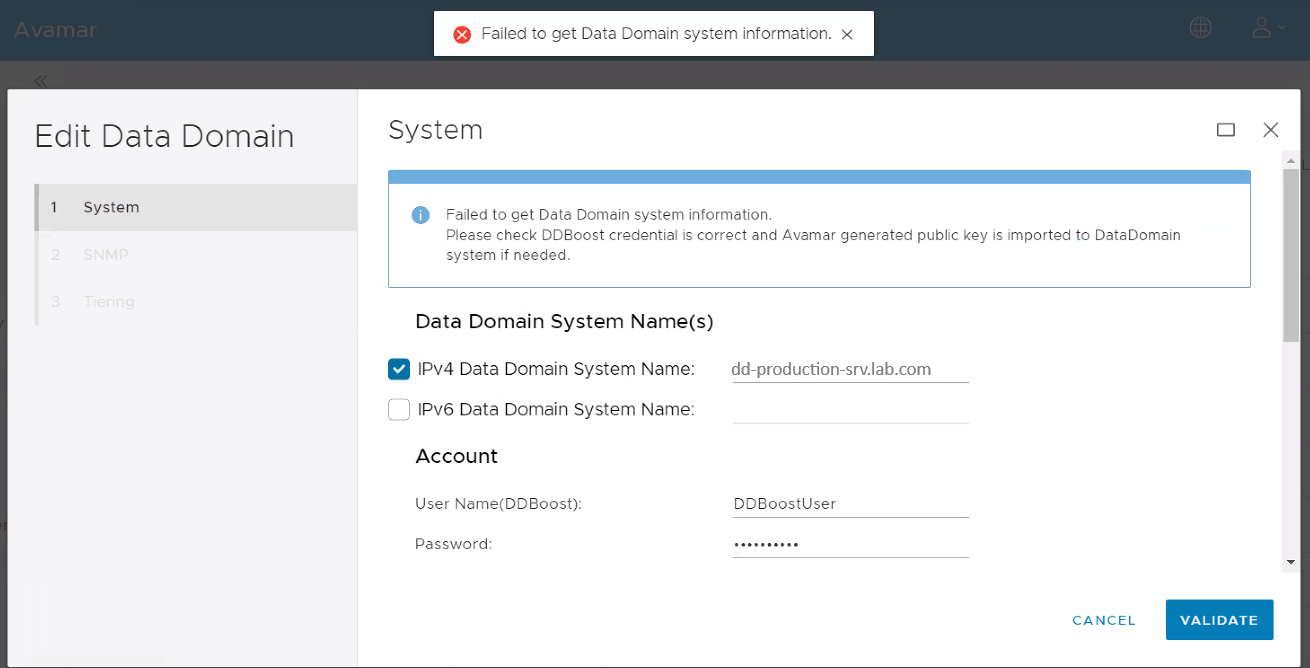
When the error occurs, the following error messages can be found on /usr/local/avamar/var/mc/server_log/mcserver.log.0:
Cipher issue:
WARNING: com.maverick.ssh.SshException: com.maverick.ssh.SshException at com.maverick.ssh.components.jce.client.DiffieHellmanGroupExchangeSha1.performClientExchange(DiffieHellmanGroupExchangeSha1.java:315) at com.maverick.ssh2.TransportProtocol.performKeyExchange(TransportProtocol.java:1424) at com.maverick.ssh2.TransportProtocol.processMessage(TransportProtocol.java:1821) at com.maverick.ssh2.TransportProtocol.startTransportProtocol(TransportProtocol.java:348) at com.maverick.ssh2.Ssh2Client.connect(Ssh2Client.java:122) at com.maverick.ssh.SshConnector.connect(SshConnector.java:646) at com.maverick.ssh.SshConnector.connect(SshConnector.java:481) at com.avamar.mc.datadomain.DdrSsh.createSshClient(DdrSsh.java:133) at com.avamar.mc.datadomain.DdrSsh.createSshClient(DdrSsh.java:185) at com.avamar.mc.datadomain.DdrSsh.validateCredentials(DdrSsh.java:272) at com.avamar.mc.datadomain.DataDomainService.validateCredentialSshConnection(DataDomainService.java:3668) at com.avamar.mc.datadomain.DataDomainService.validateDdrInfoAndGetDdrSystemInfo(DataDomainService.java:3766) at sun.reflect.GeneratedMethodAccessor171.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.lang.reflect.Method.invoke(Method.java:498) at org.springframework.aop.support.AopUtils.invokeJoinpointUsingReflection(AopUtils.java:318) at org.springframework.aop.framework.ReflectiveMethodInvocation.invokeJoinpoint(ReflectiveMethodInvocation.java:183) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:150) at org.springframework.security.access.intercept.aopalliance.MethodSecurityInterceptor.invoke(MethodSecurityInterceptor.java:61) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172) at org.springframework.aop.framework.JdkDynamicAopProxy.invoke(JdkDynamicAopProxy.java:202) at com.sun.proxy.$Proxy34.validateDdrInfoAndGetDdrSystemInfo(Unknown Source) at com.avamar.mc.datadomain.DataDomainServiceContext.validateDdrInfoAndGetDdrSystemInfo(DataDomainServiceContext.java:245) at sun.reflect.GeneratedMethodAccessor170.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.lang.reflect.Method.invoke(Method.java:498) at sun.rmi.server.UnicastServerRef.dispatch(UnicastServerRef.java:357) at sun.rmi.transport.Transport$1.run(Transport.java:200) at sun.rmi.transport.Transport$1.run(Transport.java:197)
Or
Key-exchange issue:
WARNING: com.maverick.ssh.SshException: Failed to negotiate a transport component [aes128-ctr,aes192-ctr,aes256-ctr,blowfish-cbc,aes128-cbc,aes192-cbc,aes256-cbc,arcfour,arcfour128,arcfour256] [chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com] [Unknown cause] at com.maverick.ssh2.TransportProtocol.selectNegotiatedComponent(TransportProtocol.java:1896) at com.maverick.ssh2.TransportProtocol.performKeyExchange(TransportProtocol.java:1277) at com.maverick.ssh2.TransportProtocol.processMessage(TransportProtocol.java:1821) at com.maverick.ssh2.TransportProtocol.startTransportProtocol(TransportProtocol.java:348) at com.maverick.ssh2.Ssh2Client.connect(Ssh2Client.java:122) at com.maverick.ssh.SshConnector.connect(SshConnector.java:646) at com.maverick.ssh.SshConnector.connect(SshConnector.java:481) at com.avamar.mc.datadomain.DdrSsh.createSshClient(DdrSsh.java:133) at com.avamar.mc.datadomain.DdrSsh.createSshClient(DdrSsh.java:185) at com.avamar.mc.datadomain.DdrSsh.validateCredentials(DdrSsh.java:272) at com.avamar.mc.datadomain.DataDomainService.validateCredentialSshConnection(DataDomainService.java:3668) at com.avamar.mc.datadomain.DataDomainService._updateDdr(DataDomainService.java:1182) at com.avamar.mc.datadomain.DataDomainService.updateDdr(DataDomainService.java:1036) at sun.reflect.GeneratedMethodAccessor411.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source) at java.lang.reflect.Method.invoke(Unknown Source) at org.springframework.aop.support.AopUtils.invokeJoinpointUsingReflection(AopUtils.java:318) at org.springframework.aop.framework.ReflectiveMethodInvocation.invokeJoinpoint(ReflectiveMethodInvocation.java:183) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:150) at org.springframework.security.access.intercept.aopalliance.MethodSecurityInterceptor.invoke(MethodSecurityInterceptor.java:61) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172) at org.springframework.aop.framework.JdkDynamicAopProxy.invoke(JdkDynamicAopProxy.java:202) at com.sun.proxy.$Proxy34.updateDdr(Unknown Source) at com.avamar.mc.datadomain.DataDomainServiceContext.updateDdr(DataDomainServiceContext.java:223) at sun.reflect.GeneratedMethodAccessor410.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source) at java.lang.reflect.Method.invoke(Unknown Source) at sun.rmi.server.UnicastServerRef.dispatch(Unknown Source) at sun.rmi.transport.Transport$1.run(Unknown Source)
Check the /ddr/var/log/debug/messages.engineering log file on the Data Domain server.
From the Avamar server, run as admin:
ssh -i ~/.ssh/ddr_key <ddboost_user>@<data-domain-IP-FQDN>
admin@av-server:~/>: ssh -i ~/.ssh/ddr_key DDBoostUser@dd-production-srv EMC Data Domain Virtual Edition Last login: Wed Mar 12 08:31:03 CDT 2025 from 192.168.1.113 on pts/0 Welcome to Data Domain OS 7.13.0.20-1082704 ------------------------------------------- DDBoostUser@dd-production-srv#
Use the following command to view the messages.engineering log file:
log view debug/messages.engineering
The following messages can be seen:
Cypher issue:
Unable to negotiate with 192.168.1.113 port 53036: no matching cipher found. Their offer: aes128-ctr,aes192-ctr,aes256-ctr,blowfish-cbc,aes128-cbc,aes192-cbc,aes256-cbc,arcfour,arcfour128,arcfour256 [preauth]
Key-exchange issue:
Unable to negotiate with 192.168.1.113 port 43998: no matching host key type found. Their offer: ssh-dss,ssh-rsa,x509v3-sign-rsa,x509v3-sign-dss,x509v3-sign-rsa-sha1,x509v3-ssh-rsa,x509v3-ssh-dss,x509v3-ecdsa-sha2-nistp256,x509v3-ecdsa-sha2-nistp384,x509v3-ecdsa-sha2-nistp521,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,x509v3-rsa2048-sha256 [preauth]
For cipher issue, the following test can be performed. From Avamar, run as root:
ssh -i <ddboost_user>@<data-domain-IP-FQDN> -c <cipher>
Example of error using ciphers:
root@av-server:/#: ssh DDBoostUser@dd-production-srv.lab.com -c aes128-ctr Unable to negotiate with 10.127.92.183 port 22: no matching cipher found. Their offer: chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com root@av-server:/#: root@av-server:/#: ssh DDBoostUser@dd-production-srv.lab.com -c aes192-ctr Unable to negotiate with 10.127.92.183 port 22: no matching cipher found. Their offer: chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com root@av-server:/#: root@av-server:/#: ssh DDBoostUser@dd-production-srv.lab.com -c aes256-ctr Unable to negotiate with 10.127.92.183 port 22: no matching cipher found. Their offer: chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com root@av-server:/#:
Cause
Resolution
Open a Service Request with the Avamar SCR Team to get this resolved.
For Support Team, check the Internal Notes section for resolution.