PowerEdge: How to Prepare TPM Enabled VMware ESXi Host for Hardware Changes to Avoid PSOD
Summary: If ESXi hosts use Trusted Platform Module (TPM), this article provides steps to take while the ESXi host is still accessible over SSH before any hardware changes.
This article applies to
This article does not apply to
This article is not tied to any specific product.
Not all product versions are identified in this article.
Instructions
Symptoms:
After performing hardware maintenance, including replacing components (for example, CMOS battery, CPU, so on), you may experience Purple Screen (PSOD) errors when booting the host backup.

Root Cause:
Starting from version 7.0u2, ESXi uses TPM 2.0 to protect system configurations through "TPM sealing." The configuration can only be accessed with the same TPM chip used initially.
To prevent this, it is necessary to gather the recovery key from TPM Security-Enabled hosts before performing the replacement.
Instructions:
- SSH into the ESXi host
- Verify if TPM is installed and "TPM Security" is enabled in the BIOS:
[root@host1:~] esxcli hardware trustedboot get Drtm Enabled: true Tpm Present: true
- Get the Recovery Key by running the command below:
esxcli system settings encryption recovery list
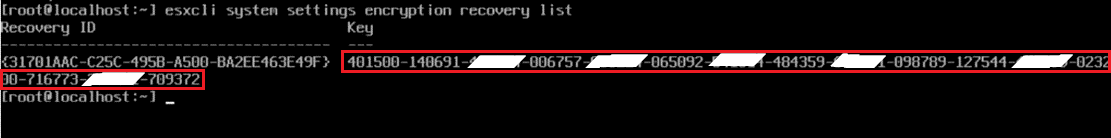
Note: The recovery key is the second set of numbers shown: 16 groups, each containing six digits, as highlighted above
- Ensure saving the recovery key somewhere secure for future use.
Note: If the recovery key is not available, the only option is to reinstall ESXi.
At this stage, safely replace the part and if you had the PSOD previously, follow the below steps to resolve the issue.
Steps:
- Reboot the ESXi and then press SHIFT+O when prompted:

- Append the boot configuration with the following from the recovery key gathered from Pre-requisites:
encryptionRecoveryKey=######-######-######-######-######-######-######-######-######-######-######-######-######
Note: Do not remove the information which is already present at the beginning of the prompt.
At the end of the existing bootUUID, add a space followed by the encryptionRecoveryKey information as shown in the above screenshot.
- Press Enter to continue the host boot process.
- SSH to the host and run the command below to Write changes to disk:
[root@host1:~] /sbin/auto-backup.sh
Affected Products
C Series, Modular Infrastructure, Rack Servers, Tower Servers, XE Servers, XR Servers, OEM Server Solutions, VMware ESXi 7.x, VMware ESXi 8.x, VMware ESXi 9.xArticle Properties
Article Number: 000318876
Article Type: How To
Last Modified: 03 Sep 2025
Version: 2
Find answers to your questions from other Dell users
Support Services
Check if your device is covered by Support Services.