For IT security teams, managing and prioritizing the endless list of known enterprise systems vulnerabilities can seem like a hopeless game of Whack-a-Mole. Just when one problem is knocked down, another one invariably pops up somewhere else. The real risk, however, comes in the form of not knowing which ‘mole’ to ‘whack’ now and which to address later.
RSA has the answer in the form of a new solution released today at RSA Conference 2013. The new RSA Vulnerability Risk Management blends a powerful mix of Big Data, analytics and the RSA Archer GRC platform to help bring order and sanity to patch management.
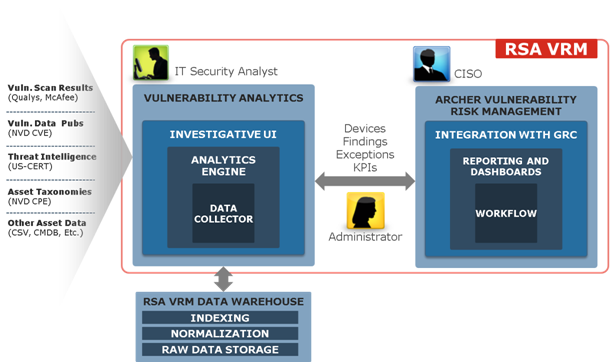
RSA Vulnerability Risk Manager, or VRM, sports the following features:
1. A Big Data-powered warehouse to collect, normalize and combine data from vulnerability scans, threat feeds and vendor alerts.
2. Vulnerability Analytics used to explore, mine, and model vulnerability data which can help IT security analysts find valuable meaning and context and, thus, determine the relative severity of certain vulnerabilities over others.
3. The RSA Archer GRC platform, which provides workflow, tracking, and key performance indicators to ensure that the vulnerability management program is running smoothly; analysts no longer have to hope on blind faith that they’re working on addressing the most important patches.
Let’s talk VRM in action… Take, for example, an IT security analyst facing the problem of too much security data without enough context. Not anymore: VRM provides the big data analytics dashboard to start their day focused on what is most important, with less worry about the lower priority security patches until the severe ones are fixed. They can customize their dashboard to monitor issues that are overdue; can track new assets discovered with critical business context (i.e. patches needed in finance applications or servers); and track vulnerabilities that are due to be fixed in the next seven days. VRM helps keep things in control!
IT administrators are happy because they get a prioritized list of patches that need applying with a clear understanding of which assets are owned by whom and their business criticality. And everyone is better off when administrators can better meet their SLAs.
Metrics for the security organization are also available in real time. The CISO likes this a lot because he or she no longer needs to run for cover when they are asked for the latest security status. CISOs can dust off their proactive wish list and confidently give security posture updates and make decisions with data-driven inputs, powered by the RSA Archer GRC platform.
The vulnerability Whack-A-Mole is a constant game the IT security team plays, but is certainly made a lot easier thanks to VRM. It takes the guessing out of which mole the security team should whack next.