This blog is co-authored by Jen Larson, Director, Large Enterprise and Government, Commercial Client, Intel.
BIOS security tops the list of questions Dell and Intel field from customers. This isn’t surprising since BIOS and other firmware have been identified as growing attack vectors in recent years. And because of our focus on reducing the attack surface in hardware, Dell and Intel are working together to protect BIOS through a variety of innovative, “built-in” security features.
BIOS security relates to the hardware and firmware protections built into a device. This includes things like BIOS verification, resilience and downgrade protection. These features not only prevent attacks, but they also kick into gear in the face of an attack and give IT and security teams the visibility and insight they need to act when questionable activity is detected within the fleet.
Cyber criminals can gain access to the BIOS from many different points of entry. An attack can happen through direct physical access to the device or even through a simple email – which, according to a 2022 FBI Internet Crime Report, resulted in adjusted losses of over $2.7 billion in the United States. Plus, without adequate protection, including not knowing what is happening with BIOS in your fleet, your organization could potentially miss a breach. And being unaware is a truly terrifying place to be.
How Dell Helps Customers Protect the BIOS
To protect this critical layer, Dell commercial devices ship with SafeBIOS, a collection of capabilities that help prevent BIOS attacks, detect potential compromise and respond by alerting IT if irregularities are found. Dell integrates post-boot BIOS verification into its commercial PCs* – OptiPlex, Latitude and Precision – giving IT the ability to verify the health of BIOS across the fleet. Rather than storing BIOS information on the hardware itself, which leaves it susceptible to corruption, SafeBIOS instead delivers these capabilities off-host. This feature, unique to Dell, uses a secure cloud environment to compare an individual BIOS image against the “known good” copy.
Dell SafeBIOS also automates the early detection of BIOS events and high-risk actions with Indicators of Attack, another feature exclusive to Dell. We designed the continuous extraction and analysis of changes in BIOS configurations and events to surface vulnerable endpoints for remediation before the fleet is infected.
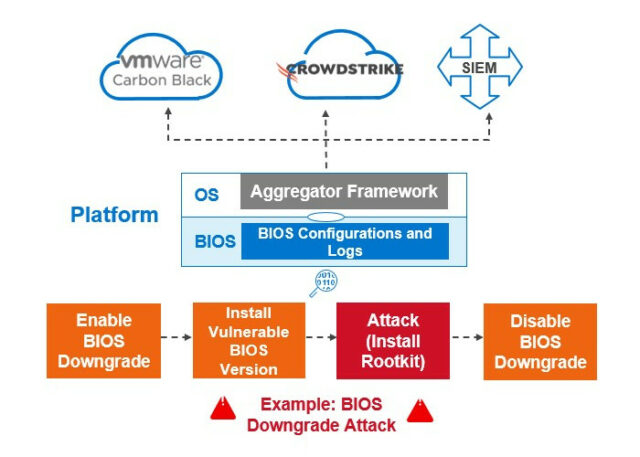
Dell SafeBIOS brings visibility and control to system hardware operating “below” the operating system (OS), an area where IT administrators have previously had little to no oversight.
What Intel Brings to the Mix
Dell and Intel’s focus on hardware-based security has yielded a comprehensive silicon-based solution for business PC security. These capabilities include:
-
- Intel vPro with Intel Hardware Shield. Every Dell commercial device running on the Intel vPro® platform includes Intel Hardware Shield, which delivers foundational hardware security through innovative security technologies that help protect all layers in the computing stack. Dell harnesses these capabilities to provide customers with the industry’s most secure commercial PCs.*
- Intel BIOS Guard. Intel BIOS Guard reduces the risk of flash-backed attacks on the BIOS by hardening the agent that can update the flash. It helps ensure resilience by eliminating software surfaces and attackable surfaces that could write and erase the flash, making the platform more secure.
- Intel Boot Guard. Intel Boot Guard is designed to protect critical system boot functions. It provides a tamper-resistant, hardware-based root of trust that serves as an effective detection mechanism to verify the integrity of the earliest and most critical system BIOS code executed by the processor.
How Dell and Intel’s Hardware-based Security Stands Out
As one attack surface hardens, attackers turn to softer targets. Today, those new vectors include the below-the-OS layers and the supply chain. To stay ahead of bad actors, having built-in, hardware-based security embedded across your fleet helps establish device trust and protect your organization against these foundational attacks. Dell and Intel are here to help.
Our joint expertise and co-engineering relationship enable us to help organizations combat particularly persistent and malicious attacks with protections for every layer of the compute stack. Read our white paper to learn how Dell and Intel work together to secure the workspace. As always, reach out to your Dell account rep or contact us here for more information.
*The industry’s most secure commercial PCs: Based on Dell internal analysis, Sept. 2022. Not all features are available with all PCs. Additional purchase required for some features.