Avamar: How to manager Session Security with the Avinstaller Installation Package (AVP)
Summary: This article explains how to manage the Avamar Session Security settings by using the Avinstaller installation package (AVP).
Instructions
1. Download Session Security AVP:
a. Go to the Dell product support link
b. Log in to view the downloads.
For example, select the appropriate Avamar version:
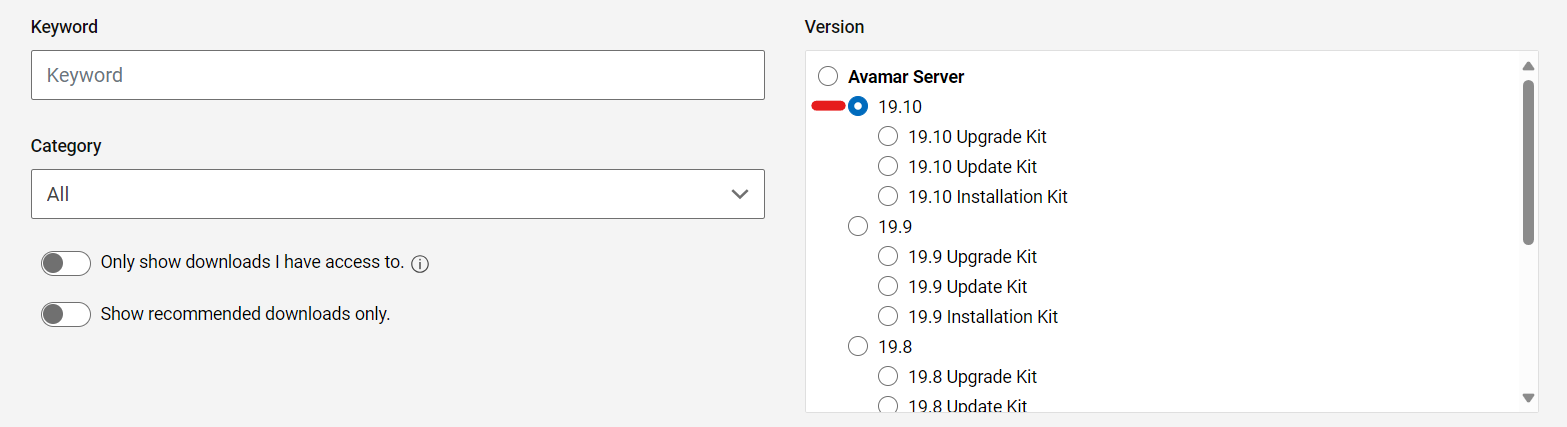
Search for the Avamar Session Security Configuration workflow package:

2. Prior to installation:
-
Stop all backups, replication, and ensure that no maintenance is running (checkpoint, checkpoint validation (
hfscheck), and garbage collection). -
Check that there is a valid checkpoint.
3. Upload the Session Security AVP to the package repository:
Once the appropriate Session Security configuration package is downloaded, there are two options for installation:
Option 1:
a. Upload the package to a temporary directory such as /home/admin on the Avamar Utility Node.
b. Move the package to the directory /data01/avamar/repo/packages:
mv <package-name> /data01/avamar/repo/packages/
The AVinstaller service detects changes to the directory and automatically starts loading the package into the package repository.
Option 2:
a. Open the AVinstaller web service page:
https://<avamar_server_ip_or_hostname>/avi
b. Go to the Repository section:


The package processes:
Once it is ready, the status is "Accepted":
4. Install Session Security AVP:
a. If the package was not uploaded using the AVinstaller, open the AVinstaller web service page:
https://<avamar_server_ip_or_hostname>/avi
b. Go to the "Maintenance" tab to run the package.
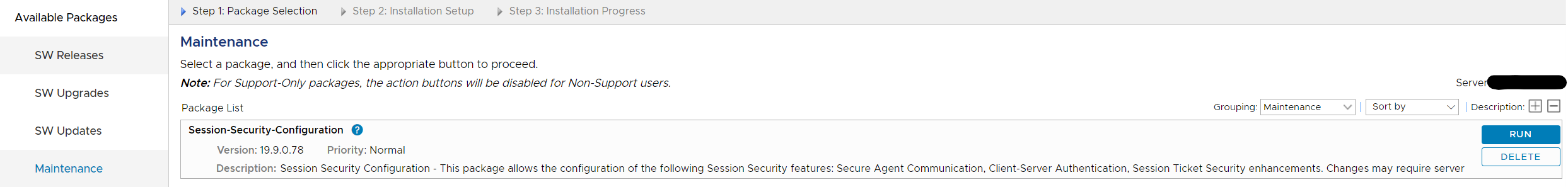
c. Select Run.
d. On the "Installation Setup" screen, select the Security Settings tab and check the "Show advanced settings" checkbox.

Manage Session Security Settings:
Generate Certificates:
-
-
- Generate Server Certificates Only:
- When selected alone, only regenerates the
GSANserver certificates.- The description on the screen states "Creates and propagates server certificates on the Avamar server and storage nodes, to be used for server and/or client authentication using the
CA certificateinstalled in the keystore."
- The description on the screen states "Creates and propagates server certificates on the Avamar server and storage nodes, to be used for server and/or client authentication using the
- This performs the following actions on the Avamar grid:
- Runs the
enable_secure_config.shscript (enable_secure_config.sh --certs), which does the following:- Exports the Avamar internal root certificate from the Avamar keystore:
- Runs the
- When selected alone, only regenerates the
- Generate Server Certificates Only:
-
keytool -export -rfc -keystore /usr/local/avamar/lib/avamar_keystore -alias mcrsaroot
-
-
-
-
-
- Saves this root certificate to the following two locations:
-
-
-
-
/home/admin/chain.pem
/usr/local/avamar/etc/chain.pem
-
-
-
-
-
- The root certificate in the avamar_keystore is then used to sign a new certificate keypair for the
GSAN, and saved to the following locations:
- The root certificate in the avamar_keystore is then used to sign a new certificate keypair for the
-
-
-
-
mcrootca rsatls <nodename> <subject_alt_names>
/home/admin/key.pem
/home/admin/cert.pem
/usr/local/avamar/etc/key.pem
/usr/local/avamar/etc/cert.pem
-
-
-
-
-
- These certificates are then propagated to any storage nodes.
- Lastly, the
GSAN SSL socketis reloaded so new connections to port 29000 to serve the regenerated certificates.
-
-
-
-
-
-
- Generate All New Certificates
- When this checkbox is selected, it automatically also selects the "Generate Server Certificates Only" checkbox as well.
This is because of the process which occurs when generating all new certificates.- The description on the screen states: "Re-creates
mcrootcaand generates all new root,TLS, and EC root certificates."
- The description on the screen states: "Re-creates
- This performs the following actions:
- Regenerate the Avamar internal root certificate authority (CA)
mcrootca all(This replaces the Avamar internal root CA stored in the avamar_keystore
/usr/local/avamar/lib/avamar_keystore) - Regenerates the
GSANcertificates as described in the previous "Generate Server Certificates Only" section.
- When this checkbox is selected, it automatically also selects the "Generate Server Certificates Only" checkbox as well.
- Generate All New Certificates
-
The Avamar internal root certificate can be viewed with the following command:
keytool -list -v -keystore /usr/local/avamar/lib/avamar_keystore -alias mcrsaroot
root CA and a signed certificate from the Avamar MCS allowing secure mutual TLS communication with Avamar.
See the following for more information: Avamar: Install or Replace Avamar Certificate Authority (CA) with User Supplied Certificate Authority (CA)
e. When ready, continue to run the package.
The package can be used multiple times to configure these settings as required.