Solution Builder Extensions for Azure Local - Integrated System AX and MC Server Release Notes
Summary: This article provides information about Solution Builder Extensions (SBEs) for Azure Local. SBEs allow updates to Firmware, Driver, and Windows Defender Application Control (WDAC) supplemental policies for Azure Local clusters running on Dell AX and MC servers. ...
This article applies to
This article does not apply to
This article is not tied to any specific product.
Not all product versions are identified in this article.
Instructions
All SBE update information for AX and MC have been moved to the Support Matrix | Solutions for Microsoft Azure.
Each subsequent release will be added under that build's version, as seen in the below example.
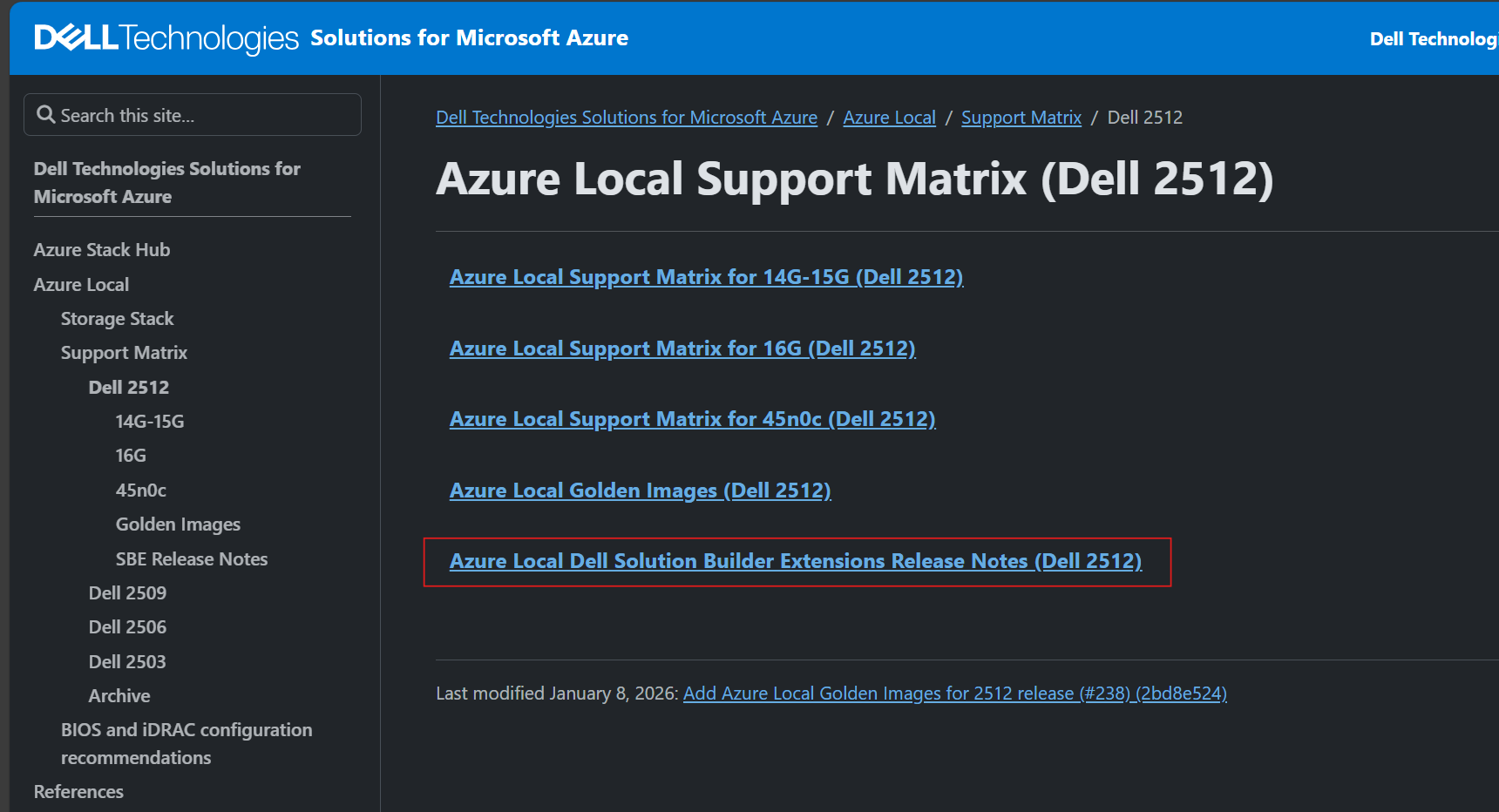
Figure 1: Azure Local support matrix page for version 2512
Affected Products
AX Nodes, AX-4510C, AX-4520C, ax-650, AX-6515, AX-660, AX-750, AX-7525, AX-760Article Properties
Article Number: 000224407
Article Type: How To
Last Modified: 08 Jan 2026
Version: 54
Find answers to your questions from other Dell users
Support Services
Check if your device is covered by Support Services.