Data Domain: How to Enable Encryption Over the Wire and File Replication Encryption
Summary: For environments that are not using a VPN for secure connections between sites, Data Domain Replicator software can securely encapsulate its replication payload over SSL with AES 256-bit encryption for secure transmission. This process is also known as encrypting data in flight. You can encrypt the data replication stream by enabling the Data Domain Boost file replication encryption option. ...
Instructions
For environments that do not use a VPN for secure connections between sites, Data Domain (DD) Replicator software can securely encapsulate its replication payload over SSL with AES 256-bit encryption for secure transmission. This process is also known as encrypting data in flight.
Encryption of data in flight
DD Replicator software encrypts data being transferred between two Data Domains. This is known as encryption of data in flight. It uses OpenSSL AES 256-bit encryption to encapsulate the replicated data over the wire. The encryption encapsulation layer is immediately removed when it lands on the destination Data Domain. DD encryption software can also encrypt data within the payload.
Enable Encryption Over Wire (MTree Replication)
DD Replicator supports encryption of data-in-flight with TLS protocol version 1.1. When replication authentication-mode is set to one-way or two-way, Ephemeral Diffie-Hellman (DHE) is used for session key exchange. Server authentication happens over RSA. The AES 256-bit Galois Counter Mode (GCM) cipher encapsulates the replicated data over the wire. The encryption encapsulation layer is immediately removed as it lands on the destination DD. SHA384 is used for hash Message Authentication Code.
One-way indicates that only the destination certificate is verified. Two-way indicates that both the source and destination certificates are verified. Mutual trust MUST be established before you can use the authentication-mode option, and both sides of the connection must enable this feature for encryption to proceed.
When the replication authentication mode is set to anonymous, Anonymous Diffie-Hellman (ADH) is used for session key exchanges, but the source and destination do not authenticate each other before the key exchange. If the authentication mode is not specified, anonymous is the default value.
NOTE: On DDOS 8.x, TLS 1.2 is used when enabling over-the-wire encryption and DDBoost file-replication encryption.
1) If using one-way or two-way authentication for replication, you MUST exchange CA certificates:
a) Check current trusts:
adminaccess trust show
b) Add trusts to configure mutual trust.
adminaccess trust add host <hostname> type mutual
2) DDSH via CLI(Command Line interface). one-way or two-way cannot be configured via GUI at this time.
Run on both source and target DD. Configuring on target first is recommended.
Also note that replication CTX numbers can be different on source and target DDs.
a) must disable replication prior to making modifications.
replication disable <destination>
example:
replication disable rctx://1
b) enable encryption over the wire with or without authentication-mode.
replication modify <destination> encryption {enabled | disabled}
[authentication-mode {one-way | two-way | anonymous}]
example:
replication modify rctx://1 encryption enabled authentication-mode two-way
3) Verify changes made:
replication show config
example:
replication show config
CTX Source Destination Connection Low-bw-optim Crepl-gc-bw-optim Encryption Enabled Max-repl- Tenant-unit
Host and Port (Auth-mode) streams
--- ------------------------------------------------------- ---------------------------------------------------- ----------------------------------- ------------ ----------------- ----------------- ------- --------- -----------
1 mtree://DD3300.MyCompany.com/data/col1/mtree1 mtree://DDVE.MyCompany.com/data/col1/mtree1_repl DDVE.MyCompany.com (default) disabled disabled enabled (two-way) no 8 -
4) Enable replication on both DDs. Enable on target first is recommended.
Also note that replication CTX numbers can be different on source and target DDs.
replication enable <destination>
example:
replication enable rctx://1
Replication modifies destination encryption {enabled | disabled}. (UI only allows for anonymous authentication.)
Modify the state of encryption over wire for the destination. This feature is active only when enabled on both the source and the destination. The Role required is admin or limited-admin.
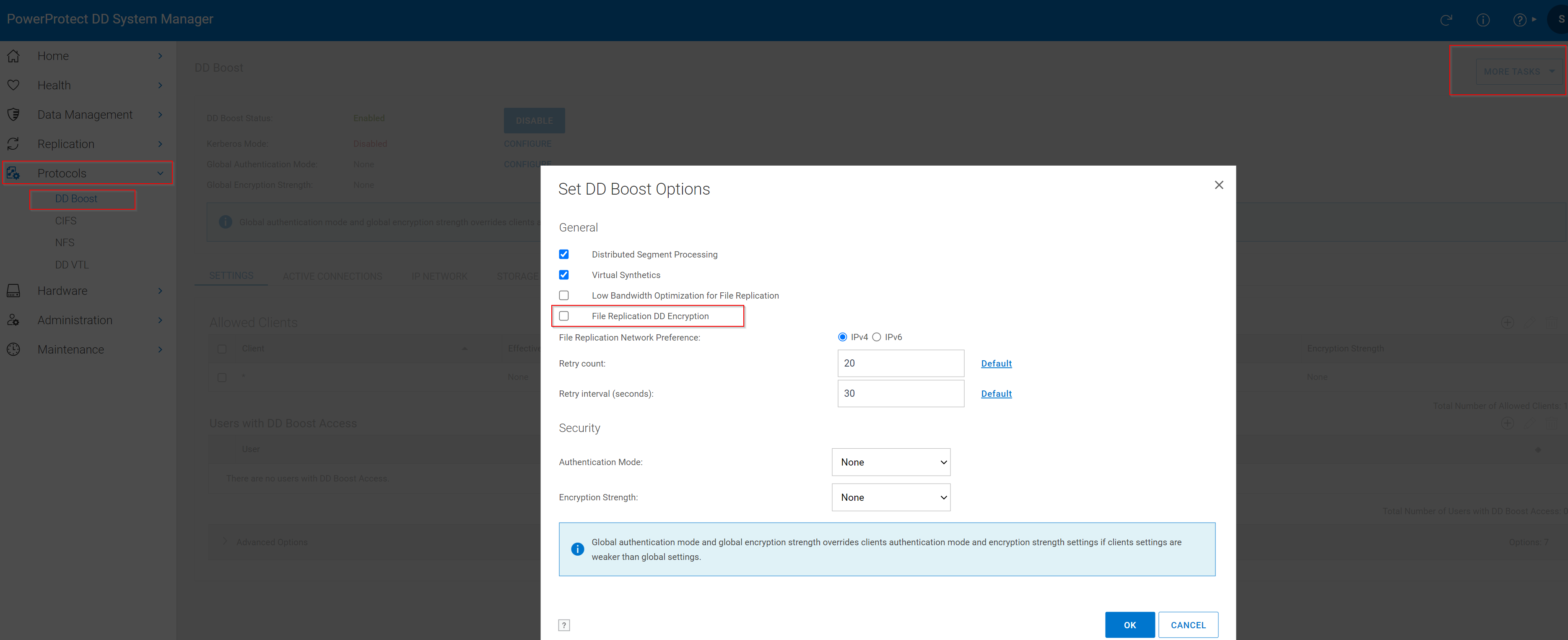
File replication encryption (MFR: Managed File Replication using DD Boost)
You can encrypt the data replication stream by enabling the DD Boost file replication encryption option.
ddboost file-replication option set encryption {enabled [authentication-mode {one-way |
two-way | anonymous}] | disabled}
Enable or disable encrypted data transfer for DD Boost file-replication. This command must be entered on both systems—the
source system and the destination (target) system.
The authentication-mode parameter is optional. If encryption is enabled, the default authentication mode is anonymous.
One-way and two-way authentication require the configuration of mutual trust on both the source and destination systems. Run
the adminaccess trust add host <hostname> [type mutual] command to configure mutual trust.
ddboost file-replication option show [encryption] Show state of encryption: enabled or disabled. Role required: admin, limited-admin, security, user, or backup-operator.
Additional Information
Question: Can the DD Encryption be enabled concurrently with the over-the-wire encryption feature in the DD Replication software option?
Answer: Yes, both over the wire encryption and Data at Rest Encryption (DARE) can be enabled concurrently to achieve different security goals.
Question: What happens if both the DD Encryption software option and the over-the-wire encryption feature in the DD Replication software option are enabled concurrently?
Answer: The first source encrypts data using destination encryption key; then already encrypted data encrypted a second time because of over the wire encryption while sending this data to its destination. At the destination after over the wire decryption is done, data will be stored in an encrypted format which was encrypted using destination's encryption key.
Question: What type of encryption algorithm is used for Data Domain's "encryption over the wire" feature, to regard encrypting the replication traffic?
Answer: When replication authentication-mode is set to "one-way" or "two-way," Ephemeral Diffie-Hellman (DHE) is used for session key exchange. Server authentication happens by RSA. AES 256-bit GCM cipher is used to encapsulate the replicated data over the wire.
The encryption encapsulation layer is immediately removed when it lands on the destination system. One way indicates that only the destination certificate is certified. Two way indicates that both the source and destination certificates are verified. Mutual trust must be established before you can use authentication-mode and both sides of the connection must enable this feature for encryption to proceed.
When replication authentication-mode is set to "anonymous," Anonymous Diffie-Hellman (ADH) is used for session key exchange, but in this case, source and destination do not authenticate each other before the key exchange. Also, if the authentication-mode is not specified, anonymous is used as the default.
Question: Is over the wire encryption supported in the EDP (encryption disablement project) system?
Answer: We cannot enable Data at Rest Encryption (DARE) or over the wire encryption (with replication or with ddboost) in EDP system.