By David Linthicum, Cloud Analyst, Gigaom Research
The rise of cloud computing has led to the rethinking of how cloud, and non-cloud systems, approach security. Considering the complex and distributed nature of cloud-based platforms, security approaches that leverage identity seem to be the best fit. This is a fundamental shift in thinking, and in technology.
Developers are finding that they have to work well with security systems, considering the rise of cloud computing, and the adoption of DevOps. In the cloud, security becomes systemic to the platform, as well as to the application. Developers need to focus on the best practices and technologies that drive security in the cloud.
Identity and Access Management (IAM) approaches and solutions are increasing in popularity. However, the movement to identity-based solutions is not as easy as many technology providers describe. There is much for developers to learn, and more to change.
While it’s pretty easy to build new approaches to security in new applications that reside on the cloud, the more difficult aspect of IAM is to extend this security model to the traditional enterprise. Security should be consistent and systemic, which is lacking in most traditional enterprise applications. The security problem needs to be considered by developers right now, before a move to the cloud.
It’s all IAM
IAM is clearly a superior security model and best practice, considering the emerging use of cloud computing, and it’s a technology that will be most beneficial for developer requirements. Indeed, many cloud providers provide IAM as a service right out of the cloud.
The IAM concept is simple: Provide a security approach and technology that enables the right individuals to access the right resources, at the right times, for the right reasons. IAM follows the principles that everything and everyone gets an identity. This includes humans, servers, APIs, applications, data, etc. Once that verification occurs, it’s just a matter of defining which identities can access other identities, and creating policies that define the limits of that relationship.
An example of IAM for developers would be to define and store the identity of a set of cloud-based Application Programming Interfaces (APIs) that are only to be leveraged by a single set of IoT (Internet of Things) devices, let’s say, thermostats. The APIs each have an identity, as do the devices, applications and the humans using the devices. They have to authenticate each other’s identity before they are granted access, or grant access. Each checks with the IAM each time they interact with another resource, such as in the example of an application running on a device, linking to and invoking an API.
An IAM provides much more control. In our simple example above, you could remove access to any resources by simply de-authorizing the relationship, using their identities and credentials as a way of determining who and what they are. Moreover, you can also set access policies, such as time of day, even geographical locations, as ways of limiting access around certain high-risk situations to better protect the assets that the IAM is securing.
New Security Model for Developers
We focused on IAM as we moved to more distributed and heterogeneous systems, which is exactly what cloud-based platforms are. Moreover, as security and compliance issues begin to become the number one priority, the investment in IAM is being made both within the enterprise, and certainly within the emerging using of public and private cloud-based systems.
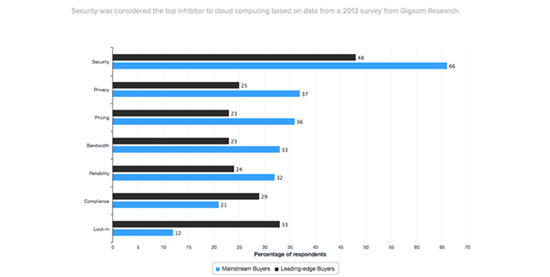
As you can see in Figure 1, in a 2013 Gigaom survey, security is often cited as the number one reason why enterprises are not moving to the cloud.
Figure 1: Security is consistently cited as the number 1 reason why the enterprise is not moving to the cloud.[1]
While technology is not always the answer, the use of IAM could bring those who are on the fence around to the use of public clouds. In many instances, data is actually more secure in the cloud, when the right security models are leveraged. Indeed, according to Alert Logic’s Fall 2012 State of the Cloud Security Report, the variations in the threat activity are not as important as where the infrastructure is located.
The report further finds that Web application-based attacks hit both service provider environments (53 percent of organizations) and on-premises environments (44 percent of organizations). However, on-premises environment users or customers actually suffer more incidents than those of service provider environments. On-premises environment users experienced an average of 61.4 attacks, while service provider environment customers averaged only 27.8. On-premises environment users also suffered significantly more brute force attacks compared to their counterparts.
What is unique about IAM is that it’s important as a business driver, as well as a security technology. Those who deploy IAM, including developers, need to focus on the core business processes, as well as the details around security. This is a shift from recent days, when security was more of a “geeky” concept, and the business drivers were largely unconsidered. The focus on making security an application, versus a platform-level issues, draws developers in as well.
Developers who build mature IAM capabilities into their systems can reduce their identity management costs and, more importantly, become significantly more agile in supporting new business initiatives. When security is built into the development processes, and not an afterthought, resulting applications provide more security and functionality. What’s more, developers feel that they are empowered to make the security calls that they need, without having to rely on an outside security organization.
It seems easy to predict that IAM will be part of more than 50 percent of the existing applications that migrate to the pubic cloud. What might be more surprising to some is that it will be part of almost 90 percent of new applications built on clouds.[2] Will you be ready?
This post was written as part of the Dell Insight Partners program, which provides news and analysis about the evolving world of tech. Dell sponsored this article, but the opinions are my own and don’t necessarily represent Dell’s positions or strategies.
[1] http://research.gigaom.com/chart/inhibitors-to-adoption-of-cloud/
[2] Gigaom, David S. Linthicum