PowerProtect - SQL discovery fails with ASD0002 or ASDS0018 error
Summary: PowerProtect Data Manager SQL discovery fails with ASD0002 or ASDS0018 error.
This article applies to
This article does not apply to
This article is not tied to any specific product.
Not all product versions are identified in this article.
Symptoms
Within PPDM, when attempting to run a discovery of a Microsoft SQL Server asset, the discovery may fail with the following errors:
In the DPSApps\AgentService\logs\OpAgentSvc* log, the following error is logged:
ADA0002: Unable to discover ASSETS on host <Server SQL Name> because of an agent issue.
Unable to perform applications discovery because agent failed to create the discovery session.
Or
ASDS0018: Discovery of Assets failed on the host <SQL Server Name> for AddOn MICROSOFT_SQL_DATABASE_SYSTEM.
In the DPSApps\AgentService\logs\OpAgentSvc* log, the following error is logged:
ErrCode: -2147467259, Error: SSL Provider: The certificate chain was issued by an authority that is not trusted.
In the System event logs on the SQL server, one or more of the following errors may be logged:
System Event Logs:
Log Name: System
Source: Schannel
Date: <DATE>
Event ID: 36882
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: <SQL Server Name>
Description:
The certificate received from the remote server was issued by an untrusted certificate authority. Because of this, none of the data contained in the certificate can be validated. The SSL connection request has failed. The attached data contains the server certificate.
Log Name: System
Source: Schannel
Date: <DATE>
Event ID: 36884
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: <SQL Server Name>
Description:
The certificate received from the remote server does not contain the expected name. It is therefore not possible to determine whether we are connecting to the correct server. The server name we were expecting is crcorpsqldev02. The TLS connection request has failed. The attached data contains the server certificate.
Log Name: System
Source: Schannel
Date: <DATE>
Event ID: 36888
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: <SQL Server Name>
Description:
A fatal alert was generated and sent to the remote endpoint. This may result in termination of the connection. The TLS protocol defined fatal error code is 48. The Windows SChannel error state is 552.
Cause
The failure is caused because "Force protocol encryption" is enabled on the SQL Native Client configuration under SQL Server Configuration Manager.
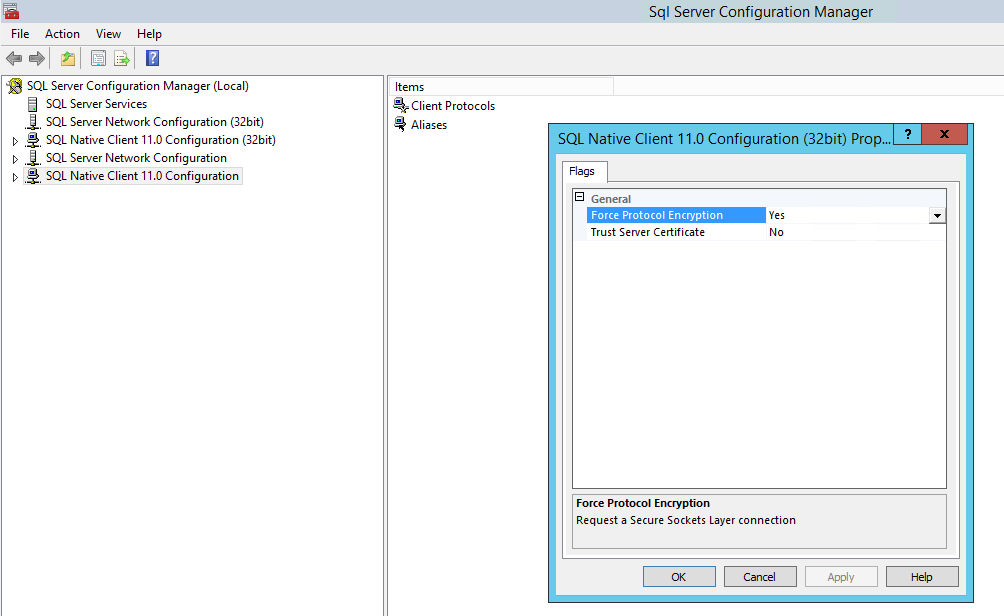
Resolution
To resolve the issue, follow the steps below:
- Open the SQL Server Configuration Manager
- Right click on SQL Native Client 11.0 Configuration and select properties.
- Set the Force Protocol Encryption value to No and select OK.
- Perform the same steps for the SQL Native Client 11.0 Configuration (32 bit) configuration
- Reboot the SQL Server
- Once the SQL server is up and running, run Discovery from the PPDM UI.
Sometimes, it may be necessary to unregister or uninstall the Agent and reinstall for discovery to work.
Affected Products
PowerProtect Data ManagerArticle Properties
Article Number: 000214332
Article Type: Solution
Last Modified: 22 Sep 2023
Version: 2
Find answers to your questions from other Dell users
Support Services
Check if your device is covered by Support Services.