Connectrix: Brocade: How to import the LDAP certificate to the switch through CLI
Summary: This article explains the steps involved generating CSR, export the CSR file and import LDAP certificate through switch CLI.
This article applies to
This article does not apply to
This article is not tied to any specific product.
Not all product versions are identified in this article.
Instructions
1. To list the available certificates on the switch, use the command.
3. Export the CSR file from the switch use the following command. Verify that the FTP client is ready for transfer.
4. Import the CA (root and intermediate) bundled certificate.
5. Next import the bundled certificate under the server role and use the same file as on Step 4.
6. Import the switch/client certificate that is exported in the previous step and signed by certificate administrator.
>seccertmgmt show --all
Switch_1:FID128:admin> seccertmgmt show -all
ssh private key:
Does not Exist
ssh public keys available for users:
None
Certificate Files:
--------------------------------------------------------------------------------------------------------------------
Protocol Client CA Server CA SW CSR PVT Key Passphrase
--------------------------------------------------------------------------------------------------------------------
FCAP Empty NA Empty Empty Empty Empty
RADIUS Empty Empty Empty Empty Empty NA
LDAP Empty Empty Empty Empty Exist NA
SYSLOG Empty Empty Empty Exist Exist NA
HTTPS NA Exist Exist Exist Exist NA
KAFKA NA Empty NA NA NA NA
ASC NA Empty NA NA NA NA
2. Create the Certificate Signing Request (.csr) use:
>seccertmgmt generate -csr ldapFile name created should end with a .csr extension.
3. Export the CSR file from the switch use the following command. Verify that the FTP client is ready for transfer.
>seccertmgmt export -csr ldap -protocol ftpHave the CSR file signed by your certificate administrator.
4. Import the CA (root and intermediate) bundled certificate.
seccertmgmt import -ca -client ldap
Switch_1:admin> seccertmgmt import -ca -client ldap
Select protocol [ftp or scp]: ftp
Enter IP address: 10.xx.xx.xx
Enter remote directory: /CSR/LDAP
Enter certificate name (must have ".crt" or ".cer" or ".pem" suffix):chain.pem
Enter Login Name: _v800503
Enter Password:
Success: imported ldap client CA certificate [chain.pem].
5. Next import the bundled certificate under the server role and use the same file as on Step 4.
seccertmgmt import -ca -server ldap
Switch_1:FID128:admin> seccertmgmt import -ca -server ldap
Select protocol [ftp or scp]: ftp
Enter IP address: 10.xx.xx.xx
Enter remote directory: /CSR/LDAP
Enter certificate name (must have ".crt" or ".cer" or ".pem" suffix):chain.pem
Enter Login Name: _v800503
Enter Password:
Success: imported ldap server CA certificate [chain.pem].
6. Import the switch/client certificate that is exported in the previous step and signed by certificate administrator.
>seccertmgmt import -cert ldap
Switch_1:FID128:admin> seccertmgmtis import -cert ldap
Select protocol [ftp or scp]: ftp
Enter IP address: 10.xx.xx.xx
Enter remote directory: /CSR/LDAP
Enter certificate name (must have ".crt" or ".cer" or ".pem" suffix):FCS50.pem
Enter Login Name: _v800503
Enter Password:
Success: imported ldap switch certificate [FCS50.pem].
Switch_1:FID128:admin> seccertmgmt show -all
ssh private key:
Does not Exist
ssh public keys available for users:
None
Certificate Files:
--------------------------------------------------------------------------------------------------------------------
Protocol Client CA Server CA SW CSR PVT Key Passphrase
--------------------------------------------------------------------------------------------------------------------
FCAP Empty NA Empty Empty Empty Empty
RADIUS Empty Empty Empty Empty Empty NA
LDAP Exist Exist Exist Exist Exist NA
SYSLOG Empty Empty Empty Exist Exist NA
HTTPS NA Exist Exist Exist Exist NA
KAFKA NA Empty NA NA NA NA
ASC NA Empty NA NA NA NAAdditional Information
Follow the below steps to chain a root, sub, and intermediate certificate into a bundle:
1. Download the certificate which could be in .p7b format. Extract the file and double-click to open it with the Windows certificate manager.
Example:
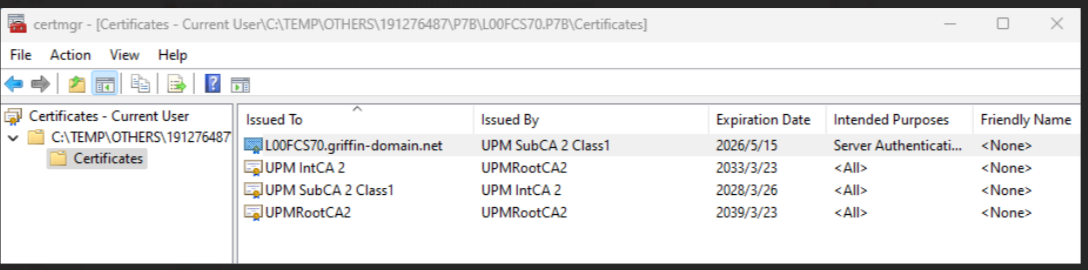
2. For the sub/int/root, right click, all tasks, export, and save as base-64 encoded one by one and save the files into .pem format.
Open a notepad and copy the content from sub/int/root and combine/chain a file into one, sub first, then int and root the last, save as PEM and change to UNIX EOL.
Example: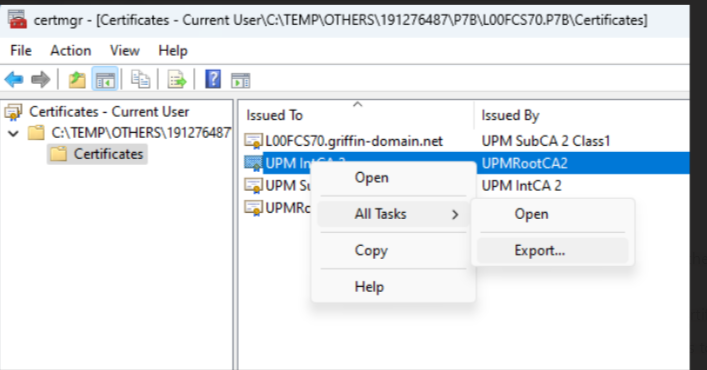
Affected Products
Connectrix B-SeriesProducts
Connectrix B-Series Fabric OS 9.X, Connectrix B-Series HardwareArticle Properties
Article Number: 000226132
Article Type: How To
Last Modified: 20 Jun 2024
Version: 1
Find answers to your questions from other Dell users
Support Services
Check if your device is covered by Support Services.