NVP vProxy: FLR Data Protection Restore Client returns "Unable to get clients"
Summary: The Data Protection Restore Client (DPRC) is used to perform a VMware Virtual Machine (VM) File Level Restore (FLR). A Microsoft Active Directory (AD) or Linux Lightweight Directory Access Protocol (LDAP) user is used to authenticate the DPRC. After logging in, an error appears stating "Unable to get clients, Non admin user for unknown client requesting client info." ...
Symptoms
- NetWorker is integrated with external authorities (Microsoft Active Directory or Linux LDAP Server).
- After accessing the DPRC using an external authority account, the following message appears.
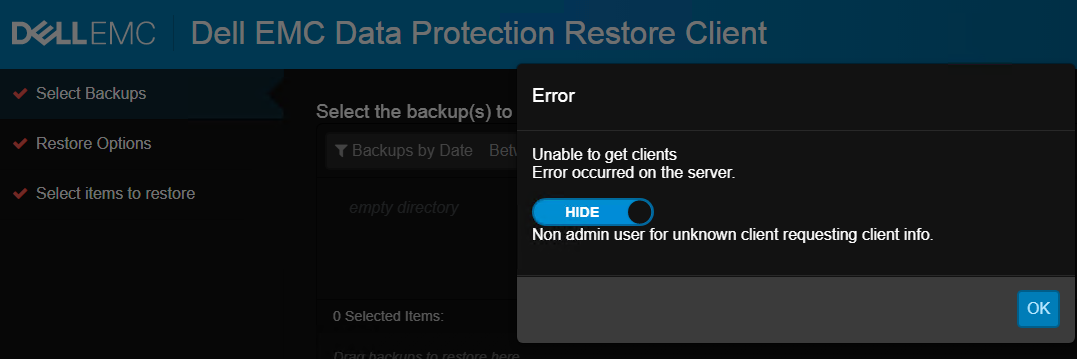
Cause
The user who is used for accessing the Dell EMC Data Protection Restore Client e is not a member of the VMware FLR Users NetWorker User group.
Resolution
1. Log in to the NetWorker Management Console (NMC) with an administrative account. For example, the default NetWorker Administrator account.
2. From the NMC, connect to the NetWorker server.
3. Go to the Server tab and click User Groups from the left menu.
4. Right-click the VMware FLR Users user group and open the properties.
5. Add the Distinguished Name 
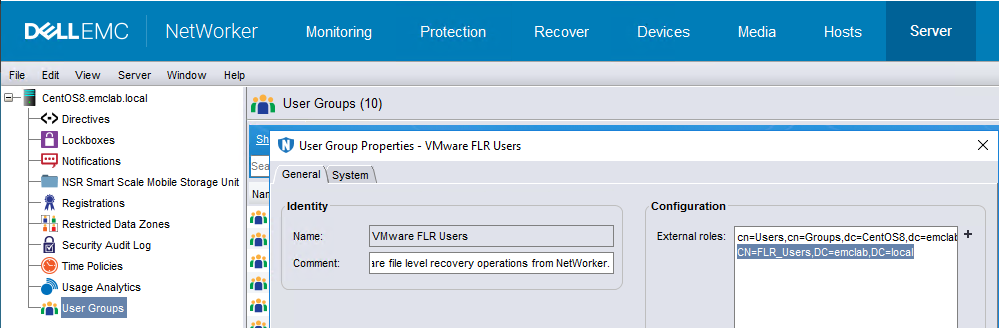
7. Select User and enter the external authority (AD or LDAP) user credentials.
You should be presented with the available backups for the VM.
NOTE: VM File Level Recoveries can be performed from the NMC, NetWorker Web User Interface (NWUI), and command-line on the NetWorker server.
Additional Information
The following methods can be used to help determine the AD/LDAP group a user belongs to. The Distinguished Name (DN) returned can be used in the VMware FLR Users external roles field.
Windows Powershell:
From a windows system on the same domain, run the following Powershell command:
Get-ADPrincipalGroupMembership -Identity USERNAME
Example:
PS C:\Users\Administrator.EMCLAB> Get-ADPrincipalGroupMembership -Identity flradmin ... ... distinguishedName : CN=FLR_Users,DC=emclab,DC=local GroupCategory : Security GroupScope : Global name : FLR_Users objectClass : group objectGUID : 058495c7-71c7-42c6-be92-2d8f96a5c2aa SamAccountName : FLR_Users SID : S-1-5-21-4085282181-485696706-820049737-1104
The distinguishedName outputted by the command could be used in NetWorker to grant the AD user access to the NMC.
For more information about this command, see: https://docs.microsoft.com/en-us/powershell/module/activedirectory/get-adprincipalgroupmembership?view=windowsserver2022-ps
NetWorker authc_mgmt Command:
You can use the authc_mgmt command to query AD/LDAP user/group membership. On the NetWorker server, open a command prompt (or SSH session) and run the following command syntax:
authc_mgmt -u Administrator -e query-ldap-groups-for-user -D query-tenant=TENANT_NAME -D query-domain=DOMAIN_NAME -D user-name=USER_NAME
PS C:\> authc_mgmt -u Administrator -e query-ldap-groups-for-user -D query-tenant=default -D query-domain=emclab.local -D user-name=flradmin Enter password: The query returns 1 records. Group Name Full Dn Name FLR_USERS CN=FLR_Users,dc=emclab,dc=local
The Full Dn Name of one of the groups can be used to grant this AD user access to the NMC.
The configuration and values that are needed for authc_mgmt commands can be collected by running:
authc_config -u Administrator -e find-all-configs authc_config -u Administrator -e find-config -D config-id=CONFIG_ID authc_config -u Administrator -e find-all-tenants
The following article provides additional information regarding external authentication integration with NetWorker: